Part 7 of 11
Joint Inquiry Report ADDITIONAL VIEWS The Honorable Jane Harman
The Joint Inquiry report is a strong product from a strong staff and unprecedented Congressional collaboration. I strongly support this report. It provides the most complete and comprehensive assessment of the plot behind the 9/11 terrorist attacks. It identifies systemic and structural problems within the U.S. Intelligence Community that hampered the prevention of these attacks. And, most important, it looks forward: it applies lessons learned to make recommendations critical to prevent further attacks. Using the information in this report, the 108th Congress has a base on which to oversee, fund, reshape, and reform the intelligence functions of the federal government.
The additional views below supplement the report's findings and recommendations.
Director of National Intelligence
To date, the term "Intelligence Community" (IC) has been an oxymoron. The community is really a collection of stovepipes working separately -often in conflicting or self-interested ways.
Creating a real Community requires a coherent approach across agencies and overarching leadership. The recommendation aims to empower a Director of National Intelligence (DNI) to lead the community by pairing authority with responsibility. The Director of Central Intelligence currently lacks the statutory authority to do this.
The DNI would also have the responsibility and accountability for bringing unity to the different intelligence collection and analysis functions. The Director would allocate budget resources to provide people and technology where they are needed most, regardless of which federal department houses the agency.
All agree that the Administration, Congress, and the IC leadership must act together to foster a more innovative and less risk-averse intelligence culture. The employees in intelligence agencies today are hard-working, capable, and dedicated, but often lack the resources and tools they need to gather, process, analyze, and use information in today's digital environment. In my view, these workers deserve the trust and appreciation of Congress and the nation, and should be encouraged and empowered to be imaginative, innovative, and collaborative in order to protect us from future attacks.
Information Sharing
The investigation revealed that significant intelligence leads about some of the hijackers were available but did not get widely shared. This was less a willful refusal to share information than it was a failure to grasp its significance. For example, the CIA and NSA had collected information on hijackers al Hazmi and al Mihdhar that connected them to bin Laden, the East Africa Embassy bombings, and the attack on the USS Cole. The agencies also had information indicating that both men were in the United States. The al Hazmi and al Mihdhar story shows what many analysts had claimed for years-the raw databases of CIA and NSA contain extremely valuable information that does not get noticed, shared, integrated, or acted upon.
Entities within the agencies that collect signals and human intelligence guard their "raw" data; few outside analysts are allowed access. The NSA and CIA's Directorate of Operations typically insist that they alone, not even all-source intelligence analysts or other sophisticated consumers, possess the special expertise required to evaluate human or signals intelligence data. Before sharing information, these entities go through an internal analysis process that "filters" out everything that does not seem to the analyst sufficiently important or reliable to report. But as the al Hazmi and al Mihdhar cases demonstrate, analysts can fail to appreciate what might be important to potential consumers, who bring different perspectives and other sources of information.
There are powerful reasons why the entities within the CIA, NSA, and FBI that collect the raw data are so unwilling to allow access to outside analysts -even those within their parent agency. Compartmentation of classified information is sometimes needed to protect sensitive sources and methods. There is also a need to protect constitutionally-protected privacy rights. For example, NSA personnel are trained in "minimization" procedures to cordon off and protect the communications the agency intercepts. The FBI, historically, has been very concerned to protect the integrity of actual or potential legal proceedings, causing its field offices to restrict access to its unreported information.
These obstacles to full exploitation of intelligence information hinder our national security, and must be overcome. It should be feasible to clear all-source counterterrorism analysts to the same standards demanded of the human and signals intelligence collectors and train them in "minimization" procedures to protect the privacy of U.S. persons.
As intelligence agencies increasingly focus on homeland security, they must share information with state and local governments, first responder groups, private companies, and the American public. To the extent possible, the intelligence community should create unclassified products that provide guidance for the appropriate responder groups to prevent or prepare for terrorist threats. The IC must work with the Department of Homeland Security to match threat information with vulnerability assessments, and provide the new Department with the intelligence it needs to communicate to first responders what they should look for.
Domestic Intelligence Collection
The findings reflect problems in gathering and processing actionable intelligence about foreign terrorists on American soil. Problems also exist for gathering and handling intelligence on Americans who assist foreign terrorists or plan terrorist plots. The nature of the terrorist threat does not allow us the luxury of focusing abroad to learn of terrorist activity; we must recognize the existence of terrorist organizations within the United States and develop the capacity to uncover, infiltrate, and disrupt them while respecting the privacy and Constitutional rights of law abiding Americans.
The FBI is currently responsible for gathering intelligence within the United States, but is not adequately organized nor resourced to successfully meet this mission. Notwithstanding efforts by FBI Director Mueller, the FBI does not have a robust counterterrorism capability, and there are serious policy and legal questions in co-locating within one agency responsibility for domestic intelligence with law enforcement. Intelligence is fundamentally predictive, based on assumptions, hypotheses, analyses, and forecasts; law enforcement is responsive, based on credible evidence. These functions use different approaches and operating procedures and there is great risk that marrying the two will sacrifice one or both.
The report recommends further study and debate of a separate domestic intelligence agency, without law enforcement responsibility or authorization. Such an entity would be modeled on Britain's MI-5, but would be tailored to reflect the U.S. federal system and civil rights laws. Establishing a new agency is not a panacea; Congress must vest any new entity with authorities and safeguards following a national debate over the appropriate scope of domestic intelligence collection.
Privacy and Civil Liberties
Collecting information on U.S. citizens and foreign visitors in the United States raises serious civil liberty and privacy implications, and it is critical that Congress defend the freedoms and rights of Americans and others. The report recommends continuing Congressional oversight of domestic intelligence authorities, including a review of the implementation of the Foreign Intelligence Surveillance Act and USA Patriot Act.
Within the Executive Branch, it is important that the position of Civil Rights and Civil Liberties Officer in the Department of Homeland Security be filled promptly by a senior and well- respected official so that protection of civil liberties is an integral part of homeland security planning and strategy, and not as an afterthought.
Leaks
Throughout the Joint Inquiry, I have expressed concern with what appear to be frequent leaks of classified intelligence information. The public disclosure of sensitive intelligence information can have devastating effects on intelligence sources and methods needed to fight terrorism. The report recommends the President and agency heads take specific steps to prevent and appropriately punish the unauthorized disclosure of properly classified intelligence. The 108th Congress should demand updates on the measures recommended by the Attorney General in a report to the Congress in fall 2002.
Conclusion
Intelligence remains the key to preventing terrorist attacks. The IC has had many successes in uncovering and preventing attacks that, by necessity, go unreported and publicly unappreciated. But terrorists need to be successful only once to kill Americans and demonstrate the inherent vulnerabilities we face.
We have learned that despite considerable attention and significant efforts across and throughout the intelligence agencies in the summer of 2001, crucial information was not exploited, and organizational barriers in the IC blocked preventive action. Solutions to these problems involve forging a true "digital" community of intelligence agencies with strong leadership, overcoming entrenched bureaucratic and risk-averse cultures, and empowering our intelligence employees. This report and these additional views are a basis for action in the 108th Congress. It will be my priority to see these improvements made.
Report of the Joint Inquiry Into the Terrorist Attacks of Se
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
Part 8 of 11
A JOINT INQUIRY STAFF REPORT ADDITIONAL VIEWS SENATOR JON KYL, SENATOR PAT ROBERTS
I. The Need for Additional Views
The Report is a product of the Joint Inquiry Staff (JIS), not the Senators and Representatives who sit, respectively, on the Senate Select Committee on Intelligence (SSCI) and the House Permanent Select Committee on Intelligence (HPSCI). The Chairman and Vice Chairman of the SSCI and the Chairman and Ranking Member of the HPSCI (the "Big Four") made most decisions and supervised the JIS. The JIS should be commended for putting together the first official account of the events leading up to the terrorist attacks of September 11, 2001.
It is difficult, however, for rank-and-file Members of the two committees to know how thorough or accurate the Report is because of the way the JIS and the "Big Four" conducted the inquiry, withholding information and decisions from the Members and SSCI and HPSCI staff throughout the process. While the Report should be a useful historical document on which to base further inquiries, we cannot vouch for its contents.
Beyond that, the investigation was deficient for what it did not include. While intelligence community failures were identified, they were presented frequently in a mode of "mistakes were made" rather than as the beginning of an inquiry as to why they were made.
