How the west created the Islamic Stateby Nafeez Ahmed
Sep 11, 2014
NOTICE: THIS WORK MAY BE PROTECTED BY COPYRIGHTYOU ARE REQUIRED TO READ
THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.
… with a little help from our friends
Part 1 – OUR TERRORISTS“This is an organisation that has an apocalyptic, end-of-days strategic vision which will eventually have to be defeated,” Gen Martin Dempsey, chairman of the US Joint Chiefs of Staff, told a Pentagon press conference in August.
Military action is necessary to halt the spread of the ISIS/IS “cancer,” said President Obama. Yesterday, in his much anticipated address, he called for expanded airstrikes across Iraq and Syria, and new measures to arm and train Iraqi and Kurdish ground forces.
“The only way to defeat [IS] is to stand firm and to send a very straightforward message,” declared Prime Minister Cameron. “A country like ours will not be cowed by these barbaric killers.”
Missing from the chorus of outrage, however, has been any acknowledgement of the integral role of covert US and British regional military intelligence strategy in empowering and even directly sponsoring the very same virulent Islamist militants in Iraq, Syria and beyond, that went on to break away from al-Qaeda and form ‘ISIS’, the Islamic State of Iraq and Syria, or now simply, the Islamic State (IS).
Since 2003, Anglo-American power has secretly and openly coordinated direct and indirect support for Islamist terrorist groups linked to al-Qaeda across the Middle East and North Africa. This ill-conceived patchwork geostrategy is a legacy of the persistent influence of neoconservative ideology, motivated by longstanding but often contradictory ambitions to dominate regional oil resources, defend an expansionist Israel, and in pursuit of these, re-draw the map of the Middle East.
Now despite Pentagon denials that there will be boots on the ground – and Obama’s insistence that this would not be another “Iraq war” – local Kurdish military and intelligence sources confirm that US and German special operations forces are already “on the ground here. They are helping to support us in the attack.” US airstrikes on ISIS positions and arms supplies to the Kurds have also been accompanied by British RAF reconnaissance flights over the region and UK weapons shipments to Kurdish peshmerga forces.
Divide and rule in Iraq“It’s not that we don’t want the Salafis to throw bombs,” said one US government defense consultant in 2007. “It’s who they throw them at – Hezbollah, Moqtada al-Sadr, Iran, and at the Syrians, if they continue to work with Hezbollah and Iran.”
Early during the 2003 invasion and occupation of Iraq, the US covertly supplied arms to al-Qaeda affiliated insurgents even while ostensibly supporting an emerging Shi’a-dominated administration.
Pakistani defense sources interviewed by Asia Times in February 2005 confirmed that insurgents described as “former Ba’ath party” loyalists – who were being recruited and trained by “al-Qaeda in Iraq” under the leadership of the late Abu Musab Zarqawi – were being supplied Pakistan-manufactured weapons by the US. The arms shipments included rifles, rocket-propelled grenade launchers, ammunition, rockets and other light weaponry. These arms “could not be destined for the Iraqi security forces because US arms would be given to them”, a source told Syed Saleem Shahzad – the Times’ Pakistan bureau chief who, “known for his exposes of the Pakistani military” according to the New Yorker, was murdered in 2011. Rather, the US is playing a double-game to “head off” the threat of a “Shi’ite clergy-driven religious movement,” said the Pakistani defense source.
This was not the only way US strategy aided the rise of Zarqawi, a bin Laden mentee and brainchild of the extremist ideology that would later spawn ‘ISIS.’
 The JSOC insignia
The JSOC insigniaAccording to a little-known November report for the US Joint Special Operations University (JSOU) and Strategic Studies Department, Dividing Our Enemies, post-invasion Iraq was “an interesting case study of fanning discontent among enemies, leading to ‘red-against-red’ [enemy-against-enemy] firefights.”
While counterinsurgency on the one hand requires US forces to “ameliorate harsh or deprived living conditions of the indigenous populations” to publicly win local hearts and minds:
“… the reverse side of this coin is one less discussed. It involves no effort to win over those caught in the crossfire of insurgent and counterinsurgent warfare, whether by bullet or broadcast. On the contrary, this underside of the counterinsurgency coin is calculated to exploit or create divisions among adversaries for the purpose of fomenting enemy-on-enemy deadly encounters.”
