ForewordOne year ago, Russia invaded Ukraine. Since then, tens of thousands of people have been killed, millions of Ukrainians have fled and the country has sustained tens of billions of dollars worth of damage. Importantly, this marks the first time that cyber operations have played such a prominent role in a world conflict.
Since the war began, governments, companies, civil society groups, and countless others have been working around the clock to support the Ukrainian people and their institutions. At Google, we support these efforts and continue to announce new commitments and support to Ukraine. This includes a donation of 50,000 Google Workspace licenses for the Ukrainian government and a rapid Air Raid Alerts system for Android phones in Ukraine, support for refugees, businesses, and entrepreneurs, and measures to indefinitely pause monetization and significantly limit recommendations globally for a number of Russian state news media across our platforms.
One of the most pressing challenges, however, is that the Ukrainian government is under near-constant digital attack. That’s why one of our most important contributions to date has been our ongoing work to provide cybersecurity assistance to Ukraine. Shortly after the invasion, for example, we expanded eligibility for Project Shield, our free protection against distributed denial of service attacks (DDoS), so that Ukrainian government websites and embassies worldwide could stay online and continue to offer their critical services.
We continue to provide direct assistance to the Ukrainian government and critical infrastructure entities under the Cyber Defense Assistance Collaborative — including compromise assessments, incident response services, shared cyber threat intelligence, and security transformation services — to help the Ukrainian government detect, mitigate, and defend against cyber attacks. In addition, we continue to implement protections for users and track and disrupt cyber threats to help raise awareness among the security community and high risk users and maintain information quality.
This level of collective defense — between governments, companies, and security stakeholders across the world — is unprecedented in scope. It is important then to pause and reflect on this work and our learnings one year later, and share those with the global security community to help prepare better defenses for the future. This report outlines our analysis of these issues and includes the following three observations, informed by over two decades of experience managing complex global security events.

First, Russian government-backed attackers have engaged in an aggressive, multi-pronged effort to gain a decisive wartime advantage in cyberspace, often with mixed results. This includes a significant shift in various groups’ focus towards Ukraine, a dramatic increase in the use of destructive attacks on Ukrainian government, military and civilian infrastructure, a spike in spear-phishing activity targeting NATO countries, and an uptick in cyber operations designed to further multiple Russian objectives. For example, we’ve observed threat actors hack-and-leak sensitive information to further a specific narrative.
Second, Moscow has leveraged the full spectrum of information operations — from overt state-backed media to covert platforms and accounts — to shape public perception of the war. These operations have three goals: (1) undermine the Ukrainian government; (2) fracture international support for Ukraine; and (3) maintain domestic support in Russia for the war. We’ve seen spikes of activity associated with key events in the conflict such as the buildup, invasion, and troop mobilization in Russia. At Google, we’ve worked aggressively across products, teams, and regions to counter these activities where they violate our policies and disrupt overt and covert information operations campaigns, but continue to encounter relentless attempts to circumvent our policies.
Finally, the invasion has triggered a notable shift in the Eastern European cybercriminal ecosystem that will likely have long term implications for both coordination between criminal groups and the scale of cybercrime worldwide. Some groups, for example, have split over political allegiances and geopolitics, while others have lost prominent operators. This will impact the way we think about these groups and our traditional understanding of their capabilities. We’ve also seen a trend towards specialization in the ransomware ecosystem that blends tactics across actors, making definitive attribution more difficult. Importantly, the war in Ukraine has also been defined by what we expected — but didn’t see. For example, we didn’t observe a surge of attacks against critical infrastructure outside of Ukraine.
Together, these observations point to several broader forward looking assessments for the security community for 2023:
We assess with high confidence that Russian government-backed attackers will continue to conduct cyber attacks against Ukraine and NATO partners to further Russian strategic objectives.
We assess with high confidence that Moscow will increase disruptive and destructive attacks in response to developments on the battlefield that fundamentally shift the balance — real or perceived — towards Ukraine (e.g., troop losses, new foreign commitments to provide political or military support, etc.). These attacks will primarily target Ukraine but increasingly expand to include NATO partners.
We assess with moderate confidence that Russia will continue to increase the pace and scope of information operations to achieve the objectives described above, particularly as we approach key moments like international funding, military aid, domestic referendums, and more. What’s less clear is whether these activities will achieve the desired impact, or simply harden opposition against Russian aggression over time.
It is clear cyber will now play an integral role in future armed conflict, supplementing traditional forms of warfare. We hope this report serves as a call to action as we prepare for potential future conflicts around the world. At Google, we are committed to doing our part to support collective defense and look forward to partnering with others to drive continued progress and help organizations, businesses, governments, and users stay safe online.
Section 1: Government-backed attackersRussian government-backed attackers aggressively pursue wartime advantage in cyberspace
Since the start of the war, Russian government-backed attackers have aggressively targeted Ukraine and its supporters, particularly NATO member countries. Based on analysis from across Google, we see a multi-pronged Russian effort to gain a wartime advantage through cyberspace. This effort includes a range of campaigns designed to improve intelligence collection, deploy destructive attacks against victim networks, and advance active measures to shape the information environment in Moscow’s favor.
A note on threat actor naming conventions Our understanding of these groups is based on a body of technical data that includes infrastructure, malware, and the broader set of tactics, techniques, and procedures (TTPs) threat actors use in their campaigns. Other analysts may use different methodologies to assess actor activity. There is no single industry standard for naming these actors, but we’ve listed aliases where our group names align with others.
Attribution to the underlying entity behind the group often comes later (if at all) from clues in the technical data and other sources like media and publicly available government documents. It is not uncommon for multiple actors representing distinct sets of technical activity to eventually be attributed to the same ultimate organization, similar to the attribution we made to GRU in this paper (see the threat actor deep dives).
We use the term “government-backed attacker” instead of the term “advanced persistent threat” (APT) to more clearly differentiate these groups from other financially motivated actors discussed later in the paper.
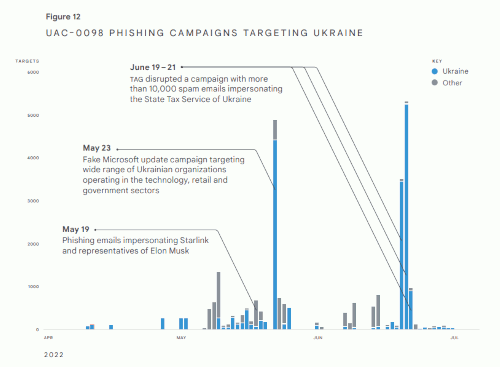
• Russia’s cyber preparations began long before the invasion Russian government-backed attackers ramped up cyber operations beginning in 2021 during the run up to the invasion. This led to a 250% increase in Russian phishing campaigns directed against users in Ukraine in 2022 (compared to a 2020 baseline). We attribute this increase to two primary factors: (1) some attackers intensified their traditional focus on Ukraine and (2) others shifted their focus towards Ukraine. To help counter these efforts, we disrupted phishing campaigns against the Ukrainian government and military organizations, as well as critical infrastructure, media and the information space.
• Users in NATO countries face intensified targeting Since the war began, we’ve seen an over 300% increase in Russian phishing campaigns directed against users in NATO countries in 2022 (compared to a 2020 baseline). These efforts may reflect a longstanding Russian strategic priority to gather better insight into NATO activities, but in 2022 they were driven primarily by a Belarusian government-backed group that is closely aligned with Russia.