After prodding by several Senators, some underlying causes of these failures were identified, but even then, they were not further probed to determine what might have been done differently. And the fact that the prodding was necessary illustrates our concern that the JIS either ran out of time or did not have the inclination or instruction to examine, for instance, why U.S. government agencies were risk-averse, who is responsible for the inadequate resources devoted to counter-terrorism efforts, why legal authorities were so confusing, and why leadership was so lacking. Without this examination, the Report will be of limited value in determining "lessons learned."
The record should also reflect some of the differences in opinion among Members on how the Report was (or should have been) prepared. The inquiry was conducted and overseen in a way that left rank-and-file Members at a distinct disadvantage, and left insufficient time to examine many relevant issues. The final draft of the Report -- which is several hundred pages long and highly classified -- was delivered to Members four days before the one and only meeting scheduled for its consideration, when most Members were out of town. There was no debate about the Report, only about the Recommendations. But there was little basis for debate since the product was strictly the work of the JIS -- more like an Inspector General's report than a typical congressional committee report. Throughout the process, rank-and-file Members complained about irregularities. Specific examples include:
Upon instructions from the Chairmen -- and in violation of SSCI rules -- the JIS often failed to tell Members and staff of important non-compartmented information it discovered in a timely manner.
Information relating to open hearings -- such as the JIS staff statement and witness statements -- were routinely provided only late on the night before the hearing.
Committee staff, and sometimes even the staff directors, were often excluded from meetings of the "Big Four," whose decisions were often made without consultation. Members' liaison staff, and, therefore, the Members themselves, were in the dark about these decisions.
Despite repeated requests, records of JIS interviews with key witnesses conducted in the spring were not made available to committee staff for review until fall, when the final draft report was already in the late drafting stages.
Over the strong objections of several Members, and key officials of the intelligence community, the "Big Four" scheduled a series of open hearings that sidetracked the ongoing investigation from mid-July to late October.
Here is a representative example of the lack of meaningful rank-and-file input into "Big
2
Four" decisions: During the JIS hearing of September 24, 2002 on "U.S. Government Counter- Terrorism Organizations and the Evolution of the Terrorist Threat," Chairman Goss asked unanimous consent to include in the record several documents relating to that day's hearing. However, among these documents were requests to the administration regarding its decision not to declassify certain information. These requests from the "Big Four" were made without consultation with the rank-and-file Members -- a fact that Senator Kyl noted for the record at that time. He stated: "Mr. Chairman, I have no objection, but I would like the record to note that the matter that the four of you spoke to is not a matter that has been discussed by the full membership of the committee. Therefore, at least I for one am in no position to judge whether the requests that you have made are warranted or not."
The holding of open hearings was particularly frustrating. The decision to hold them was apparently made by the "Big Four" despite the concerns of the JIS and the objections of other Senators. The JIS was forced to focus on them for three months, and from there had to go right into drafting the Report in order to meet the year-end deadline.
Several Members voiced their opposition to holding open hearings before the investigative work was completed and the Report written (and, we had supposed, agreed to). We objected, mostly in closed committee business meetings, that it was premature to convene open hearings before the investigation was complete. And indeed, at the point when the JIS began preparing for them (July, 2002), its investigations into the causes of 9/11 largely ground to a halt. Due to dramatic media leaks and the potential for further compromise, intelligence agencies "pushed back" against open hearings, causing further friction with the JIS investigation.
The hearings distracted these agencies, our "front line troops" on the war on terrorism, and they distracted Members and congressional staff from our traditional oversight responsibilities. They also, in our view and the view of Vice Chairman Shelby, publicly revealed a lot of sensitive information from which our enemies could profit. Most of the information presented had already been revealed in closed hearings, which were far more productive because those who participated could delve freely into classified information.
Key figures in our counter-terrorism efforts were unnecessarily compromised by these public hearings. A case in point is the Arizona resident whose identity came out in the media.
3
His name and face were even broadcast on Al-Jazeera. His family was harassed and was potentially in danger from extremists. Our hard-working people deserve better treatment than that. We should have been more circumspect about publicly releasing results before the investigation was complete and the two intelligence committees had had a chance to adequately review the final Report.
II. Deficiencies in the Report
These inadequacies in the process resulted in a Report that falls well short of addressing the core problems that led to 9/11. Because the fundamental problems that led to 9/11 are almost certainly rooted in poor policy and inadequate leadership, the investigation should have delved more deeply into conflicting interpretations of legal authorities (including presidential directives), budget allocations, institutional attitudes, and other key areas. Only penetrating these areas will tell us how policymakers, including Congress, contributed to the failures the Report identifies. In other words, only such a thorough exercise will help us to make sure the failures are not repeated.
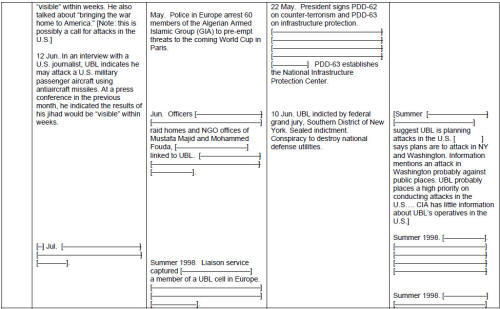
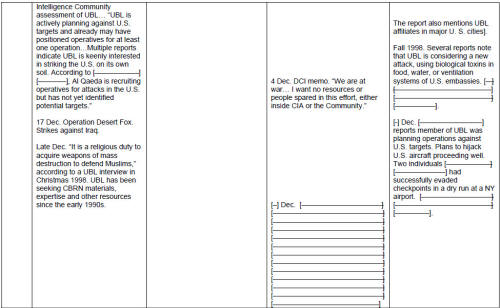
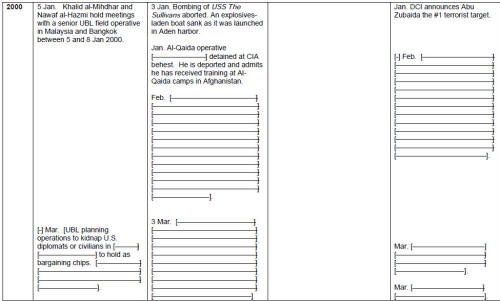
What best shows the tendency of the JIS investigation to go to the water's edge but no farther is that, in the Report, there is a pronounced tendency to identify problems as "facts," or "realities," rather than as matters to be plumbed for underlying causes. For instance, we have the following JIS testimony to the joint committees: "The 1996 Khobar Towers attack, the 1998 African embassies attacks, and the 2000 USS Cole attack led the Departments of State and Defense to focus heavily on force protection, but not on meeting the challenge of Afghanistan, even though they recognized the dangers emanating from terrorist camps there." [1] So, the problem of Afghanistan as a haven for terrorists was widely recognized. But the CIA and FBI lacked the means, and also lacked a plan, to go after training camps in Afghanistan in a comprehensive manner. It would be reasonable to wonder at this point: What efforts were made to penetrate various groups in Afghanistan (or if there were efforts, why were they not successful), and why
_______________
1 Emphasis added. Written statement of Eleanor Hill, in testimony before a hearing of the House Permanent Select Committee on Intelligence and the Senate Select Committee on Intelligence (hereafter "the joint committees"), October 8, 2002.
4
was there no attempt to beef up the military for a comprehensive response? The record shows that little effort was made to effectively utilize the military even after President Clinton's post-embassy bombing declaration in 1998 that "there will be no sanctuary for terrorists." Again, it is reasonable to ask why actions did not match words. These are questions we believe have not been asked, or at best have been asked superficially, by the JIS.
Other areas were treated similarly:
Risk Aversion
The JIS did not examine risk aversion as a distinct and separate issue, despite the fact that several witnesses and interviewees told the staff that it was a big problem. Indeed, no intelligence or law- enforcement agency escaped being described by its own officials as hampered by an aversion to taking risks of one sort or another.