In other words, US forces will pursue public legitimacy through conventional social welfare while simultaneously delegitimising local enemies by escalating intra-insurgent violence, knowing full-well that doing so will in turn escalate the number of innocent civilians “caught in the crossfire.” The idea is that violence covertly calibrated by US special operations will not only weaken enemies through in-fighting but turn the population against them.
In this case, the ‘enemy’ consisted of jihadists, Ba’athists, and peaceful Sufis, who were in a majority but, like the militants, also opposed the US military presence and therefore needed to be influenced. The JSOU report referred to events in late 2004 in Fallujah where “US psychological warfare (PSYOP) specialists” undertook to “set insurgents battling insurgents.” This involved actually promoting Zarqawi’s ideology, ironically, to defeat it: “The PSYOP warriors crafted programs to exploit Zarqawi’s murderous activities – and to disseminate them through meetings, radio and television broadcasts, handouts, newspaper stories, political cartoons, and posters – thereby diminishing his folk-hero image,” and encouraging the different factions to pick each other off. “By tapping into the Fallujans’ revulsion and antagonism to the Zarqawi jihadis the Joint PSYOP Task Force did its ‘best to foster a rift between Sunni groups.’”
Yet as noted by Dahr Jamail, one of the few unembedded investigative reporters in Iraq after the war, the proliferation of propaganda linking the acceleration of suicide bombings to the persona of Zarqawi was not matched by meaningful evidence. His own search to substantiate the myriad claims attributing the insurgency to Zarqawi beyond anonymous US intelligence sources encountered only an “eerie blankness”.
 US soldiers in Fallujah
US soldiers in FallujahThe US military operation in Fallujah, largely justified on the claim that Zarqawi’s militant forces had occupied the city, used white phosphorous, cluster bombs, and indiscriminate air strikes to pulverise 36,000 of Fallujah’s 50,000 homes, killing nearly a thousand civilians, terrorising 300,000 inhabitants to flee, and culminating in a disproportionate increase in birth defects, cancer and infant mortality due to the devastating environmental consequences of the war.
To this day, Fallujah has suffered from being largely cut-off from wider Iraq, its infrastructure largely unworkable with water and sewage systems still in disrepair, and its citizens subject to sectarian discrimination and persecution by Iraqi government backed Shi’a militia and police. “Thousands of bereaved and homeless Falluja families have a new reason to hate the US and its allies,” observed The Guardian in 2005. Thus, did the US occupation plant the seeds from which Zarqawi’s legacy would coalesce into the Frankenstein monster that calls itself “the Islamic State.”
Bankrolling al-Qaeda in SyriaAccording to former French foreign minister Roland Dumas, Britain had planned covert action in Syria as early as 2009: “I was in England two years before the violence in Syria on other business,” he told French television: “I met with top British officials, who confessed to me that they were preparing something in Syria. This was in Britain not in America. Britain was preparing gunmen to invade Syria.”
Leaked emails from the private intelligence firm Stratfor, including notes from a meeting with Pentagon officials, confirmed that as of 2011, US and UK special forces training of Syrian opposition forces was well underway. The goal was to elicit the “collapse” of Assad’s regime “from within.”
Since then, the role of the Gulf states – namely Saudi Arabia, Qatar, Kuwait, the United Arab Emirates, and Jordan (as well as NATO member Turkey) – in officially and unofficially financing and coordinating the most virulent elements amongst Syria’s rebels under the tutelage of US military intelligence is no secret. Yet the conventional wisdom is that the funneling of support to Islamist extremists in the rebel movement affiliated to al-Qaeda has been a colossal and regrettable error.
The reality is very different. The empowerment of the Islamist factions within the ‘Free Syrian Army’ (FSA) was a foregone conclusion of the strategy.