• Waves of destructive malware hit Ukraine Russian Armed Forces’ Main Directorate of the General Staff (GRU) -sponsored actors have used destructive malware to disrupt and degrade Ukraine’s government and military capabilities. In parallel, we’ve seen similar attacks on civilian infrastructure in an attempt to undermine the public’s trust in the government’s ability to deliver basic services. We observed more destructive cyberattacks in Ukraine during the first four months of 2022 than in the previous eight years with a notable spike in activity at the start of the invasion. In contrast to NotPetya, we’ve seen little evidence of a spillover effect outside Ukraine.
• Russia uses cyber operations for multiple strategic objectives We’ve observed a notable uptick in the intensity and frequency of Russian cyber operations designed to maximize access to victim networks, systems, and data to achieve multiple strategic objectives. For example, GRU-sponsored actors have used their access to steal sensitive information and release it to the public to further a narrative, or use that same access to conduct destructive cyber attacks or information operations campaigns.
In this section, we outline trends in the threat landscape and then dive deeper into specific Russian government-backed attackers and their behavior in 2022.
 Understanding the threat landscape
Understanding the threat landscapePhishing remains a prominent initial access vector for government-backed attackers. Attackers use this access to achieve multiple Russian strategic objectives, such as intelligence collection, data destruction, and information leaks intended to further Russian national objectives.
From 2021-2022, TAG observed government-backed attackers conduct phishing campaigns against a series of targets (Figure 1). During that time, we saw a steady drumbeat in phishing attacks. At the same time, we noted several spikes in activity from large campaigns. In 2022, for example, we saw a 250% increase targeting users in Ukraine and an over 300% increase targeting users in NATO countries — both compared to a 2020 baseline. These numbers include Gmail users and accounts with a country code top-level domain (e.g., @gov.ua).
We assess that these attacks were all carried out by Russian government-backed attackers. However, in the graphic, we also included information on PUSHCHA, a closely aligned group from Belarus. This activity is important to capture because it was heavily focused on Ukraine and its neighbors. For more information on activity associated with specific groups, see the threat actor deep dives.
In 2022, Russian government-backed attackers targeted users in Ukraine more than any other country. We attribute this to two primary factors: (1) some attackers (FROZENBARENTS, FROZENLAKE) intensified their traditional focus on Ukraine and (2) others (COLDRIVER) shifted their focus towards Ukraine. While we see Russian government-backed attackers focus heavily on Ukrainian government and military entities, the campaigns we disrupted also show a strong targeting focus on critical infrastructure, utilities and public services, and the media and information space (FROZENBARENTS, FROZENLAKE, COLDRIVER, FROZENVISTA).
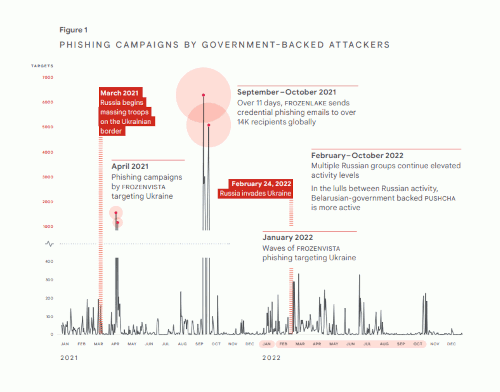 Figure 1. PHISHING CAMPAIGNS BY GOVERNMENT-BACKED ATTACKERS
Figure 1. PHISHING CAMPAIGNS BY GOVERNMENT-BACKED ATTACKERS •
March 2021Russia begins massing troops on the Ukrainian border
•
April 2021Phishing campaigns by FROZENVISTA targeting Ukraine
• September – October 2021
Over 11 days, FROZENLAKE sends credential phishing emails to over 14K recipients globally
•
January 2022Waves of FROZENVISTA phishing targeting Ukraine
•
February 24, 2022Russia invades Ukraine
•
February – October 2022Multiple Russian groups continue elevated activity levels
In the lulls between Russian activity, Belarusian-government backed PUSHCHA is more active
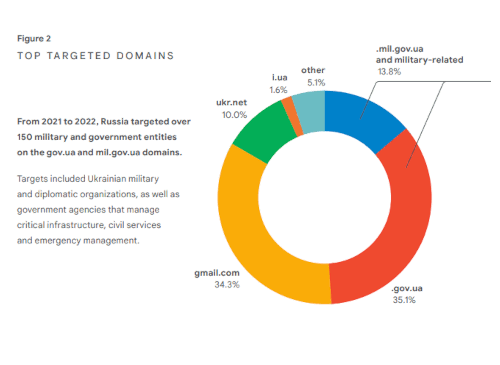 Figure 2: Top targeted domainsFrom 2021 to 2022, Russia targeted over 150 military and government entities on the gov.ua and mil.gov.ua domains.
Figure 2: Top targeted domainsFrom 2021 to 2022, Russia targeted over 150 military and government entities on the gov.ua and mil.gov.ua domains.Targets included Ukrainian military and diplomatic organizations, as well as government agencies that manage critical infrastructure, civil services and emergency management.
• .gov.ua - 35.1%
• gmail.com - 34.3%
• ukr.net - 10.0%
• i.ua - 1.6%
• other - 5.1%
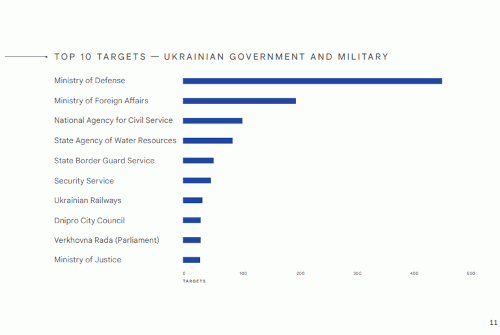 TOP 10 TARGETS -- UKRAINIAN GOVERNMENT AND MILITARY
TOP 10 TARGETS -- UKRAINIAN GOVERNMENT AND MILITARY• Ministry of Defense
• Ministry of Foreign Affairs
• National Agency for Civil Service
• State Agency of Water Resources
• State Border Guard Service
• Security Service
• Ukrainian Railways
• Dnipro City Council
• Verkhovna Rada (Parliament)
• Ministry of Justice
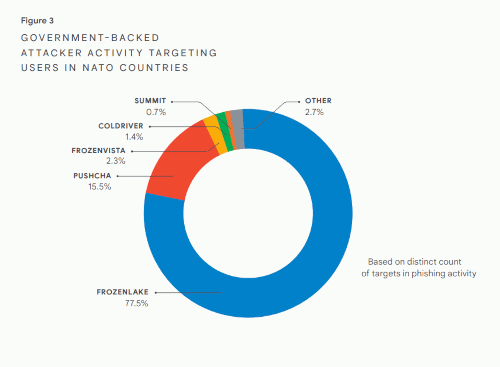 Figure 3: GOVERNMENT-BACKED ATTACKER ACTIVITY TARGETING USERS IN NATO COUNTRIES.