For instance, at the September 24, 2002 JIS open hearing, a cloaked "Minneapolis FBI Agent" testified about risk aversion in the FBI. He was asked if he thought previous disciplinary actions involving agents making erroneous applications to the Foreign Intelligence Court of Review (the court set up under the Foreign Intelligence Surveillance Act, or FISA) had made agents reluctant to file FISA applications. He responded that these did indeed have a chilling effect. [2]
FBI fears of being seen as committing racial or religious profiling were acknowledged by a Phoenix special agent who attempted to alert FBI headquarters about suspicious individuals seeking pilot training. The special agent's now-famous electronic communication to headquarters recommended that it consider seeking authority to obtain visa information from the State Department on individuals who got visas to attend flight school. The intelligence operations specialists at FBI headquarters who reviewed the "Phoenix Memorandum" told the JIS that they had decided among themselves that seeking that authority raised profiling concerns. FBI qualms in this regard were stimulated by public allegations of racial profiling that were made against FBI agents who questioned two Middle Eastern men who had acted suspiciously on an Air West flight
_______________
2 Statements of a Minneapolis FBI Agent before the joint committees, September 24, 2002.
5
from Phoenix to Washington, D.C. in 1999.
JIS director Eleanor Hill described the latter incident at the September 24, 2002 hearing: "During a physical surveillance of the subject of the Phoenix [electronic communication], the agent determined that he was using a vehicle registered to another individual. In 1999, the owner of the car and an associate of his were detained for trying to gain access to the cockpit of a commercial airliner on a domestic flight. They told the FBI that they thought the cockpit was the bathroom and they accused the FBI of racism." [3]
During the same hearing, Senator Hatch pressed the FBI witnesses on problems brought on by perceived racial profiling. Michael Rolince of the FBI remarked on his colleagues' interactions as they pursued leads on possible terrorist attacks during Y2K celebrations around the world: "I think you only need to go back to the millennium . .. There was a proposal on the table to interview every subject of every full and every preliminary inquiry investigation [regarding Osama Bin Laden] ...and we were concerned about follow-on events for the Y2K. That met with overwhelming resistance by the [Special Agents in Charge] in the field for a lot of different reasons, one of which is we would be hounded unmercifully over the profiling issue." [4]
_______________
3 Written statement of Eleanor Hill, in testimony before the joint committees, September 24, 2002.
4 Michael Rolince, testimony before the joint committees, September 24, 2002.
6
The head of the National Security Agency, Lieutenant General Michael Hayden, told the JIS that, in 2000, his agency found itself having to fend off -- in an unusual public hearing -- Representative Robert Barr's public criticisms. Representative Barr had criticized the National Security Agency for what he believed were inappropriate collection activities. [5]
Many comments on risk aversion alluded to congressional oversight and/or investigations dating back to the Church and Pike investigations of the 1970s. In the 1980s, congressional investigation and litigation involving the FBI's investigation of the Committees in Solidarity with the People of El Salvador led indirectly to newer agents being "warned to be careful that they do not violate religious groups' First Amendment rights." [6] It is quite possible -- though this theme was not fully explored by the JIS -- that a legacy of caution left by these historical episodes contributed to timidity in tackling the Al Qaeda problem before Al Qaeda struck on 9/11.
_______________
5 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject: "October 31, 2002, Questions from Senators Kyl and Roberts."
6 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject: "October 31, 2002, Questions from Senators Kyl and Roberts."
7
A good example of comments that gave prominence to this subject is that of Richard Clarke, the National Security Council counter-terrorism coordinator from 1993 to October, 2001, who discussed in a JIS briefing on June 11, 2002 the atmosphere he would like to see engendered within our intelligence agencies. Mr. Clarke said the ethos should be: "Don't be afraid to make mistakes. Encourage a climate in the military and in the law-enforcement communities and in the CIA that says, perfection is not the goal here; and if you have good intentions and you mess up along the way, you will not be punished as an organization or as an individual. Get away from this risk-averse culture, where one mistake and you are out." He added that "we need a thousand more Colleen Rowleys, and you are never going to get them until you provide them with some encouragement, both from the Director of the FBI, from the President of the United States and, most importantly, from the Congress. ...elieve it or not, a lot of people in the executive branch are scared stiff about being up in front of a congressional committee." [7]
Changing the culture of risk aversion in these agencies is a major undertaking. It should be a central focus of any corrective actions we may attempt following this investigation. Yet the Report seems only to document the "fact" of risk aversion, rather than get at why it existed. Without knowing the causes, how can we be certain the conditions that led to it in the 1990s have been corrected? The two congressional intelligence committees should be very careful when it comes to recommending that individuals who were "to blame" for 9/11-related failures be aggressively punished, lest we promote the scapegoating of junior government employees by those who actually bore more responsibility. (See Recommendation #16.)
[b]Insufficient Resources
Throughout this investigation, top intelligence officials cited a lack of money and people, in the years before the 9/11 attacks. One CIA witness described intelligence resources fighting terrorism as "a platoon in a brigade-sized field and doing the best they can." [8] This was known, yet little was done to correct it.
_______________
7 Richard Clarke, testimony before the joint committees, June 11,2002.
8 Statements of a CIA witness before the joint committees, September 20, 2002.
8
During the 1990s, intelligence community budgets stayed roughly even in constant dollars, or slightly declined. Overall capabilities declined. Primarily by taking from other budgets, counter- terrorism funds doubled. The Report states that, "in spite of increased counter-terrorism resources, the overall decreases in Intelligence Community resources made it difficult to expand the counter- terrorism effort significantly to meet the growing threat . ... The number of people working on terrorism rose steadily, despite overall decreases in Intelligence Community staffing. Nonetheless, the number of people in counter-terrorism remained small." [9]
One notices a lack of clarity here. The Report spends many pages cataloging why it is difficult to pinpoint how much money was expended on counter-terrorism; yet the document does not really grapple with the contradiction between the high-ranking officials' complaints about inadequate resources and the fact that, according to the Office of Management and Budget, the intelligence agencies usually got what they asked for. Some excerpts describing this disconnect follow:
_______________
9 Final JIS Report, Tab E, pp. 2-3.
10 Final JIS Report, Tab E, p. 7.
11Final JIS Report, Tab E, p. 9.
12 Final JIS Report, Tab E, p. 10.
9
"The FBI usually received more -- at times far more -- than the amounts the President initially requested from Congress." [14]
_______________
13 Final JIS Report, Tab E, p. 12.
14 Final JIS report, Tab E, p. 11.
10
Yet officials from the intelligence agencies contended after the fact that the enhanced resources they received were not sufficient to meet the growing threat. One officer of the Counter-Terrorism Center claimed she was told when appeals for more resources were rejected: "People [will] have to die for them to get resources." [16]
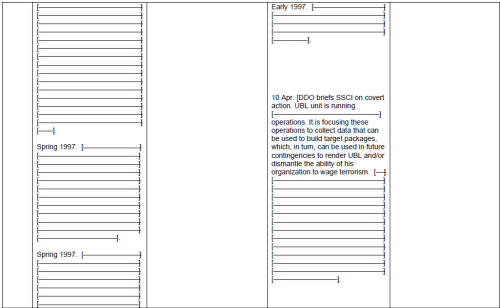
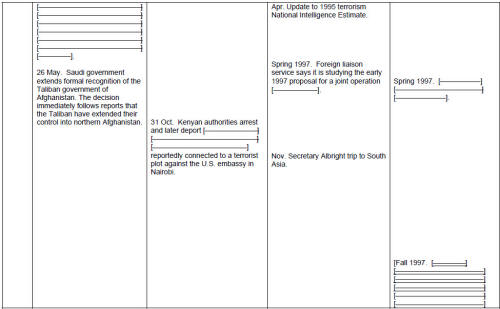
Director of Central Intelligence George Tenet is in a rare and privileged position of having a personal audience with the President on a near-daily basis. When the Director of Central Intelligence declares war on Al Qaeda, as George Tenet did in 1998, we should see a dramatic effect. Did he press his case with President Clinton that he did not have enough people or resources? What he said in written testimony before the joint committees on October 17, 2002 is that the CIA prepared a policy-and-objectives statement in early 1997 that reflected a determination to go on the offensive against terrorism. Director Tenet:
"The submission outlined our Counter-Terrorism Center's offensive operations, listing as their goals to 'render the masterminds, disrupt terrorist infrastructure, infiltrate terrorist groups, and work with foreign partners. ' ... It highlighted efforts to work with the FBI in a bold bid to destroy the infrastructure of major terrorist groups worldwide.