 United States Secretary of State Hillary Clinton (R) greets Turkey’s Foreign Minister Ahmet Davutoglu (L), United Arab Emirates’ Foreign Minister Sheikh Abdullah bin Zayed al-Nahyan (2nd L) and British Foreign Minister William Hague, in Tunis
United States Secretary of State Hillary Clinton (R) greets Turkey’s Foreign Minister Ahmet Davutoglu (L), United Arab Emirates’ Foreign Minister Sheikh Abdullah bin Zayed al-Nahyan (2nd L) and British Foreign Minister William Hague, in TunisIn its drive to depose Col. Qaddafi in Libya, NATO had previously allied itself with rebels affiliated to the al-Qaeda faction, the Islamic Fighting Group. The resulting Libyan regime backed by the US was in turn liaising with FSA leaders in Istanbul to provide money and heavy weapons for the anti-Assad insurgency. The State Department even hired an al-Qaeda affiliated Libyan militia group to provide security for the US embassy in Benghazi – although they had links with the very people that attacked the embassy.
Last year, CNN confirmed that CIA officials operating secretly out of the Benghazi embassy were being forced to take extra polygraph tests to keep under wraps what US Congressman suspect was a covert operation “to move surface-to-air missiles out of Libya, through Turkey, and into the hands of Syrian rebels.”
With their command and control centre based in Istanbul, Turkey, military supplies from Saudi Arabia and Qatar in particular were transported by Turkish intelligence to the border for rebel acquisition. CIA operatives along with Israeli and Jordanian commandos were also training FSA rebels on the Jordanian-Syrian border with anti-tank and anti-aircraft weapons. In addition, other reports show that British and French military were also involved in these secret training programmes. It appears that the same FSA rebels receiving this elite training went straight into ISIS – last month one ISIS commander, Abu Yusaf, said, “Many of the FSA people who the west has trained are actually joining us.”
The National thus confirmed the existence of another command and control centre in Amman, Jordan, “staffed by western and Arab military officials,” which “channels vehicles, sniper rifles, mortars, heavy machine guns, small arms and ammunition to Free Syrian Army units.” Rebel and opposition sources described the weapons bridge as “a well-run operation staffed by high-ranking military officials from 14 countries, including the US, European nations and Arabian Gulf states, the latter providing the bulk of materiel and financial support to rebel factions.”
The FSA sources interviewed by The National went to pains to deny that any al-Qaeda affiliated factions were involved in the control centre, or would receive any weapons support. But this is difficult to believe given that “Saudi and Qatari-supplied weapons” were being funneled through to the rebels via Amman, to their favoured factions.
Classified assessments of the military assistance supplied by US allies Saudi Arabia and Qatar obtained by the New York Times showed that “most of the arms shipped at the behest of Saudi Arabia and Qatar to supply Syrian rebel groups… are going to hardline Islamic jihadists, and not the more secular opposition groups that the West wants to bolster.”
Lest there be any doubt as to the extent to which all this covert military assistance coordinated by the US has gone to support al-Qaeda affiliated factions in the FSA, it is worth noting that earlier this year, the Israeli military intelligence website Debkafile – run by two veteran correspondents who covered the Middle East for 23 years for The Economist – reported that: “Turkey is giving Syrian rebel forces, including the al-Qaeda-affiliated Nusra Front, passage through its territory to attack the northwestern Syrian coastal area around Latakia.”
In August, Debkafile reported that “The US, Jordan and Israel are quietly backing the mixed bag of some 30 Syrian rebel factions”, some of which had just “seized control of the Syrian side of the Quneitra crossing, the only transit point between Israeli and Syrian Golan.” However, Debkafile noted, “al-Qaeda elements have permeated all those factions.” Israel has provided limited support to these rebels in the form of “medical care,” as well as “arms, intelligence and food…
“Israel acted as a member, along with the US and Jordan, of a support system for rebel groups fighting in southern Syria. Their efforts are coordinated through a war-room which the Pentagon established last year near Amman. The US, Jordanian and Israeli officers manning the facility determine in consultation which rebel factions are provided with reinforcements from the special training camps run for Syrian rebels in Jordan, and which will receive arms. All three governments understand perfectly that, notwithstanding all their precautions, some of their military assistance is bound to percolate to al-Qaeda’s Syrian arm, Jabhat Al-Nusra, which is fighting in rebel ranks. Neither Washington or Jerusalem or Amman would be comfortable in admitting they are arming al-Qaeda’s Nusra Front in southern Syria.”