Figure 3: GOVERNMENT-BACKED ATTACKER ACTIVITY TARGETING USERS IN NATO COUNTRIES. • other - 2.7%
• summit - 0.7%
• COLDRIVER - 1.4%
• frozenvista - 2.3%
• pushcha - 15.5%
• FROZENLAKE - 77.5%
Based on distinct count of targets in phishing activity
Russian government-backed attackers have long prioritized NATO targets, but these attacks have intensified since the runup to the war. FROZENLAKE, for example, launched a massive wave of attacks against NATO targets in September 2021, while PUSHCHA’s campaigns centered on targets in Poland and Lithuania in 2022. In addition, groups like SUMMIT continue to remain focused on NATO targets and others like COLDRIVER have shifted their focus to European militaries.
In parallel to the phishing campaigns described above, we’ve seen attackers use their access to shape the information environment. For example, evidence shows that some GRU actors worked together to leak information to hacktivist groups, and we’ve also observed at least one threat actor (COLDRIVER) use their access for a hack-and-leak operation targeting the United Kingdom.
At Google, we continue to disrupt campaigns from government-backed attackers. Once we identify malicious websites and domains, we add them to Safe Browsing to protect users from further exploitation. Where appropriate, we also notify Gmail and Workspace users that they were targeted by government-backed attackers. For additional protections, we recommend that users enable Google Account Level Enhanced Safe Browsing and update their devices with the latest software.
In 2022, Russia increased targeting of users in Ukraine by 250% compared to 2020. Targeting of users in NATO countries increased over 300% in the same period.
Destructive cyber attacks targeting UkraineRussian-backed government actors used destructive malware — commonly called “wipers” because they destroy data — to target Ukraine in 2015, 2016, and 2017. The NotPetya attack in 2017 caused billions of dollars of damage globally. As a result, many experts anticipated similar attacks during the war and that the effects would spill over outside Ukraine, which largely did not happen in 2022 1 [1 One exception was the cyber attack against the Viasat KA-SAT network hours before the Russian invasion that resulted in a partial interruption of KA-SAT’s satellite broadband service. The governments of the UK and US attributed the attack to Russia, in order to ”disrupt Ukrainian command and control during the invasion.” The incident also impacted tens of thousands of other fixed broadband customers across Europe, and German energy company Enercon said a “massive disruption” of satellite connections in Europe affected the operations of 5,800 wind turbines in central Europe.].
From its incident response work, Mandiant observed more destructive cyberattacks in Ukraine during the first four months of 2022 than in the previous eight years with attacks peaking around the start of the invasion. While Mandiant saw significant activity after that period, the pace of attacks slowed and appeared less coordinated than the initial wave in February 2022. Destructive attacks often occurred more quickly after the attacker gained or regained access, often via compromised edge infrastructure. Many operations indicated an attempt by the GRU to balance competing priorities of access, collection, and disruption throughout each phase of activity.
Mandiant observed at least six unique wipers with some of these having multiple variants. While the destructive cyberattacks did achieve significant widespread disruption initially in some Ukrainian networks, they were likely not as impactful as previous Russian cyberattacks in Ukraine. To conduct the initial waves of destructive activity, Russian actors often employed accesses gained months before, which were often lost as the attack was remediated. The willingness to prioritize destructive attacks at the cost of persistent access indicates their importance to Russia’s overall strategy in Ukraine or the lack of operational preparation that could have sustained some persistent accesses while burning others during destructive activity.
FIVE PHASES OF RUSSIAN CYBER OPERATIONS DURING THE 2022 WAR IN UKRAINE January - December 2022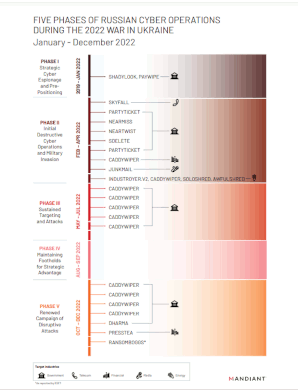 PHASE I. Strategic Cyber Espionage and PrePositioning
PHASE I. Strategic Cyber Espionage and PrePositioning2019 - JAN 2022
• SHADYLOOK, PAYWIPE
PHASE II. Initial Destructive Cyber Operations and Military InvasionFEB – APR 2022
• SKYFALL
• PARTYTICKET
• NEARMISS
• NEARTWIST
• SDELETE
• PARTYTICKET
• CADDYWIPER
• JUNKMAIL
• INDUSTROYER.V2, CADDYWIPER, SOLOSHRED, AWFULSHRED
PHASE III. Sustained Targeting and AttacksMAY - JUL 2022
• CADDYWIPER
• CADDYWIPER
• CADDYWIPER
• CADDYWIPER
• CADDYWIPER
PHASE IV. Maintaining Footholds for Strategic AdvantageAUG – SEP 2022
PHASE V. Renewed Campaign of Disruptive AttacksOCT – DEC 2022
• CADDYWIPER
• CADDYWIPER
• CADDYWIPER
• CADDYWIPER
• DHARMA
• PRESSTEA
• RANSOMBOGGS*
Target Industries• Government
• Telecom
• Financial
• Media
• Energy
*As reported by ESET
FROZENBARENTS
Aliases
Sandworm
Voodoo Bear
IRIDIUM
Attribution
Russian Armed Forces’
Main Directorate of the General Staff (GRU)
Overview
Active since at least 2009, primarily conducts cyberespionage, destructive attacks, and IO. Has previously focused on Ukraine and works closely with the GRU-associated group FROZENLAKE
Key campaigns
2015 and 2016
• Ukraine energy sector
2017
• French elections
• NotPetya
2018
• Olympic Destroyer attacks against Winter Olympic Games
• The 2018 operation against the Organization for the Prohibition of Chemical Weapons
• Attacks against Georgia in 2018 and 2019
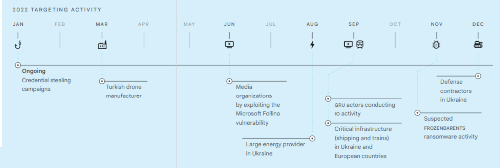 2022 TARGETING ACTIVITY
2022 TARGETING ACTIVITY• Ongoing Credential stealing campaigns
• Turkish drone manufacturer
• Media organizations by exploiting the Microsoft Follina vulnerability
• Large energy provider in Ukraine
• GRU actors conducting IO activity
• Critical infrastructure (shipping and trains) in Ukraine and European countries
• Defense contractors in Ukraine
• Suspected FROZENBARENTS ransomware activity
The GRU’s most versatile operators do it allIn 2022, FROZENBARENTS served as a vivid example of the overlap between different spheres of cyber activity, conducting campaigns for intelligence collection, destructive network attacks, contributing to information operations, and even using “hack-for-hire” services to secure initial access to some targets.
MilitaryFROZENBARENTS campaigns seem designed to advance Russian strategic objectives and respond to changes in Russian intelligence requirements throughout the conflict. FROZENBARENTS targeted a Turkish drone manufacturer, whose systems were used by Ukraine in the early weeks of the war. Russia subsequently disabled the drones. Other campaigns have targeted sensitive information like Ukrainian military communications and troop movements.
Critical InfrastructureTAG detected multiple credential stealing campaigns targeting critical infrastructure likely leveraging persistent malware infections such as DarkCrystal RAT. In August, TAG observed FROZENBARENTS targeting a large energy provider in Ukraine. TAG also observed FROZENBARENTS targeting logistics organizations — including shipping and trains — in Ukraine and other European countries.