_______________
15 Final JIS Report, Tab E, p. 19.
16 Final JIS Report, Tab E, p. 14.
11
"...The FY99 submission -- prepared in early 1998 -- continued the trend in requesting a substantial funding increase for offensive operations against terrorism. ... The FY 2000 budget submission prepared in early 1999 described Bin Laden as 'the most significant individual sponsor of Sunni Islamic extremism and terrorism activity in the world today.' Our FY 2000 submission noted our use of a wide range of operational techniques, joint operations with foreign partners, and the recruitment of well-placed agents." [17]
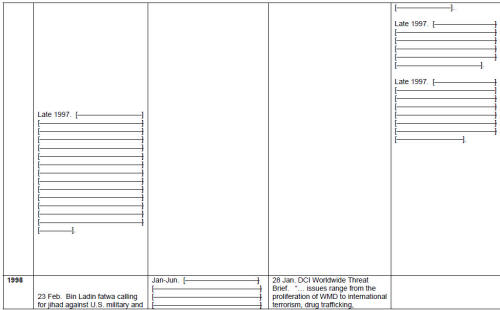
Director Tenet continued: "Despite these clear intentions and the daring activities that went with them, I was not satisfied that we were doing all we could against this target. In 1998, I told key leaders at CIA and across the intelligence community that we should consider ourselves 'at war' with UBL. I ordered that no effort or resource be spared in prosecuting this war. In early 1999, I ordered a baseline review of CIA's operational strategy against Bin Laden." [18]
In spite of Director Tenet's claims of "daring activities" and not being satisfied that the CIA was doing all it could against terrorists, the JIS found that "There was a reluctance to take risks in which CIA officers might die." [19]
But, back to the question of resources: What did Tenet do to follow up? Did he request more? Were the requests rejected? By whom? Why? If requests for money had been granted, would that have made any difference? And finally, how much has changed since 9/11 ?
_______________
17 George Tenet, testimony before the joint committees, October 17, 2002.
18 Ibid.
19 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject, "October 31, 2002, Questions from Senators Kyl and Roberts."
12
The JIS was able to get the personnel and fiscal counter-terrorism requests of the FBI dating to the early 1990s. These contained the total number of additional positions or monies requested by the FBI of the Department of Justice, requested by the Department of Justice of the Office of Management and Budget, requested by the OMB of Congress, and enacted by Congress. Within these data are indications of irrational, ad hoc budgeting and funding decisions. [20] The positions approved by each entity in turn, as the requests wended their way from the FBI to Congress, sometimes showed wild disparities and inconsistencies. Yet the root causes for this remain unexplored. Without this information, the JIS contended it could not determine the "failure mechanisms" in the budgeting process. What was the impact on counter-terrorism as a result of the administration's budget requests and congressional responses, and what changes would be required to rectify the problems? The JIS Report does not provide answers.
A Flawed Legal/Institutional Framework
It is also evident that some of the pre-9/11 failings were caused by government officials operating under unclear authorities. The joint committees heard testimony from a number of senior officers from the intelligence agencies, the National Security Council, and the Pentagon. The committees were presented with divergent perspectives on exactly what authorities existed in our efforts to take the war to the terrorists.
_______________
20 Final JIS Report, Chart 1.5 ("FBI Resource Requests"); Joint Inquiry Staff briefing to the joint committees, "An Overview of Counter-Terrorism Resources, " Slide #6 ("FBI Requests for Additional Counter-Terrorism Resources and the DOJ, OMB, and Congressional Response").
13
National Security Council officials said they provided all the tools, both physical and legal, to do the job; intelligence agency officials said the National Security Council provided neither. Stated former National Security Advisor Anthony Lake: "In June, 1995, Presidential Decision Directive 39 mandated increased efforts to capture terrorists abroad." [21] His successor as National Security Advisor, Sandy Berger, said in response to our questions for the record: "President Clinton approved every strike or other action against bin Laden proposed by his intelligence, military, and national security advisors." [22]
On the other side of this divide, Members heard from intelligence officials, such as Cofer Black, former chief of the Counter-Terrorism Center, comments about being hampered by a lack of operational flexibility. Mr. Black: "I want to make this very clear. I do not feel that I had sufficient authorities to do the best job that we could." [23] He underlined this point at a later hearing: " All I want to say is that there was before 9/11 and after 9/11. After 9/11 the gloves came off." [24]
While the details of this debate remain classified, the JIS Report, as it does in so many other respects, documents the fact that there were discordant views without digging to find the point of failure that allowed this confusion to persist.
_______________
21 Written statement of Anthony Lake, in testimony before the joint committees, September 19, 2002.
22 Memorandum from Sandy Berger to Senator Graham dated November 4, 2002, Subject: "Reply to Additional Joint Inquiry Questions."
23 Cofer Black, statements before the joint committees, September 12, 2002.
24 Written statement of Cofer Black, in testimony before the joint committees, September 26, 2002.
14
Uncertainty about a particular legal authority is shown in the FBI's decision-making surrounding the search of Zaccarias Moussaoui's computer. Minneapolis agent Rowley thought a FISA warrant could be obtained. Headquarters personnel thought not, because it was not clear Moussaoui was acting on behalf of an international terrorist organization. [25] More in-depth analysis of this issue might have resulted in a recommendation by our committees to revisit the legal definition, under FISA, of a "foreign power" -- a term that currently only includes foreign governments or international terrorist organizations. A warrant for surveillance of an individual is only granted under FISA if a court finds probable cause to believe the target of the warrant is linked either to a foreign government or an established organization. This may have made sense when the Foreign Intelligence Surveillance Act was enacted during the Cold War, but apparently, as noted, U.S. authorities did not try to obtain a FISA warrant to search Moussaoui in the summer of 2001 because the FBI could not prove he was linked to a specific terrorist group. Senator Kyl has offered a three-word change to the statute that would permit a FISA warrant to be obtained if the person suspected of terrorist activity is a foreign person. This change is supported by the Department of Justice.
Another change in the law that could improve the institutional framework would be further congressional legislation to enable the U.S. Government to dete:r and punish unauthorized disclosure of security-related information.
Leadership Failures
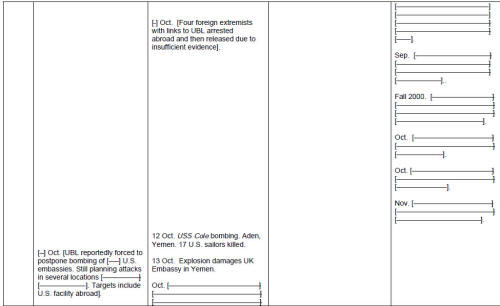
Al Qaeda's attack on Washington and New York occurred after a long period of poor leadership at the highest levels of the U.S. Government regarding terrorism. Despite repeated assaults on the United States and its interests -- the 1993 World Trade Center attack, the bombing of the American embassies in Kenya and Tanzania in 1998, the attack on the USS Cole in 2000, to name a few -- the U.S. Government was still unwilling to treat terrorism as a true national security issue until 9/11. Indeed, the previous administration strove mightily to treat terrorism strictly as a law- enforcement issue, often thinking in terms of what evidence could be gathered on
_______________
25 "F.B.I. Denial of Search Warrant for Suspect's Belongings Is at Center of Inquiries," Philip Shenon, New York Times, June 7, 2002.
15
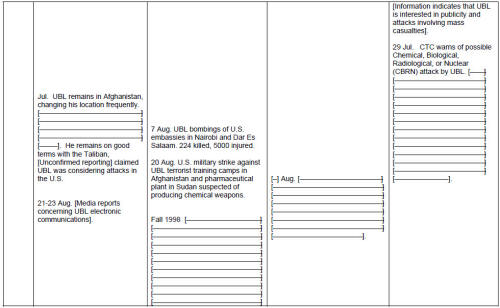
terrorists that would hold up in a court of law. Even when we did respond with military force -- sending cruise missiles into Afghanistan and Sudan after the 1998 embassy attacks, for instance -- it smacked of doing something for show, rather than a real attempt to treat the terrorist threat for what it is -- a war.