This support also went to ISIS. Although the latter was originally founded in Iraq in October 2006, by 2013 the group had significantly expanded its operations in Syria working alongside al-Qaeda’s al-Nusra until February 2014, when ISIS was formally denounced by al-Qaeda. Even so, experts on the region’s Islamist groups point out that the alleged rift between al-Nusra and ISIS, while real, is not as fraught as one might hope, constituting a mere difference in tactics rather than fundamental ideology.
 ISIS fighters pose for the camera
ISIS fighters pose for the cameraOfficially, the US government’s financial support for the FSA goes through the Washington DC entity, the Syrian Support Group (SSG), Syrian Support Group (SSG) which was incorporated in April 2012. The SSG is licensed via the US Treasury Department to “export, re-export, sell, or supply to the Free Syrian Army (‘FSA’) financial, communications, logistical, and other services otherwise prohibited by Executive Order 13582 in order to support the FSA.”
In mid-2013, the Obama administration intensified its support to the rebels with a new classified executive order reversing its previous policy limiting US direct support to only nonlethal equipment. As before, the order would aim to supply weapons strictly to “moderate” forces in the FSA.
Except the government’s vetting procedures to block Islamist extremists from receiving US weapons have never worked.
A year later, Mother Jones found that the US government has “little oversight over whether US supplies are falling prey to corruption – or into the hands of extremists,” and relies “on too much good faith.” The US government keeps track of rebels receiving assistance purely through “handwritten receipts provided by rebel commanders in the field,” and the judgement of its allies. Countries supporting the rebels – the very same which have empowered al-Qaeda affiliated Islamists – “are doing audits of the delivery of lethal and nonlethal supplies.”
Thus, with the Gulf states still calling the shots on the ground, it is no surprise that by September last year, eleven prominent rebel groups distanced themselves from the ‘moderate’ opposition leadership and allied themselves with al-Qaeda.
By the SSG’s own conservative estimate, as much as 15% of rebel fighters are Islamists affiliated to al-Qaeda, either through the Jabhut al-Nusra faction, or its breakaway group ISIS. But privately, Pentagon officials estimate that “more than 50%” of the FSA is comprised of Islamist extremists, and according to rebel sources neither FSA chief Gen Salim Idris nor his senior aides engage in much vetting, decisions about which are made typically by local commanders.
Part 2 – THE LONG WAR
Follow the moneyMedia reports following ISIS’ conquest of much of northern and central Iraq this summer have painted the group as the world’s most super-efficient, self-financed, terrorist organisation that has been able to consolidate itself exclusively through extensive looting of Iraq’s banks and funds from black market oil sales. Much of this narrative, however, has derived from dubious sources, and overlooked disturbing details.
One senior anonymous intelligence source told Guardian correspondent Martin Chulov, for instance, that over 160 computer flash sticks obtained from an ISIS hideout revealed information on ISIS’ finances that was completely new to the intelligence community.
 ISIS fighters in Mosul
ISIS fighters in Mosul“Before Mosul, their total cash and assets were $875m [£515m],” said the official on the funds obtained largely via “massive cashflows from the oilfields of eastern Syria, which it had commandeered in late 2012.” Afterwards, “with the money they robbed from banks and the value of the military supplies they looted, they could add another $1.5bn to that.” The thrust of the narrative coming from intelligence sources was simple: “They had done this all themselves. There was no state actor at all behind them, which we had long known. They don’t need one.”
“ISIS’ half-a-billion-dollar bank heist makes it world’s richest terror group,” claimed the Telegraph, adding that the figure did not include additional stolen gold bullion, and millions more grabbed from banks “across the region.”
This story of ISIS’ stupendous bank looting spree across Iraq made global headlines but turned out to be disinformation. Senior Iraqi officials and bankers confirmed that banks in Iraq, including Mosul where ISIS supposedly stole $430 million, had faced no assault, remain open, and are guarded by their own private security forces.