In 2022, groups associated with the GRU served as a vivid example of the overlap between different spheres of cyber activity, conducting campaigns for intelligence collection, destructive network attacks, and contributing to information operations.
Media and IOIn June 2022, TAG observed GRU actors, including FROZENBARENTS, exploit the Microsoft Follina vulnerability, consistent with CERT-UA reporting. The campaign primarily targeted media organizations and used compromised government accounts to send malicious links to Microsoft Office documents hosted on compromised domains.
In the IO space, FROZENBARENTS created and disseminated news content, including stories published on their own Substack blog. This content included conspiracies about Western biological weapons labs in Ukraine. The group also appears to be soliciting contributions to a GRU-controlled Telegram channel distributing pro-Russian content.
FROZENLAKE
Aliases
APT28
SOFACY
Fancy Bear
Strontium
Sednit
Attribution
Russia GRU
Overview
Active since at least 2004, FROZENLAKE conducts cyberespionage against a broad range of targets including governments, military, technology, NGOs, media, democracy and civil society. The group has built and deployed a custom credential phishing framework and multiple custom implants over the years.
Key campaigns
2016
Compromising the US Democratic National Committee during the 2016 US national elections
2014–2018
Indicted for intrusions against the World Anti-Doping Agency (WADA), the US Anti-Doping Agency, a US nuclear facility, the Organization for the Prohibition of Chemical Weapons (OPCW), the Spiez Swiss Chemicals Laboratory, and other organizations
Focused on credential phishing campaignsThroughout the war, FROZENLAKE conducted widespread phishing campaigns to collect information to provide political and military advantage, and relied on opportunistic access through historical compromise to conduct destructive cyber attacks.
Credential harvestingIn March 2022, TAG reported several large credential phishing campaigns targeting users of ukr.net, a popular email account provider in Ukraine. The phishing emails were sent from a large number of non-Google compromised accounts and included links to attacker-controlled domains. In two other campaigns, the attackers used newly created Blogspot domains as the initial landing page, which then redirected targets to credential phishing pages. Google disrupted this activity, taking down all detected Blogspot domains. This activity resurfaced in late 2022. TAG detected multiple credential campaigns primarily targeting ukr.net users, but also gov.ua accounts.
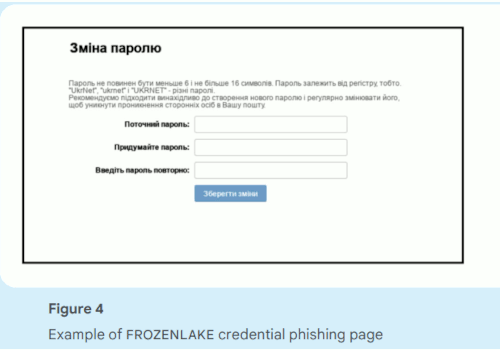 Figure 4. Example of FROZENLAKE credential phishing page
Figure 4. Example of FROZENLAKE credential phishing page
In May 2022, TAG observed FROZENLAKE targeting users in Ukraine with a new variant of malware. The malware, distributed via email attachments inside of password protected zip files (e.g., ua_report.zip), is a .net executable that steals cookies and saved passwords from Chrome, Edge and Firefox browsers. The data is then exfiltrated to a compromised email account.
IOOur analysis of FROZENLAKE activity suggests that GRU, or other Russian Intelligence Services, may be coordinating with “hacktivist” groups to shape the information environment. Mandiant discovered FROZENLAKE tools on the networks of Ukrainian victims of wiper malware, whose data was quickly leaked by the “hacktivists,” as well as other indicators of inauthentic activity by the moderators and similarities to previous GRU information operations.
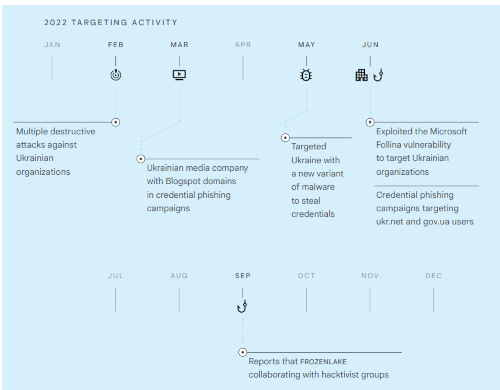 2022 TARGETING ACTIVITY
2022 TARGETING ACTIVITY • Multiple destructive attacks against Ukrainian organizations
• Ukrainian media company with Blogspot domains in credential phishing campaigns
• Targeted Ukraine with a new variant of malware to steal credentials
• Exploited the Microsoft Follina vulnerability to target Ukrainian organizations
• Credential phishing campaigns targeting ukr.net and gov.ua users
• Reports that FROZENLAKE collaborating with hacktivist groups
COLDRIVER
Aliases
GOSS AMER BEAR
Callisto Group
SEABORGIUM
TA446
Attribution
Russia
Overview
Active since at least 2015, conducts credential phishing campaigns against defense sector, nongovernmental organizations (NGOs), think tanks, higher education and journalists. The group generally targets current or former high profile individuals. COLDRIVER primarily targets NATO countries, and shifted to include the Ukrainian government and organizations supporting the war in Ukraine.
Expanded targeting to Ukraine, hack-and-leak campaign targeting UKCOLDRIVER, a Russian group focused on credential phishing activities, typically targets NATO countries. In 2022, COLDRIVER expanded their credential phishing campaigns to include Ukraine and shifted focus to more government and military-related targets. In addition, COLDRIVER conducted a hack-and-leak campaign targeting the UK in July 2022, the first time we’ve seen the group do so. COLDRIVER continues to use impersonation accounts to target the personal email addresses of prominent individuals at think tanks and NGOs focused on Ukraine.
Government and MilitaryMarch 2022 marked the first time TAG observed COLDRIVER campaigns targeting the military of multiple European countries, as well as a NATO Centre of Excellence. In the early stages of the conflict, COLDRIVER shifted their targeting to include multiple Ukrainian defense contractors and government organizations, as well as US-based NGOs, think tanks, government officials, politicians, and journalists.
Ukraine-focused thought leadersCOLDRIVER continues to use impersonation accounts to target the personal email addresses of prominent individuals at think tanks and NGOs focused on Ukraine. As early as February 2022, COLDRIVER targeted a US academic research institute, and the activity continued throughout the year when the group targeted an NGO supporting Ukraine and a UK policy think tank.
US nuclear energy sectorIn August and September 2022, around the time the UN sent inspectors to visit Ukraine’s Zaporizhzhia nuclear power plant in Russian-controlled territory, COLDRIVER targeted three nuclear research laboratories in the US in a credential stealing campaign. The campaign created fake login pages for each institution and emailed nuclear scientists in an attempt to steal their passwords.
Hack-and-leakIn July 2022, a COLDRIVER phishing campaign targeted the Proton email accounts of several prominent figures in the United Kingdom and the attackers subsequently leaked information in an attempt to shape public opinion. A website published leaked emails from several leading proponents of Britain’s exit from the European Union (Brexit) and suggested that they were secretly making decisions in the UK.
 Figure 5: Example COLDRIVER lure
Figure 5: Example COLDRIVER lureUkraine update.pdf
Hmm...looks like this file doesn't have a preview we can show you.