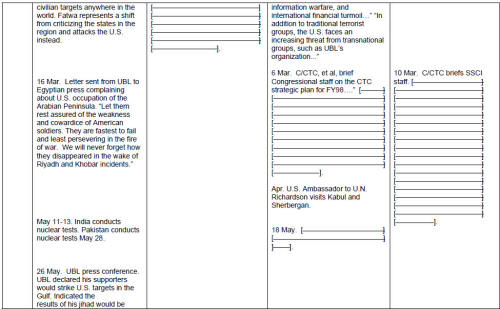
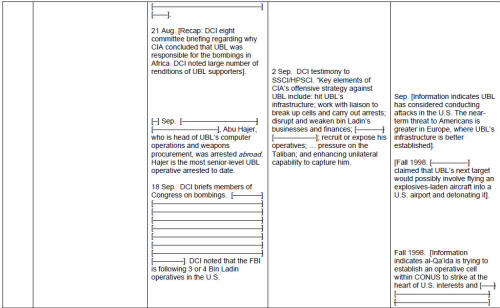
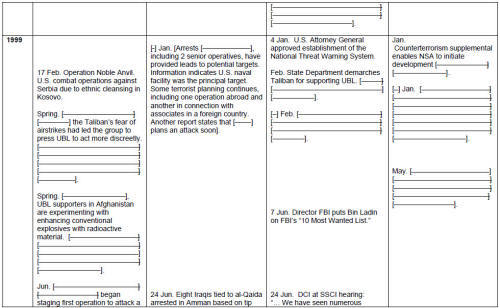
But these leadership failures at the political level do not absolve the decision-makers at the intelligence agencies of their own failures. The problem of inadequate allocation of resources, for example, appears to be a result of confused leadership in the intelligence community. Just about every person interviewed indicated that, before 9/11, he or she was overtasked and undermanned. Yet the Counter-Terrorism "Center" evidently did not fully use the resources already in the community. Analysts from agencies outside the CIA indicated to the JIS that they were not being tapped to assist counter-terrorism work inside the Counter-Terrorism Center. JIS information indicates that the Defense Intelligence Agency and the Federal Aviation Administration offered analytic support to the chief of the Counter-Terrorism Center, but both offers were rebuffed. [26] So, in spite of a 1998 DCI declaration of war on Al Qaeda, two key organizations were not allowed to fully throw their support behind the anti-terror effort. In this connection, Director Tenet stated before our committee -- apparently with pride -- that, by 2001, the Counter-Terrorism Center "had 30 officers from more than a dozen agencies on board, [constituting] ten percent of its staff complement at that time." [27] This means the CIA accounted for 90 percent of the personnel at the Counter-Terrorism Center, and the "more than a dozen" other agencies were only allotted the remaining 10 percent of the billets. Clearly, the Counter- Terrorism Center, created as an intelligence community entity to fuse information and analysis, did not fully leverage the assets resident throughout the law-enforcement and intelligence communities.
Instead we had fragmented counter-terrorism analytic centers at CIA headquarters, at the Pentagon, and at various FBI locations. The failure to concert the community's activities had
_______________
26 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject: "October 31, 2002, Questions from Senators Kyl and Roberts."
27 Written statement of George Tenet, in testimony before the joint committees, October 17, 2002.
16
severe consequences. Did the intelligence community fail the Director of Central Intelligence by not offering more support to the Counter-Terrorism Center, or did the Director of Central Intelligence fail the Counter-Terrorism Center by not bringing in more government-wide talent and skills?
Only after 9/11 did the various intelligence and law-enforcement entities begin to put aside their parochialism and work together in a more productive manner. With better leadership of the intelligence community, this condition would not have been prevalent before 9/11. It would not have taken that monumental disaster for our nation to get the members of the community to cooperate with one another.
One of the purposes of the Joint Inquiry, as stated in the preamble to the House and Senate committees' "Initial Scope" document, was to "lay the basis for assessing the accountability of institutions and officials of government." The JIS Report, however, apparently fails to identify which officials within the intelligence community had responsibility, before 9/11, for strategic and tactical warning of terrorist activity. Instead, Recommendation # 16 suggests that discovering who is accountable should be the job of the Inspectors General of the various agencies.
Inadequate Scope
The failures that led to 9/11 occurred not only in the intelligence community. The JIS was selective about what threads of inquiry it was willing to follow beyond the intelligence community. Failure to examine the State Department's visa-issuance process must rank as the most glaring of these omissions because the answer to the question -- could 9/11 have been prevented -- is yes, if State Department personnel had merely followed the law and not granted non-immigrant visas to 15 of the 19 hijackers in Saudi Arabia.
We repeat: If our own laws regarding the issuance of visas had been followed by the State Department, most of the hijackers would not have been able to obtain visas, and 9/11 would not have happened. Because the entire culture of the State Department is geared toward facilitating smooth relations with foreign governments, State Department personnel have tended to ignore the potential effect of their practices on national security.
An October, 2002 report of the General Accounting Office found that, before 9/11, there was among U .S. consular officers abroad a wide divergence of opinions and practices regarding
17
"the authority of consular officers to deny questionable applicants a visa; the role of the visa process in ensuring national security; and the types of changes . .. appropriate given the need for heightened border security." [28]
Section 214(b) of the Immigration and Nationality Act essentially creates a presumption against the issuance of visas to single young men without visible means of support. Consular officers are empowered with broad authority to deny visas in cases where the applicant fails to overcome this presumption. Section 214(b), which pertains to non-immigrant visas, specifically provides that applicants for such visas must demonstrate that they: 1) have a residence abroad and strong ties to a country that they have no intention of abandoning; 2) intend to leave the United States in a timely manner; and 3) intend to engage in legitimate activities related to the non-immigrant category.
_______________
28 "Border Security: Visa Process Should Be Strengthened as an Antiterrorism Tool," General Accounting Office, October, 2002, p. 3.
18
The failure of several of the terrorist hijackers, including the ringleader, Mohammed Atta, to completely fill out their applications provided ample reason for denying the visas. Only one of the 15 terrorists who were from Saudi Arabia provided an actual address; the rest listed only general locations, such as "California," "New York," "Hotel D.C." and "Hotel." [29] Only three of the 15 provided the name and street address of present employer or school as required on the application. Only one of these applications had additional documentation or explanatory notes provided by a consular officer that addressed any discrepancy or problem with the original application.
It was the official position of the State Department's Bureau of Consular Affairs for over a year, that 13 of the 15 terrorists from Saudi Arabia had been personally interviewed and that there was nothing in their visa applications or in the interviews that should have prevented issuance of their visas. According to the GAO, however, only two of the Saudi applicants were actually interviewed, and all 19 hijackers had substantial omissions and inconsistencies on their visa applications that should have raised concerns about why they wanted visas.
_______________
29 "Visas for Terrorists," Joel Mowbray, National Review, October 28, 2002.
19
The GAO reported that these applicants were presumed to be eligible based upon pre-9/11 internal State Department policies that stressed that all applicants from Saudi Arabia and the United Arab Emirates were to be considered "good cases" and, therefore, exempt from interviews. Moreover, the GAO noted that applicants from these two countries were not required to "complete their applications or [provide] supporting documentation." [30] Why was this so? The pervasiveness in Saudi Arabia of Wahhabism, a radical, anti-American variant of Islam, was well-known before 9/11. The JIS should have inquired why the country of Saudi Arabia was given such preferential treatment by the State Department and whether the intelligence agencies were complicit in the policy.
III. Comments on Recommendations
When there is a crisis, there is a tendency to look for easy solutions. A case in point is the first and most publicized Recommendation to come out of this investigation: the creation of a new "Director of National Intelligence." Good policies, good leadership, adequate resources, and will can better protect the American people from terrorism than simply creating new offices and rearranging organizational charts. And, as we have attempted to show, policy, resources, and leadership were issues that were not treated in sufficient depth by the JIS. It is not at all clear that a new intelligence "czar" could succeed where the Director of Central Intelligence has not. For that matter, the Report does not even conclude that DCI Tenet or any predecessor DCI did fail. The disconnect between the JIS' investigative efforts and the Recommendation supposedly based on them is remarkable.
On the merits of the "Director of National Intelligence" idea itself, we would concur with some of the points made by Vice Chairman Shelby in his Statement of Additional Views. Separating the job of the head of the intelligence community from the directorship of the CIA is an idea of some value. It has been endorsed by a number of post-Cold War studies of intelligence-community reform. However, we in the House and Senate intelligence committees have not yet deliberated enough on this question to draw any conclusions.