How did the story come about? One of its prime sources was Iraqi parliamentarian Ahmed Chalabi – the same man who under the wing of his ‘Iraqi National Congress’ peddled false intelligence about Saddam’s weapons of mass destruction and ties to al-Qaeda.
In June, Chalabi met with the US ambassador to Iraq, Robert Beecroft, and Brett McGurk, the State Department’s deputy assistant secretary of state for Iraq and Iran. According to sources cited by Buzzfeed in June, Beecroft “has been meeting Chalabi for months and has dined at his mansion in Baghdad.”
Follow the oilBut while ISIS has clearly obtained funding from donors in the Gulf states, many of its fighters having broken away from the more traditional al-Qaeda affiliated groups like Jabhut al-Nusra, it has also successfully leveraged its control over Syrian and Iraqi oil fields.
In January, the New York Times reported that “Islamist rebels and extremist groups have seized control of most of Syria’s oil and gas resources”, bolstering “the fortunes of the Islamic State of Iraq and Syria, or ISIS, and the Nusra Front, both of which are offshoots of al-Qaeda.” Al-Qaeda affiliated rebels had “seized control of the oil and gas fields scattered across the country’s north and east,” while more moderate “Western-backed rebel groups do not appear to be involved in the oil trade, in large part because they have not taken over any oil fields.”
 Jabhut al-Nusra rebels at Syrian oil fields
Jabhut al-Nusra rebels at Syrian oil fieldsYet the west had directly aided these Islamist groups in their efforts to operationalise Syria’s oil fields. In April 2013, for instance, the Times noted that al-Qaeda rebels had taken over key regions of Syria: “Nusra’s hand is felt most strongly in Aleppo”, where the al-Qaeda affiliate had established in coordination with other rebel groups including ISIS “a Shariah Commission” running “a police force and an Islamic court that hands down sentences that have included lashings.” Al-Qaeda fighters also “control the power plant and distribute flour to keep the city’s bakeries running.” Additionally, they “have seized government oil fields” in provinces of Deir al-Zour and Hasaka, and now make a “profit from the crude they produce.”
Lost in the fog of media hype was the disconcerting fact that these al-Qaeda rebel bread and oil operations in Aleppo, Deir al-Zour and Hasaka were directly and indirectly supported by the US and the European Union (EU). One account by the Washington Post for instance refers to a stealth mission in Aleppo “to deliver food and other aid to needy Syrians – all of it paid for by the US government,” including the supply of flour. “The bakery is fully supplied with flour paid for by the United States,” the Post continues, noting that local consumers, however, “credited Jabhat al-Nusra – a rebel group the United States has designated a terrorist organisation because of its ties to al-Qaeda – with providing flour to the region, though he admitted he wasn’t sure where it comes from.”
And in the same month that al-Qaeda’s control of Syria’s main oil regions in Deir al-Zour and Hasaka was confirmed, the EU voted to ease an oil embargo on Syria to allow oil to be sold on international markets from these very al-Qaeda controlled oil fields. European companies would be permitted to buy crude oil and petroleum products from these areas, although transactions would be approved by the Syrian National Coalition. Due to damaged infrastructure, oil would be trucked by road to Turkey where the nearest refineries are located.
“The logical conclusion from this craziness is that Europe will be funding al-Qaeda,” said Joshua Landis , a Syria expert at the University of Oklahoma.
Just two months later, a former senior staffer at the Syria Support Group in DC, David Falt, leaked internal SSG emails confirming that the group was “obsessed” with brokering “jackpot” oil deals on behalf of the FSA for Syria’s rebel-run oil regions.
“The idea they could raise hundreds of millions from the sale of the oil came to dominate the work of the SSG to the point no real attention was paid to the nature of the conflict,” said Falt, referring in particular to SSG’s director Brian Neill Sayers, who before his SSG role worked with NATO’s Operations Division. Their aim was to raise money for the rebels by selling the rights to Syrian oil.