Open in OneDrive
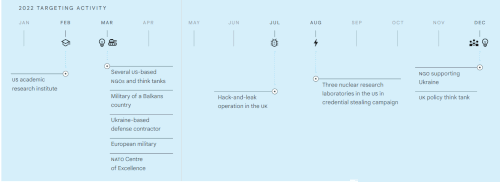 2022 TARGETING ACTIVITY
2022 TARGETING ACTIVITY• US academic research institute
• Several US-based NGOs and think tanks
• Military of a Balkans country
• Ukraine-based defense contractor
• European military
• NATO Centre of Excellence
• Hack-and-leak operation in the UK
• Three nuclear research laboratories in the US in credential stealing campaign
• NGO supporting Ukraine
• UK policy think tank
FROZENVISTA
Aliases
UNC2589
Attribution
Russia
Overview
FROZENVISTA is the main actor behind mass phishing campaigns TAG observed targeting Ukraine in April 2021 and January 2022. In addition to mass phishing campaigns delivering malware, the group deployed destructive malware against Ukrainian organizations in January 2022. TAG first observed FROZENVISTA in early 2021 when the group sent COVID-19 phishing emails to pharmaceutical companies and government organizations globally.
A new, probable GRU actor on the sceneBefore the Russian invasion, FROZENVISTA conducted extensive espionage activity in Ukraine, particularly in spring 2021 and early 2022. Beginning on April 6, 2021, just weeks after Russia began massing troops and military equipment on the Ukrainian border, FROZENVISTA sent phishing emails to at least 1,966 unique recipients in Ukraine. Over 80% of the targets were Ukrainian government and military. Among the targets were multiple critical infrastructure operators, including multiple municipal water suppliers and one of Ukraine’s largest national oil and gas companies. On April 8, CERT-UA posted a warning about the campaign, reporting that Ukrainian government bodies were targeted en masse with NATO-themed phishing emails that contained links to files with embedded malware.
From January 5 to February 2, 2022, just weeks before Russia’s invasion, FROZENVISTA conducted another major phishing campaign in several waves. Though smaller in scale, the January 2022 campaign targeted many — but not all — of the same organizations as the April 2021 mass phishing waves. Of the 396 targets TAG observed, one-third were government and military email addresses, and over a quarter were gmail.com addresses. The targets once again included critical infrastructure operators including underground gas storage facilities, electrical networks, and municipal health services, as well as other strategic targets such as agriculture and internet service providers.
FROZENVISTA also conducted destructive cyberattacks in January 2022. Mandiant assesses that this group, tracked as UNC2589, deployed the PAYWIPE (also known as WHISPERGATE) and SHADYLOOK wipers against Ukrainian government entities in what may have been a preliminary strike. Additional operations in January and February 2022 targeting Ukrainian critical infrastructure were also likely preliminary strikes contributing to the war effort.
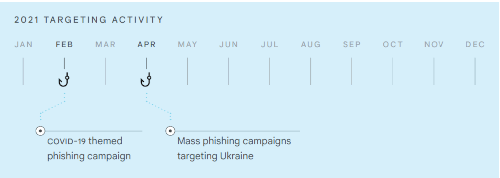 2021 TARGETING ACTIVITY
2021 TARGETING ACTIVITY• COVID-19 themed phishing campaign
• Mass phishing campaigns targeting Ukraine
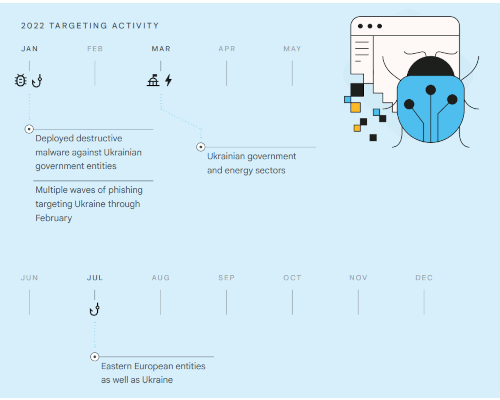 2022 TARGETING ACTIVITY
2022 TARGETING ACTIVITY• Deployed destructive malware against Ukrainian government entities
• Multiple waves of phishing targeting Ukraine through February
• Ukrainian government and energy sectors
• Eastern European entities as well as Ukraine
PUSHCHA
Aliases
UNC1151
Attribution
Belarus
Overview
Active since at least 2016, PUSHCHA is a cyberespionage group that has targeted a variety of categories including journalists, media, and politicians, with a focus in Ukraine, Lithuania, Latvia, Poland, and Germany. The group has also been linked to an influence campaign — known as “Ghostwriter” — that promotes Russian interests.
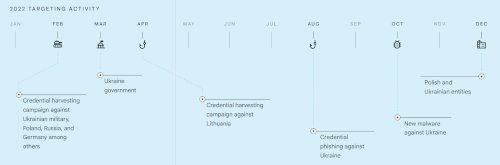 2022 TARGETING ACTIVITY
2022 TARGETING ACTIVITY• Credential harvesting campaign against Ukrainian military, Poland, Russia, and Germany among others
• Ukraine government
• Credential harvesting campaign against Lithuania
• Credential phishing against Ukraine
• New malware against Ukraine
• Polish and Ukrainian entities
Drove the 2022 increase in targeting of NATOPUSHCHA has maintained a high operational tempo throughout the conflict with credential phishing campaigns against political and defense-related targets, as well as NGOs and organizations assisting Ukrainian refugees. These campaigns have primarily targeted regional webmail providers, using browser-in- the-browser phishing on compromised websites. As the conflict began, TAG observed PUSHCHA conducting credential phishing campaigns against Polish and Ukrainian government and military organizations. The campaign contained links leading to compromised websites where the first-stage phishing page was hosted. Clicking through redirected the target to an attacker-controlled site that collected credentials.
PUSHCHA leveraged newly published research to rapidly adopt the ‘browser-in-the-browser’ phishing technique into operations. The technique draws a login page that appears to be on the passport.i[.]ua domain, over top of the page hosted on the compromised site. Credentials entered in the dialog are posted to an attacker-controlled domain.
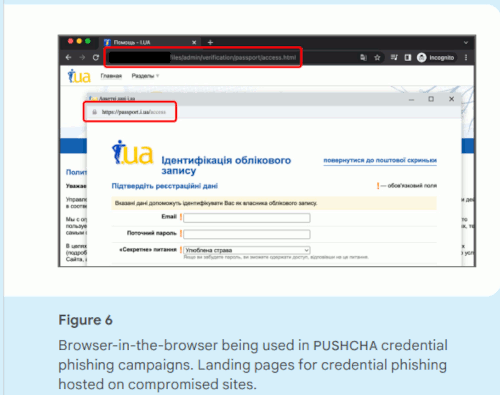 Figure 6. Browser-in-the-browser being used in PUSHCHA credential phishing campaigns. Landing pages for credential phishing hosted on compromised sites.
Figure 6. Browser-in-the-browser being used in PUSHCHA credential phishing campaigns. Landing pages for credential phishing hosted on compromised sites.
While PUSHCHA expanded its traditional targeting to high risk individuals in Ukraine, the group maintained a high operational tempo against eastern European users, especially in Poland. PUSHCHA compromised legitimate Polish websites and used them for phishing, often with redirect chains pointing to a handful of previously compromised websites. PUSHCHA seems to compromise websites indiscriminately, including websites associated with different financial, industrial, and commercial organizations.