_______________
30 GAO report, p. 17.
20
As indicated above, we are particularly troubled by the JIS Report's Recommendation #16, calling for lower-level personnel to be held accountable by the various agencies' Inspectors General. It is doubtful whether this would improve the functioning of the intelligence agencies. Accountability of this kind would, in our view, have a troubling result: exacerbating what so many people quoted herein cited as a pervasive problem, namely, aversion to risk. Accountability of those at the very top is what is needed; it alone produces accountability at the intervening levels, and among officers in the field who run down the leads to find terrorists.
It would be expecting too much to think that U.S. authorities should have predicted that the attack of 9/11 would come. But the level of dysfunction in the security and intelligence agencies comes as a shock to Americans, who had faith in the expertise of the intelligence community. To restore that faith it must improve its performance, and in this regard, the proposition "First things first" is only common sense. Our duty to understand precedes our ability to improve. The JIS Report, in not fully coming to terms with what produced the intelligence failures it identified, left that duty unfulfilled. These Additional Views are offered not to criticize those who worked very hard under difficult circumstances to file a Report by the end of the 107th Congress, but to provide a more complete perspective for those who are charged to further investigate the terrorist attacks of September 11, 2001.
21
A JOINT INQUIRY STAFF REPORT ADDITIONAL VIEWS SENATOR JON KYL, SENATOR PAT ROBERTS
I. The Need for Additional Views
The Report is a product of the Joint Inquiry Staff (JIS), not the Senators and Representatives who sit, respectively, on the Senate Select Committee on Intelligence (SSCI) and the House Permanent Select Committee on Intelligence (HPSCI). The Chairman and Vice Chairman of the SSCI and the Chairman and Ranking Member of the HPSCI (the "Big Four") made most decisions and supervised the JIS. The JIS should be commended for putting together the first official account of the events leading up to the terrorist attacks of September 11, 2001.
It is difficult, however, for rank-and-file Members of the two committees to know how thorough or accurate the Report is because of the way the JIS and the "Big Four" conducted the inquiry, withholding information and decisions from the Members and SSCI and HPSCI staff throughout the process. While the Report should be a useful historical document on which to base further inquiries, we cannot vouch for its contents.
Beyond that, the investigation was deficient for what it did not include. While intelligence community failures were identified, they were presented frequently in a mode of "mistakes were made" rather than as the beginning of an inquiry as to why they were made.
After prodding by several Senators, some underlying causes of these failures were identified, but even then, they were not further probed to determine what might have been done differently. And the fact that the prodding was necessary illustrates our concern that the JIS either ran out of time or did not have the inclination or instruction to examine, for instance, why U.S. government agencies were risk-averse, who is responsible for the inadequate resources devoted to counter-terrorism efforts, why legal authorities were so confusing, and why leadership was so lacking. Without this examination, the Report will be of limited value in determining "lessons learned."
The record should also reflect some of the differences in opinion among Members on how the Report was (or should have been) prepared. The inquiry was conducted and overseen in a way that left rank-and-file Members at a distinct disadvantage, and left insufficient time to examine many relevant issues. The final draft of the Report -- which is several hundred pages long and highly classified -- was delivered to Members four days before the one and only meeting scheduled for its consideration, when most Members were out of town. There was no debate about the Report, only about the Recommendations. But there was little basis for debate since the product was strictly the work of the JIS -- more like an Inspector General's report than a typical congressional committee report. Throughout the process, rank-and-file Members complained about irregularities. Specific examples include:
Upon instructions from the Chairmen -- and in violation of SSCI rules -- the JIS often failed to tell Members and staff of important non-compartmented information it discovered in a timely manner.
Information relating to open hearings -- such as the JIS staff statement and witness statements -- were routinely provided only late on the night before the hearing.
Committee staff, and sometimes even the staff directors, were often excluded from meetings of the "Big Four," whose decisions were often made without consultation. Members' liaison staff, and, therefore, the Members themselves, were in the dark about these decisions.
Despite repeated requests, records of JIS interviews with key witnesses conducted in the spring were not made available to committee staff for review until fall, when the final draft report was already in the late drafting stages.
Over the strong objections of several Members, and key officials of the intelligence community, the "Big Four" scheduled a series of open hearings that sidetracked the ongoing investigation from mid-July to late October.
Here is a representative example of the lack of meaningful rank-and-file input into "Big
2
Four" decisions: During the JIS hearing of September 24, 2002 on "U.S. Government Counter- Terrorism Organizations and the Evolution of the Terrorist Threat," Chairman Goss asked unanimous consent to include in the record several documents relating to that day's hearing. However, among these documents were requests to the administration regarding its decision not to declassify certain information. These requests from the "Big Four" were made without consultation with the rank-and-file Members -- a fact that Senator Kyl noted for the record at that time. He stated: "Mr. Chairman, I have no objection, but I would like the record to note that the matter that the four of you spoke to is not a matter that has been discussed by the full membership of the committee. Therefore, at least I for one am in no position to judge whether the requests that you have made are warranted or not."
The holding of open hearings was particularly frustrating. The decision to hold them was apparently made by the "Big Four" despite the concerns of the JIS and the objections of other Senators. The JIS was forced to focus on them for three months, and from there had to go right into drafting the Report in order to meet the year-end deadline.
Several Members voiced their opposition to holding open hearings before the investigative work was completed and the Report written (and, we had supposed, agreed to). We objected, mostly in closed committee business meetings, that it was premature to convene open hearings before the investigation was complete. And indeed, at the point when the JIS began preparing for them (July, 2002), its investigations into the causes of 9/11 largely ground to a halt. Due to dramatic media leaks and the potential for further compromise, intelligence agencies "pushed back" against open hearings, causing further friction with the JIS investigation.
The hearings distracted these agencies, our "front line troops" on the war on terrorism, and they distracted Members and congressional staff from our traditional oversight responsibilities. They also, in our view and the view of Vice Chairman Shelby, publicly revealed a lot of sensitive information from which our enemies could profit. Most of the information presented had already been revealed in closed hearings, which were far more productive because those who participated could delve freely into classified information.
Key figures in our counter-terrorism efforts were unnecessarily compromised by these public hearings. A case in point is the Arizona resident whose identity came out in the media.
3
His name and face were even broadcast on Al-Jazeera. His family was harassed and was potentially in danger from extremists. Our hard-working people deserve better treatment than that. We should have been more circumspect about publicly releasing results before the investigation was complete and the two intelligence committees had had a chance to adequately review the final Report.
II. Deficiencies in the Report
These inadequacies in the process resulted in a Report that falls well short of addressing the core problems that led to 9/11. Because the fundamental problems that led to 9/11 are almost certainly rooted in poor policy and inadequate leadership, the investigation should have delved more deeply into conflicting interpretations of legal authorities (including presidential directives), budget allocations, institutional attitudes, and other key areas. Only penetrating these areas will tell us how policymakers, including Congress, contributed to the failures the Report identifies. In other words, only such a thorough exercise will help us to make sure the failures are not repeated.
What best shows the tendency of the JIS investigation to go to the water's edge but no farther is that, in the Report, there is a pronounced tendency to identify problems as "facts," or "realities," rather than as matters to be plumbed for underlying causes. For instance, we have the following JIS testimony to the joint committees: "The 1996 Khobar Towers attack, the 1998 African embassies attacks, and the 2000 USS Cole attack led the Departments of State and Defense to focus heavily on force protection, but not on meeting the challenge of Afghanistan, even though they recognized the dangers emanating from terrorist camps there." [1] So, the problem of Afghanistan as a haven for terrorists was widely recognized. But the CIA and FBI lacked the means, and also lacked a plan, to go after training camps in Afghanistan in a comprehensive manner. It would be reasonable to wonder at this point: What efforts were made to penetrate various groups in Afghanistan (or if there were efforts, why were they not successful), and why
_______________
1 Emphasis added. Written statement of Eleanor Hill, in testimony before a hearing of the House Permanent Select Committee on Intelligence and the Senate Select Committee on Intelligence (hereafter "the joint committees"), October 8, 2002.
4
was there no attempt to beef up the military for a comprehensive response? The record shows that little effort was made to effectively utilize the military even after President Clinton's post-embassy bombing declaration in 1998 that "there will be no sanctuary for terrorists." Again, it is reasonable to ask why actions did not match words. These are questions we believe have not been asked, or at best have been asked superficially, by the JIS.