Tacit complicity in IS oil smugglingEven as al-Qaeda fighters increasingly decide to join up with IS, the ad hoc black market oil production and export infrastructure established by the Islamist groups in Syria has continued to function with, it seems, the tacit support of regional and western powers.
 Baiji oil refinery in Iraq
Baiji oil refinery in IraqAccording to Ali Ediboglu, a Turkish MP for the border province of Hatay, IS is selling the bulk of its oil from regions in Syria and Mosul in Iraq through Turkey, with the tacit consent of Turkish authorities: “They have laid pipes from villages near the Turkish border at Hatay. Similar pipes exist also at [the Turkish border regions of] Kilis, Urfa and Gaziantep. They transfer the oil to Turkey and parlay it into cash. They take the oil from the refineries at zero cost. Using primitive means, they refine the oil in areas close to the Turkish border and then sell it via Turkey. This is worth $800 million.” He also noted that the extent of this and related operations indicates official Turkish complicity. “Fighters from Europe, Russia, Asian countries and Chechnya are going in large numbers both to Syria and Iraq, crossing from Turkish territory. There is information that at least 1,000 Turkish nationals are helping those foreign fighters sneak into Syria and Iraq to join ISIS. The National Intelligence Organization (MIT) is allegedly involved. None of this can be happening without MIT’s knowledge.”
Similarly, there is evidence that authorities in the Kurdish region of Iraq are also turning a blind eye to IS oil smuggling. In July, Iraqi officials said that IS had begun selling oil extracted from in the northern province of Salahuddin. One official pointed out that “the Kurdish peshmerga forces stopped the sale of oil at first, but later allowed tankers to transfer and sell oil.”
State of Law coalition MP Alia Nasseef also accused the Kurdistan Regional Government (KRG) of secretly trading oil with IS: “What is happening shows the extent of the massive conspiracy against Iraq by Kurdish politicians… The [illegal] sale of Iraqi oil to ISIS or anyone else is something that would not surprise us.” Although Kurdish officials have roundly rejected these accusations, informed sources told the Arabic daily Asharq Al-Awsat that Iraqi crude captured by ISIS was “being sold to Kurdish traders in the border regions straddling Iraq, Iran and Syria, and was being shipped to Pakistan where it was being sold ‘for less than half its original price.’”
An official statement in August from Iraq’s Oil Ministry warned that any oil not sanctioned by Baghdad could include crude smuggled illegally from IS:
“International purchasers [of crude oil] and other market participants should be aware that any oil exports made without the authorisation of the Ministry of Oil may contain crude oil originating from fields under the control of [ISIS].”
“Countries like Turkey have turned a blind eye to the practice” of IS oil smuggling, said Luay al-Khateeb, a fellow at the Brookings Doha Center, “and international pressure should be mounted to close down black markets in its southern region.” So far there has been no such pressure. Meanwhile, IS oil smuggling continues, with observers inside and outside Turkey noting that the Turkish government is tacitly allowing IS to flourish as it prefers the rebels to the Assad regime.
According to former Iraqi oil minister Isam al-Jalabi, “Turkey is the biggest winner from the Islamic State’s oil smuggling trade.” Both traders and oil firms are involved, he said, with the low prices allowing for “massive” profits for the countries facilitating the smuggling.
Buying ISIS oil?Early last month, a tanker carrying over a million barrels in crude oil from northern Iraq’s Kurdish region arrived at the Texas Gulf of Mexico. The oil had been refined in the Iraqi Kurdish region before being pumped through a new pipeline from the KRG area ending up at Ceyhan, Turkey, where it was then loaded onto the tanker for shipping to the US. Baghdad’s efforts to stop the oil sale on the basis of its having national jurisdiction were rebuffed by American courts.
In early September, the European Union’s ambassador to Iraq, Jana Hybášková, told the EU Foreign Affairs Committee that “several EU member states have bought oil from the Islamic State (IS, formerly ISIS) terrorist organisation that has been brutally conquering large portions of Iraq and Syria,” according to Israel National News. She however “refused to divulge the names of the countries despite being asked numerous times.”