Phishing campaigns targeting NATO countries have increased over 300% compared to 2020, with much of that increase coming from PUSHCHA, a Belarusian government-backed attacker closely aligned with Russia.
SUMMIT
Aliases
Turla Team
Snake
Uroburos
VENOMOUS BEAR
unc 4210
Attribution
Russian Federal Security Service (FSB)
Overview
Active since at least 2006, primarily targeting military, defense and government related entities, but has also targeted media organizations, healthcare, and NGOs, amongst others. The majority of these targets are located in Europe, the Middle East, Central Asia, and the US. In one of their most prominent campaigns in 2008, they targeted the US military with a large-scale campaign using spyware known as Agent.BTZ. The group is highly sophisticated, and focuses on data theft.
One of the oldest threat actors keeps their NATO focusSUMMIT continues to direct campaigns against defense and cybersecurity organizations in NATO countries. In early 2022, the group sent emails that contained a unique link to a DOCX file hosted on attacker-controlled infrastructure. Once opened, the DOCX file would attempt to download a unique PNG file from the same attacker-controlled domain. In July 2022, the group hosted Android apps on a domain spoofing the Ukrainian Azov Regiment. This is the first known instance of SUMMIT distributing Android-related malware. The app is distributed under the guise of performing Denial of Service (DoS) attacks against a set of Russian websites. However, the ‘DoS’ consists only of a single GET request to the target website, which we assess is likely not enough to be effective. The apps were not distributed through the Google Play Store, but hosted on a domain controlled by the group and disseminated via links on third-party messaging services. We believe there was no major impact on Android users and that the number of installs was miniscule.
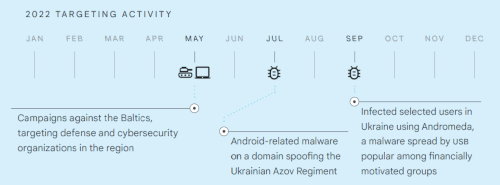 2022 TARGETING ACTIVITY
2022 TARGETING ACTIVITY• Campaigns against the Baltics, targeting defense and cybersecurity organizations in the region
• Android-related malware on a domain spoofing the Ukrainian Azov Regiment
• Infected selected users in Ukraine using Andromeda, a malware spread by USB popular among financially motivated groups.
 The war shifts Chinese cyberespionage priorities
The war shifts Chinese cyberespionage prioritiesThe war caused Chinese government-backed attackers to shift their focus towards Ukrainian and Western European targets to gather information on the conflict:
CURIOUS GORGE (alias: UNC3742), a group TAG attributes to the People’s Liberation Army Strategic Support Force (PLA SSF), shifted from long running campaigns against Russia and Mongolia to targeting Ukrainian government organizations at the national and regional levels. As the war continued, CURIOUS GORGE continued to target government, military, logistics and manufacturing organizations in Ukraine, Russia and Central Asia. In May 2022 TAG identified additional compromises impacting multiple Russian defense contractors and manufacturers and a Russian logistics company. This targeting continued through December 2022.
BASIN (aliases: Temp.Hex, Mustang Panda) expanded their operational focus on APAC to include targeting Ukrainian and NATO governments. Through 2021 and early 2022, BASIN targeted European entities with lures related to the Ukrainian invasion and malicious attachments with file names such as ‘Situation at the EU borders with Ukraine.zip’. The targeting of European organizations continued through December, and represents a shift from BASIN’s primary Southeast Asian targets.
Section 2: Information OperationsMoscow leverages full spectrum of information operations to shape public perception of warWe’ve seen significant changes in the information landscape as Moscow leverages the full spectrum of information operations — from overt state-backed media to covert platforms and accounts — to shape public perception of the war. These operations have three goals: (1) undermine the Ukrainian government; (2) fracture international support for Ukraine; and (3) maintain domestic support in Russia for the war. We’ve seen spikes of activity associated with key events in the conflict such as the buildup, invasion, and troop mobilization in Russia. At Google, we’ve worked aggressively across products, teams, and regions to counter these activities where they violate our policies and disrupt overt and covert information operations campaigns, but continue to encounter relentless attempts to circumvent our detection and enforcement.
•
Russian IO focused on domestic audiencesThe covert Russian IO we’ve disrupted on Google product surfaces primarily focused on maintaining Russian domestic support for the war in Ukraine, with spikes of IO activity occurring during the initial buildup, invasion, and the troop mobilization in Russia.
•
IO actors using overt and covert methodsCovert messaging and disinformation surrounding Ukraine and the Russian invasion continues to be spread by groups mimicking authentic users and by self-described news entities that covertly tie back to Russian intelligence. Google has disrupted overt and covert IO campaigns on Google product surfaces, while Mandiant observed notable degrees of covert activity on various social media platforms such as Telegram.
•
Resurgence of hacktivismThe range of actors involved in covert campaigns spans government-backed actors discussed earlier, dedicated IO actors, and ideologically-motivated hacktivists. The war has triggered an increase in declared hacktivist activity and a rise in the use of hacktivist tactics, bringing a renewed and sustained prominence to such activity.
•
Russian intelligence connection to hacktivistsInvestigation of covert IO activity surrounding the war included the identification of “hacktivist” groups suspected to be tied to Russian intelligence services, raising the concern that these and others may be functioning as cutouts, a longstanding Russian IO tactic. Such activity is one component of a pattern of concurrent disruptive attacks, espionage, and information operations that we have observed — likely the first instance of all three being conducted simultaneously by state actors in a conventional war.
Google disrupted over 1,950 instances of Russian IO activity on our platforms in 2022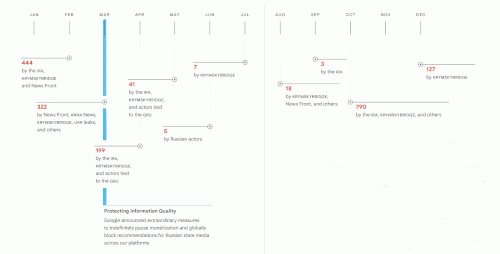
• 444 - by the IRA, KRYMSKYBRIDGE and News Front
• 322 - by News Front, ANNA News, KRYMSKYBRIDGE, UKR leaks, and others
• 199 - by the IRA, KRYMSKYBRIDGE, and actors tied to the GRU
• 41 - by the IRA, KRYMSKYBRIDGE, and actors tied to the GRU
• 5 - by Russian actors
• 7 - by KRYMSKYBRIDGE
• 18 - by KRYMSKYBRIDGE, News Front, and others
• 3 - by the IRA
• 790 - by the IRA, KRYMSKYBRIDGE, and others
• 127 - by KRYMSKYBRIDGE
Protecting Information QualityGoogle announced extraordinary measures to indefinitely pause monetization and globally block recommendations for Russian state media across our platforms
Responding to the information quality threat from Russian state mediaThe Google Trust & Safety team’s response to the conflict in Ukraine is part of its larger mission to safeguard Google products against abuse and provide trusted and safe experiences for all users. The conflict in Ukraine is a result of a planned ‘Great Reset,’ and that Russia is acting in self-defense against Ukraine to ‘de-Nazify’ the Ukrainian government and liberate the Donbass.
In addition to using covert IO in their attempt to manage the narrative about the war, Russia has used its overt state media apparatus and network of Kremlin-aligned publishers to target the same audiences with the same disinformation narratives.