Other areas were treated similarly:
Risk Aversion
The JIS did not examine risk aversion as a distinct and separate issue, despite the fact that several witnesses and interviewees told the staff that it was a big problem. Indeed, no intelligence or law- enforcement agency escaped being described by its own officials as hampered by an aversion to taking risks of one sort or another.
For instance, at the September 24, 2002 JIS open hearing, a cloaked "Minneapolis FBI Agent" testified about risk aversion in the FBI. He was asked if he thought previous disciplinary actions involving agents making erroneous applications to the Foreign Intelligence Court of Review (the court set up under the Foreign Intelligence Surveillance Act, or FISA) had made agents reluctant to file FISA applications. He responded that these did indeed have a chilling effect. [2]
FBI fears of being seen as committing racial or religious profiling were acknowledged by a Phoenix special agent who attempted to alert FBI headquarters about suspicious individuals seeking pilot training. The special agent's now-famous electronic communication to headquarters recommended that it consider seeking authority to obtain visa information from the State Department on individuals who got visas to attend flight school. The intelligence operations specialists at FBI headquarters who reviewed the "Phoenix Memorandum" told the JIS that they had decided among themselves that seeking that authority raised profiling concerns. FBI qualms in this regard were stimulated by public allegations of racial profiling that were made against FBI agents who questioned two Middle Eastern men who had acted suspiciously on an Air West flight
_______________
2 Statements of a Minneapolis FBI Agent before the joint committees, September 24, 2002.
5
from Phoenix to Washington, D.C. in 1999.
JIS director Eleanor Hill described the latter incident at the September 24, 2002 hearing: "During a physical surveillance of the subject of the Phoenix [electronic communication], the agent determined that he was using a vehicle registered to another individual. In 1999, the owner of the car and an associate of his were detained for trying to gain access to the cockpit of a commercial airliner on a domestic flight. They told the FBI that they thought the cockpit was the bathroom and they accused the FBI of racism." [3]
During the same hearing, Senator Hatch pressed the FBI witnesses on problems brought on by perceived racial profiling. Michael Rolince of the FBI remarked on his colleagues' interactions as they pursued leads on possible terrorist attacks during Y2K celebrations around the world: "I think you only need to go back to the millennium . .. There was a proposal on the table to interview every subject of every full and every preliminary inquiry investigation [regarding Osama Bin Laden] ...and we were concerned about follow-on events for the Y2K. That met with overwhelming resistance by the [Special Agents in Charge] in the field for a lot of different reasons, one of which is we would be hounded unmercifully over the profiling issue." [4]
_______________
3 Written statement of Eleanor Hill, in testimony before the joint committees, September 24, 2002.
4 Michael Rolince, testimony before the joint committees, September 24, 2002.
6
The head of the National Security Agency, Lieutenant General Michael Hayden, told the JIS that, in 2000, his agency found itself having to fend off -- in an unusual public hearing -- Representative Robert Barr's public criticisms. Representative Barr had criticized the National Security Agency for what he believed were inappropriate collection activities. [5]
Many comments on risk aversion alluded to congressional oversight and/or investigations dating back to the Church and Pike investigations of the 1970s. In the 1980s, congressional investigation and litigation involving the FBI's investigation of the Committees in Solidarity with the People of El Salvador led indirectly to newer agents being "warned to be careful that they do not violate religious groups' First Amendment rights." [6] It is quite possible -- though this theme was not fully explored by the JIS -- that a legacy of caution left by these historical episodes contributed to timidity in tackling the Al Qaeda problem before Al Qaeda struck on 9/11.
_______________
5 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject: "October 31, 2002, Questions from Senators Kyl and Roberts."
6 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject: "October 31, 2002, Questions from Senators Kyl and Roberts."
7
A good example of comments that gave prominence to this subject is that of Richard Clarke, the National Security Council counter-terrorism coordinator from 1993 to October, 2001, who discussed in a JIS briefing on June 11, 2002 the atmosphere he would like to see engendered within our intelligence agencies. Mr. Clarke said the ethos should be: "Don't be afraid to make mistakes. Encourage a climate in the military and in the law-enforcement communities and in the CIA that says, perfection is not the goal here; and if you have good intentions and you mess up along the way, you will not be punished as an organization or as an individual. Get away from this risk-averse culture, where one mistake and you are out." He added that "we need a thousand more Colleen Rowleys, and you are never going to get them until you provide them with some encouragement, both from the Director of the FBI, from the President of the United States and, most importantly, from the Congress. ...elieve it or not, a lot of people in the executive branch are scared stiff about being up in front of a congressional committee." [7]
Changing the culture of risk aversion in these agencies is a major undertaking. It should be a central focus of any corrective actions we may attempt following this investigation. Yet the Report seems only to document the "fact" of risk aversion, rather than get at why it existed. Without knowing the causes, how can we be certain the conditions that led to it in the 1990s have been corrected? The two congressional intelligence committees should be very careful when it comes to recommending that individuals who were "to blame" for 9/11-related failures be aggressively punished, lest we promote the scapegoating of junior government employees by those who actually bore more responsibility. (See Recommendation #16.)
[b]Insufficient Resources
Throughout this investigation, top intelligence officials cited a lack of money and people, in the years before the 9/11 attacks. One CIA witness described intelligence resources fighting terrorism as "a platoon in a brigade-sized field and doing the best they can." [8] This was known, yet little was done to correct it.
_______________
7 Richard Clarke, testimony before the joint committees, June 11,2002.
8 Statements of a CIA witness before the joint committees, September 20, 2002.
8
During the 1990s, intelligence community budgets stayed roughly even in constant dollars, or slightly declined. Overall capabilities declined. Primarily by taking from other budgets, counter- terrorism funds doubled. The Report states that, "in spite of increased counter-terrorism resources, the overall decreases in Intelligence Community resources made it difficult to expand the counter- terrorism effort significantly to meet the growing threat . ... The number of people working on terrorism rose steadily, despite overall decreases in Intelligence Community staffing. Nonetheless, the number of people in counter-terrorism remained small." [9]
One notices a lack of clarity here. The Report spends many pages cataloging why it is difficult to pinpoint how much money was expended on counter-terrorism; yet the document does not really grapple with the contradiction between the high-ranking officials' complaints about inadequate resources and the fact that, according to the Office of Management and Budget, the intelligence agencies usually got what they asked for. Some excerpts describing this disconnect follow:
"DCI Tenet testified that the CIA regularly asked OMB for more money, but had little success." [10]
"Agency leaders testified that their requests for resources were sometimes not satisfied, even though Congress appropriated as much or more than the President requested. This is because OMB often reduces agency requests before sending them to Congress." [11]
"In general, CIA appropriations for counter-terrorism met or exceeded the requests that were submitted by the President to Congress." [12]
"[National Security Agency] appropriations consistently met or exceeded Presidential requests to Congress." [13]
_______________
9 Final JIS Report, Tab E, pp. 2-3.
10 Final JIS Report, Tab E, p. 7.
11Final JIS Report, Tab E, p. 9.
12 Final JIS Report, Tab E, p. 10.
9
"The FBI usually received more -- at times far more -- than the amounts the President initially requested from Congress." [14]
_______________
13 Final JIS Report, Tab E, p. 12.
14 Final JIS report, Tab E, p. 11.
10
"Budget requests specifically tied to counter-terrorism were generally approved, according to OMB officials." [15]
Yet officials from the intelligence agencies contended after the fact that the enhanced resources they received were not sufficient to meet the growing threat. One officer of the Counter-Terrorism Center claimed she was told when appeals for more resources were rejected: "People [will] have to die for them to get resources." [16]
Director of Central Intelligence George Tenet is in a rare and privileged position of having a personal audience with the President on a near-daily basis. When the Director of Central Intelligence declares war on Al Qaeda, as George Tenet did in 1998, we should see a dramatic effect. Did he press his case with President Clinton that he did not have enough people or resources? What he said in written testimony before the joint committees on October 17, 2002 is that the CIA prepared a policy-and-objectives statement in early 1997 that reflected a determination to go on the offensive against terrorism. Director Tenet:
"The submission outlined our Counter-Terrorism Center's offensive operations, listing as their goals to 'render the masterminds, disrupt terrorist infrastructure, infiltrate terrorist groups, and work with foreign partners. ' ... It highlighted efforts to work with the FBI in a bold bid to destroy the infrastructure of major terrorist groups worldwide.