A third end-point for the KRG’s crude this summer, once again shipped via Turkey’s port of Ceyhan, was Israel’s southwestern port of Ashkelon. This is hardly news though. In May, Reuters revealed that Israeli and US oil refineries had been regularly purchasing and importing KRG’s disputed oil.
Meanwhile, as this triangle of covert oil shipments in which ISIS crude appears to be hopelessly entangled becomes more established, Turkey has increasingly demanded that the US pursue formal measures to lift obstacles to Kurdish oil sales to global markets. The KRG plans to export as much as 1 million barrels of oil a day by next year through its pipeline to Turkey.
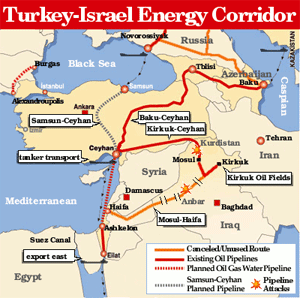 The Kirkuk-Ceyhan pipeline: Iraqi Kurdistan alone could hold up to 45 billion barrels of oil, allowing exports of up to 4 million barrels a day in the next decade if successfully brought to production
The Kirkuk-Ceyhan pipeline: Iraqi Kurdistan alone could hold up to 45 billion barrels of oil, allowing exports of up to 4 million barrels a day in the next decade if successfully brought to productionAmong the many oil and gas firms active in the KRG capital, Erbil, are ExxonMobil and Chevron. They are drilling in the region for oil under KRG contracts, though operations have been halted due to the crisis. No wonder Steve Coll writes in the New Yorker that Obama’s air strikes and arms supplies to the Kurds – notably not to Baghdad – effectively amount to “the defense of an undeclared Kurdish oil state whose sources of geopolitical appeal – as a long-term, non-Russian supplier of oil and gas to Europe, for example – are best not spoken of in polite or naïve company.” The Kurds are now busy working to “quadruple” their export capacity, while US policy has increasingly shifted toward permitting Kurdish exports – a development that would have major ramifications for Iraq’s national territorial integrity.
To be sure, as the offensive against IS ramps up, the Kurds are now selectively cracking down on IS smuggling efforts – but the measures are too little, too late.
A new mapThe Third Iraq War has begun. With it, longstanding neocon dreams to partition Iraq into three along ethnic and religious lines have been resurrected.
White House officials now estimate that the fight against the region’s ‘Islamic State’ will last years, and may outlive the Obama administration. But this ‘long war’ vision goes back to nebulous ideas formally presented by late RAND Corp analyst Laurent Muraweic before the Pentagon’s Defense Policy Board at the invitation of then chairman Richard Perle. That presentation described Iraq as a “tactical pivot” by which to transform the wider Middle East.
Brian Whitaker, former Guardian Middle East editor, rightly noted that the Perle-RAND strategy drew inspiration from a 1996 paper published by the Israeli Institute for Advanced Strategic and Political Studies, co-authored by Perle and other neocons who held top positions in the post-9/11 Bush administration.
The policy paper advocated a strategy that bears startling resemblance to the chaos unfolding in the wake of the expansion of the ‘Islamic State’ – Israel would “shape its strategic environment” by first securing the removal of Saddam Hussein. “Jordan and Turkey would form an axis along with Israel to weaken and ‘roll back’ Syria.” This axis would attempt to weaken the influence of Lebanon, Syria and Iran by “weaning” off their Shi’ite populations. To succeed, Israel would need to engender US support, which would be obtained by Benjamin Netanyahu formulating the strategy “in language familiar to the Americans by tapping into themes of American administrations during the cold war.”
The 2002 Perle-RAND plan was active in the Bush administration’s strategic thinking on Iraq shortly before the 2003 war. According to US private intelligence firm Stratfor, in late 2002, then vice-president Dick Cheney and deputy defense secretary Paul Wolfowitz had co-authored a scheme under which central Sunni-majority Iraq would join with Jordan; the northern Kurdish regions would become an autonomous state; all becoming separate from the southern Shi’ite region.