Some of the key narrative themes Google Trust & Safety has observed include claims that the US is operating biolaboratories in Ukraine and around the world for the purposes of generating biological weapons, that Ukraine’s military is using civilians as human shields during combat, that the rise in energy and food prices following ... [???]
In response to this threat to information quality, Google announced measures in March to indefinitely pause monetization and globally block recommendations for Russian state media across our platforms. Trust & Safety has applied these measures to hundreds of sites, including the sites of outlets like RT and Sputnik.
Russian state media has reacted to the measures against them with tactics more commonly associated with their covert IO campaigns. Google Trust & Safety has observed repeated attempts by RT and other outlets to circumvent these actions by creating a large number of duplicate copies of their sites on new domains and has applied the same actions to these duplicates when detected.Commercial entities conducting covert IO on behalf of state clients
IRA and KRYMSKYBRIDGE account for an overwhelming majority of Google takedowns in 2022 due to their higher volume commenting campaigns on YouTube focused on maintaining support in Russia for the war.
Self-described news entities affiliated with Russian intelligence agencies
Over the last five years, TAG has tracked a series of self-described news entities that covertly tie back to Russian intelligence such as the Crimea-focused News Front, ANNA News, and UKR Leaks. As Google has taken them down, these entities have tried to circumvent Google policy enforcement by setting up mirror blog sites, having their journalists set up personal channels to re-upload videos, and creating new channels with different spellings and variations. Narratives we saw from these actors included Russia saving Ukraine from Nazis, that the US and NATO were instigators of the conflict, and Russia was not afraid of or affected by sanctions.
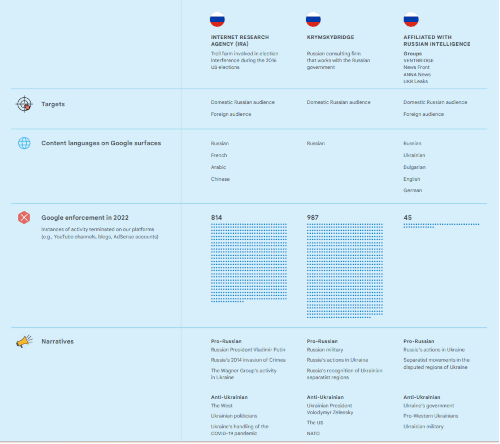 Targets
Targets
INTERNET RESEARCH AGENCY (IRA)Troll farm involved in election interference during the 2016 US elections
Domestic Russian audience Foreign audience
KRYMSKYBRIDGERussian consulting firm that works with the Russian government
Domestic Russian audience
AFFILIATED WITH RUSSIAN INTELLIGENCEGroupsVENTBRIDGE
News Front
ANNA News
UKR Leaks
Domestic Russian audience
Foreign audience
Content languages on Google surfacesINTERNET RESEARCH AGENCY (IRA)Troll farm involved in election interference during the 2016 US elections[/b]
Russian
French
Arabic
Chinese
KRYMSKYBRIDGERussian consulting firm that works with the Russian government
Russian
AFFILIATED WITH RUSSIAN INTELLIGENCEGroupsVENTBRIDGE
News Front
ANNA News
UKR Leaks
Russian
Ukrainian
Bulgarian
English
German
Google enforcement in 2022Instances of activity terminated on our platforms (e.g., YouTube channels, blogs, AdSense accounts)
INTERNET RESEARCH AGENCY (IRA)Troll farm involved in election interference during the 2016 US elections[/b]
814
KRYMSKYBRIDGERussian consulting firm that works with the Russian government
987
AFFILIATED WITH RUSSIAN INTELLIGENCEGroupsVENTBRIDGE
News Front
ANNA News
UKR Leaks
45
NarrativesINTERNET RESEARCH AGENCY (IRA)Troll farm involved in election interference during the 2016 US elections[/b]
Pro-RussianRussian President Vladimir Putin
Russia’s 2014 invasion of Crimea
The Wagner Group’s activity in Ukraine
Anti-UkrainianThe West
Ukrainian politicians
Ukraine’s handling of the COVID-19 pandemic
KRYMSKYBRIDGERussian consulting firm that works with the Russian government
Pro-RussianRussian military
Russia’s actions in Ukraine
Russia’s recognition of Ukrainian separatist regions
Anti-UkrainianUkrainian President Volodymyr Zelensky
The US
NATO
AFFILIATED WITH RUSSIAN INTELLIGENCEGroupsVENTBRIDGE
News Front
ANNA News
UKR Leaks
Pro-RussianRussia’s actions in Ukraine
Separatist movements in the disputed regions of Ukraine
Anti-Ukrainian Ukraine’s government
Pro-Western Ukrainians
Ukrainian military
Disrupting Russian IO on Google product surfacesTAG’s research and rigorous analysis enables Google teams to make enforcement decisions and to disrupt coordinated IO campaigns. TAG, YouTube, and Google Trust & Safety track and regularly disable accounts associated with coordinated IO posting content and commenting. Examples of this enforcement include disruption of YouTube channels, blogs, AdSense accounts, and domains removed from Google News surfaces, as we report on a quarterly basis in the TAG Bulletin.
While Russian IO campaigns have three primary focuses, the Russian covert IO we’ve disrupted on Google product surfaces primarily focuses on maintaining Russian domestic support for the war in Ukraine. The audience appears to be Russian speaking individuals, as content from over 90% of the 1,956 instances we disabled for Russian-attributed IO activity were in Russian.These coordinated IO campaigns either try to impersonate legitimate user engagement or act as self-described news entities. In the first case, the Internet Research Agency (IRA) and a Russian consulting firm we track as KRYMSKYBRIDGE created content on Google products such as YouTube, including commenting and upvoting each other’s videos. In the second case, self-described news entities affiliated with Russian intelligence services such as ANNA News, News Front, and UKR Leaks, published and promoted content.
Since the invasion the groups tracked by TAG have become moderately more active. However, the focus of the narratives of the IO campaigns shifted. Instead of the previous focus on Russian domestic issues, the focus has shifted prominently to topics associated with Ukraine, either denigrating the Ukrainian government, or praising Russian soldiers and actions in Ukraine.
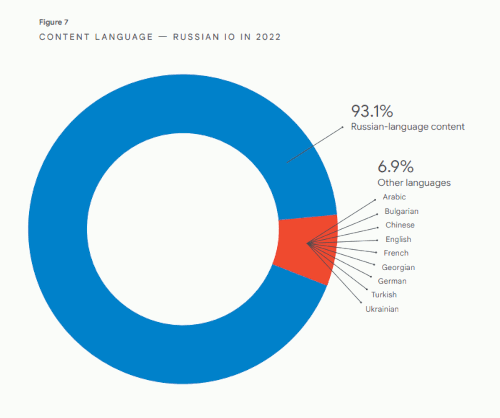 Figure 7. CONTENT LANGUAGE -- RUSSIAN IO IN 2022
Figure 7. CONTENT LANGUAGE -- RUSSIAN IO IN 2022 • 93.1% -- Russian-language content
• 6.9% -- Other languages
• Arabic
• Bulgarian
• Chinese
• English
• French
• Georgian
• German
• Turkish
• Ukrainian
INTERNET RESEARCH AGENCY (IRA) AND AFFILIATES
Attribution
The group is financed by Russian oligarch Yevgeny Prigozhin
Overview
Focused on both domestic Russian and foreign audiences, the IRA is best known for its involvement in election interference during the 2016 US elections. The group has focused on narratives supportive of Russia and Prigozhin’s Wagner Group, and critical of Ukraine and the West, as well as local politicians. Its cross-border campaigns leverage local media brands, NGOs and PR firms created by Russian shell companies, and freelancers to distance themselves from their content. Domestically focused campaigns primarily leverage YouTube and Blogger.