The strategic advantages of an Iraq partition, Stratfor argued, focused on US control of oil:
“After eliminating Iraq as a sovereign state, there would be no fear that one day an anti-American government would come to power in Baghdad, as the capital would be in Amman [Jordan]. Current and potential US geopolitical foes Iran, Saudi Arabia and Syria would be isolated from each other, with big chunks of land between them under control of the pro-US forces.
Equally important, Washington would be able to justify its long-term and heavy military presence in the region as necessary for the defense of a young new state asking for US protection – and to secure the stability of oil markets and supplies. That in turn would help the United States gain direct control of Iraqi oil and replace Saudi oil in case of conflict with Riyadh.”
The expansion of the ‘Islamic State’ has provided a pretext for the fundamental contours of this scenario to unfold, with the US and British looking to re-establish a long-term military presence in Iraq in the name of the “defense of a young new state.”
In 2006, Cheney’s successor, Joe Biden, also indicated his support for the ‘soft partition’ of Iraq along ethno-religious lines – a position which the co-author of the Biden-Iraq plan, Leslie Gelb of the Council on Foreign Relations, now argues is “the only solution” to the current crisis.
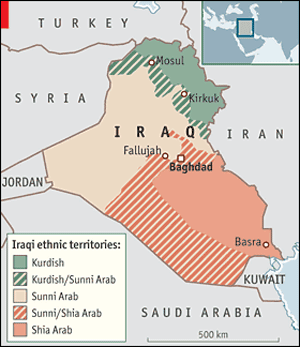
Also in 2006, the Armed Forces Journal published a map of the Middle East with its borders thoroughly re-drawn, courtesy of Lt. Col. (ret.) Ralph Peters, who had previously been assigned to the Office of the Deputy Chief of Staff for Intelligence where he was responsible for future warfare. As for the goals of this plan, apart from “security from terrorism” and “the prospect of democracy”, Peters also mentioned “access to oil supplies in a region that is destined to fight itself.”
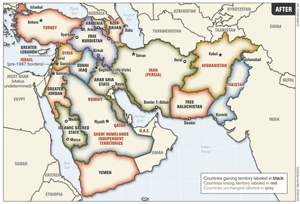
In 2008, the strategy re-surfaced – once again via RAND Corp – through a report funded by the US Army Training and Doctrine Command on how to prosecute the ‘long war.’ Among its strategies, one scenario advocated by the report was ‘Divide and Rule’ which would involve:
“… exploiting fault lines between the various Salafi-jihadist groups to turn them against each other and dissipate their energy on internal conflicts.”
Simultaneously, the report suggested that the US could foster conflict between Salafi-jihadists and Shi’ite militants by:
“… shoring up the traditional Sunni regimes… as a way of containing Iranian power and influence in the Middle East and Persian Gulf.”
One way or another, some semblance of this plan is in motion. Last week, Israeli foreign minister Avigdor Leiberman told US secretary of state John Kerry:
“Iraq is breaking up before our eyes and it would appear that the creation of an independent Kurdish state is a foregone conclusion.”
The rise of the ‘Islamic State’ is not just a direct consequence of this neocon vision, tied as it is to a dangerous covert operations strategy that has seen al-Qaeda linked terrorists as a tool to influence local populations – it has in turn offered a pretext for the launch of a new era of endless war, the spectre of a prolonged US-led military presence in the energy-rich Persian Gulf region, and a return to the dangerous imperial temptation to re-configure the wider regional order.
Nafeez Ahmed is a bestselling author, investigative journalist and international security scholar. He has contributed to two major terrorism investigations in the US and UK, the 9/11 Commission and the 7/7 Coroner’s Inquest, and has advised the Royal Military Academy Sandhust, British Foreign Office and US State Department, among government agencies.
Nafeez is a regular contributor to The Guardian where he writes about the geopolitics of interconnected environmental, energy and economic crises. He has also written for The Independent, Sydney Morning Herald, The Age, The Scotsman, Foreign Policy, Prospect, New Statesman, Le Monde diplomatique, among many others.
Nafeez’s just released new novel, ZERO POINT, predicted a new war in Iraq to put down an al-Qaeda insurgency. Follow him on Twitter @nafeezahmed and Facebook.