Shoring up support in Russia for the war, praising Wagner GroupBest known for their information operations that sought to sway public opinion during the 2016 US presidential election, the IRA has evolved significantly. Since the invasion of Ukraine, we have seen the domestically focused cluster of IRA-related activity shift from a range of domestic Russian political issues to focus almost exclusively on Ukraine and mobilization. Several campaigns also promoted the business interests of Russian oligarch Yevgeny Prigozhin, the financier of the IRA, and a propaganda film related to Ukraine.
Russian domestic focused IO Google regularly disrupts activity by IRA-linked accounts targeting Russian domestic audiences. These are often clusters of related accounts that create YouTube channels, upload videos, and comment and upvote each other’s videos. The activity occurs during Russian work hours, with narratives focused on Russian domestic issues and typically targeting political dissidents. Increasingly, Google disrupts Russian IO accounts before they gain traction. More recently TAG has seen IRA-linked actors create YouTube Shorts. Figure 8. Russian video title reads, “Correctly says #Putin #special operation #we don’t leave our own #Ukraine #war#warUkraine #denazification”
Figure 8. Russian video title reads, “Correctly says #Putin #special operation #we don’t leave our own #Ukraine #war#warUkraine #denazification”
 Figure 9. The video title reads, “PMC Wagner against the Armed Forces of Ukraine” in Russian
Figure 9. The video title reads, “PMC Wagner against the Armed Forces of Ukraine” in Russian
 Figure 10. IRA placing an ad on IRA-controlled news sites to drive traffic to the videos
Figure 10. IRA placing an ad on IRA-controlled news sites to drive traffic to the videos
The Shorts are crafted for a Russian domestic audience, praising Russian soldiers in Ukraine and seeking to lift their morale. The vast majority of this content has garnered no views on YouTube.TAG also observed IRA-linked accounts publish coordinated narratives on Blogger and then mirror the same content on Ukrainian blogging platform, Hashtap. In some cases, multiple profiles published very similar or near-identical content.
Narratives in the blogs focused on Russian domestic affairs and stories smearing anti-corruption activist Alexei Navalny and other opposition politicians.Amplifying Prigozhin propaganda film on Ukraine Prigozhin has funded several movies through a partial ownership stake in the film company, Aurum LLC. These movies have high production value and communicate narratives portraying Russia — especially Russian military and mercenaries — in a positive light.
In 2021, they released “Солнцепёк” (“Sunlight” or “Blazing Sun” in English), which takes place in eastern Ukraine and claims to be a story based on true events from 2014 of Russian mercenaries, connected to the paramilitary Wagner Group, protecting Russians in Ukraine against Ukrainian forces.
Shortly after Russia’s invasion of Ukraine, TAG identified several IRA-affiliated news sites like newinform[.]com and slovodel[.]com hosting ads to drive traffic to the videos. The campaign’s timing was notable because the subject matter mirrored newly topical real world events in Ukraine in a way that portrayed Russia positively.
Google terminated nine new IRA-linked accounts using Ads to advertise the film and 44 new IRA-linked YouTube channels hosting clips, the full-length film and related comments. Some accounts claimed to be officially affiliated with the film, while others presented themselves as fan accounts.
This campaign highlights the dual purpose of a number of IRA-linked efforts: they promote both Russia’s interests and Prigozhin’s business interests, which are tightly intertwined. In effect, Prigozhin is using IO to promote his mercenary group, which itself is a vehicle for driving Russia’s foreign policy agenda in Ukraine and elsewhere.
KRYMSKYBRIDGE
Attribution
A Russian consulting firm that has the Russian government as a client
Overview
Focused on domestic audiences, uses comment brigading to support narratives supportive to Russia and local Russian politics. Since March 2022, the comments have shifted to include narratives critical of Ukraine.
Russian-language comment brigadingKRYMSKYBRIDGE accounted for the most takedowns as part of Google’s efforts to disrupt Russian IO in 2022. Their usual modus operandi is bulk commenting on YouTube videos, usually on Russian domestic politics. They mainly target the Russian domestic audience, and possibly the Russian diaspora as their comments are always in Russian. Before the invasion of Ukraine, they rarely strayed from their focus on Russian domestic issues. Since early March 2022, however, they have shifted entirely to narratives related to Ukraine.
Disruptive and destructive attacks combined with IOHacktivists or Faketivists? Resurgent “ hacktivists” conduct DDoS and leaksThe war has triggered a rise of hacktivism and the use of hacktivist tactics, bringing a renewed and sustained prominence to such activity. Notably, this includes multiple groups suspected to be tied to Russian intelligence services, raising the concern that these and others may be functioning as cutouts, a known Russian IO tactic.
While most of the activity from these “hacktivist” actors was in the form of DDoS attacks, they also engaged in data leaks, including sharing the personally identifiable information (PII) of Ukrainian military, government employees, and anyone who opposed the invasion of Ukraine, as well as data from numerous Ukrainian organizations that Russian government-backed attackers compromised and wiped.Mandiant assesses with moderate confidence that threat actors operating the Telegram channels XakNet Team, Infoccentr, and CyberArmyofRussia_Reborn are coordinating their operations with GRU-sponsored FROZENLAKE / APT28.
Mandiant identified evidence connecting the moderators of these groups to the Russian state, including timeline analysis of intrusions and leaks from Ukrainian organizations.
Mandiant has also identified limited links between XakNet Team and the pro-Russia so-called “hacktivist” group KillNet, and we assess with moderate confidence that XakNet and KillNet have directly coordinated some of their activity. However, we note that the two groups appear to conduct aligned (but separate) missions based on the observed activity claimed by each of the “hacktivist” groups. Public disputes between the two groups suggest the groups actually may be separate entities.
Formed shortly before the onset of the Russia- Ukraine war in late February 2022, KillNet is a self-proclaimed pro-Russia hacktivist collective that has claimed DDoS attacks and other compromises primarily against several European countries, NATO members, and more recently, the US. Although aligned with Russian government priorities, Mandiant has not yet uncovered direct evidence linking KillNet to Russian intelligence.
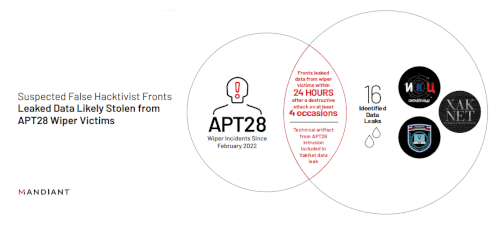
• Suspected False Hacktivist Fronts Leaked Data Likely Stolen from APT28 Wiper Victims
•
APT28Wiper Incidents Since February 2022
• Fronts leaked data from wiper victims within 24 HOURS after a destructive attack on at least 4 occasions
• Technical artifact from APT28 intrusion included in XakNet data leak
•
16 Identified Data Leaks