_______________
15 Final JIS Report, Tab E, p. 19.
16 Final JIS Report, Tab E, p. 14.
11
"...The FY99 submission -- prepared in early 1998 -- continued the trend in requesting a substantial funding increase for offensive operations against terrorism. ... The FY 2000 budget submission prepared in early 1999 described Bin Laden as 'the most significant individual sponsor of Sunni Islamic extremism and terrorism activity in the world today.' Our FY 2000 submission noted our use of a wide range of operational techniques, joint operations with foreign partners, and the recruitment of well-placed agents." [17]
Director Tenet continued: "Despite these clear intentions and the daring activities that went with them, I was not satisfied that we were doing all we could against this target. In 1998, I told key leaders at CIA and across the intelligence community that we should consider ourselves 'at war' with UBL. I ordered that no effort or resource be spared in prosecuting this war. In early 1999, I ordered a baseline review of CIA's operational strategy against Bin Laden." [18]
In spite of Director Tenet's claims of "daring activities" and not being satisfied that the CIA was doing all it could against terrorists, the JIS found that "There was a reluctance to take risks in which CIA officers might die." [19]
But, back to the question of resources: What did Tenet do to follow up? Did he request more? Were the requests rejected? By whom? Why? If requests for money had been granted, would that have made any difference? And finally, how much has changed since 9/11 ?
_______________
17 George Tenet, testimony before the joint committees, October 17, 2002.
18 Ibid.
19 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject, "October 31, 2002, Questions from Senators Kyl and Roberts."
12
The JIS was able to get the personnel and fiscal counter-terrorism requests of the FBI dating to the early 1990s. These contained the total number of additional positions or monies requested by the FBI of the Department of Justice, requested by the Department of Justice of the Office of Management and Budget, requested by the OMB of Congress, and enacted by Congress. Within these data are indications of irrational, ad hoc budgeting and funding decisions. [20] The positions approved by each entity in turn, as the requests wended their way from the FBI to Congress, sometimes showed wild disparities and inconsistencies. Yet the root causes for this remain unexplored. Without this information, the JIS contended it could not determine the "failure mechanisms" in the budgeting process. What was the impact on counter-terrorism as a result of the administration's budget requests and congressional responses, and what changes would be required to rectify the problems? The JIS Report does not provide answers.
A Flawed Legal/Institutional Framework
It is also evident that some of the pre-9/11 failings were caused by government officials operating under unclear authorities. The joint committees heard testimony from a number of senior officers from the intelligence agencies, the National Security Council, and the Pentagon. The committees were presented with divergent perspectives on exactly what authorities existed in our efforts to take the war to the terrorists.
_______________
20 Final JIS Report, Chart 1.5 ("FBI Resource Requests"); Joint Inquiry Staff briefing to the joint committees, "An Overview of Counter-Terrorism Resources, " Slide #6 ("FBI Requests for Additional Counter-Terrorism Resources and the DOJ, OMB, and Congressional Response").
13
National Security Council officials said they provided all the tools, both physical and legal, to do the job; intelligence agency officials said the National Security Council provided neither. Stated former National Security Advisor Anthony Lake: "In June, 1995, Presidential Decision Directive 39 mandated increased efforts to capture terrorists abroad." [21] His successor as National Security Advisor, Sandy Berger, said in response to our questions for the record: "President Clinton approved every strike or other action against bin Laden proposed by his intelligence, military, and national security advisors." [22]
On the other side of this divide, Members heard from intelligence officials, such as Cofer Black, former chief of the Counter-Terrorism Center, comments about being hampered by a lack of operational flexibility. Mr. Black: "I want to make this very clear. I do not feel that I had sufficient authorities to do the best job that we could." [23] He underlined this point at a later hearing: " All I want to say is that there was before 9/11 and after 9/11. After 9/11 the gloves came off." [24]
While the details of this debate remain classified, the JIS Report, as it does in so many other respects, documents the fact that there were discordant views without digging to find the point of failure that allowed this confusion to persist.
_______________
21 Written statement of Anthony Lake, in testimony before the joint committees, September 19, 2002.
22 Memorandum from Sandy Berger to Senator Graham dated November 4, 2002, Subject: "Reply to Additional Joint Inquiry Questions."
23 Cofer Black, statements before the joint committees, September 12, 2002.
24 Written statement of Cofer Black, in testimony before the joint committees, September 26, 2002.
14
Uncertainty about a particular legal authority is shown in the FBI's decision-making surrounding the search of Zaccarias Moussaoui's computer. Minneapolis agent Rowley thought a FISA warrant could be obtained. Headquarters personnel thought not, because it was not clear Moussaoui was acting on behalf of an international terrorist organization. [25] More in-depth analysis of this issue might have resulted in a recommendation by our committees to revisit the legal definition, under FISA, of a "foreign power" -- a term that currently only includes foreign governments or international terrorist organizations. A warrant for surveillance of an individual is only granted under FISA if a court finds probable cause to believe the target of the warrant is linked either to a foreign government or an established organization. This may have made sense when the Foreign Intelligence Surveillance Act was enacted during the Cold War, but apparently, as noted, U.S. authorities did not try to obtain a FISA warrant to search Moussaoui in the summer of 2001 because the FBI could not prove he was linked to a specific terrorist group. Senator Kyl has offered a three-word change to the statute that would permit a FISA warrant to be obtained if the person suspected of terrorist activity is a foreign person. This change is supported by the Department of Justice.
Another change in the law that could improve the institutional framework would be further congressional legislation to enable the U.S. Government to dete:r and punish unauthorized disclosure of security-related information.
Leadership Failures
Al Qaeda's attack on Washington and New York occurred after a long period of poor leadership at the highest levels of the U.S. Government regarding terrorism. Despite repeated assaults on the United States and its interests -- the 1993 World Trade Center attack, the bombing of the American embassies in Kenya and Tanzania in 1998, the attack on the USS Cole in 2000, to name a few -- the U.S. Government was still unwilling to treat terrorism as a true national security issue until 9/11. Indeed, the previous administration strove mightily to treat terrorism strictly as a law- enforcement issue, often thinking in terms of what evidence could be gathered on
_______________
25 "F.B.I. Denial of Search Warrant for Suspect's Belongings Is at Center of Inquiries," Philip Shenon, New York Times, June 7, 2002.
15
terrorists that would hold up in a court of law. Even when we did respond with military force -- sending cruise missiles into Afghanistan and Sudan after the 1998 embassy attacks, for instance -- it smacked of doing something for show, rather than a real attempt to treat the terrorist threat for what it is -- a war.
But these leadership failures at the political level do not absolve the decision-makers at the intelligence agencies of their own failures. The problem of inadequate allocation of resources, for example, appears to be a result of confused leadership in the intelligence community. Just about every person interviewed indicated that, before 9/11, he or she was overtasked and undermanned. Yet the Counter-Terrorism "Center" evidently did not fully use the resources already in the community. Analysts from agencies outside the CIA indicated to the JIS that they were not being tapped to assist counter-terrorism work inside the Counter-Terrorism Center. JIS information indicates that the Defense Intelligence Agency and the Federal Aviation Administration offered analytic support to the chief of the Counter-Terrorism Center, but both offers were rebuffed. [26] So, in spite of a 1998 DCI declaration of war on Al Qaeda, two key organizations were not allowed to fully throw their support behind the anti-terror effort. In this connection, Director Tenet stated before our committee -- apparently with pride -- that, by 2001, the Counter-Terrorism Center "had 30 officers from more than a dozen agencies on board, [constituting] ten percent of its staff complement at that time." [27] This means the CIA accounted for 90 percent of the personnel at the Counter-Terrorism Center, and the "more than a dozen" other agencies were only allotted the remaining 10 percent of the billets. Clearly, the Counter- Terrorism Center, created as an intelligence community entity to fuse information and analysis, did not fully leverage the assets resident throughout the law-enforcement and intelligence communities.
Instead we had fragmented counter-terrorism analytic centers at CIA headquarters, at the Pentagon, and at various FBI locations. The failure to concert the community's activities had
_______________
26 Joint Inquiry Staff, Memorandum from the Joint Inquiry Staff to Eleanor Hill, dated November 6, 2002, Subject: "October 31, 2002, Questions from Senators Kyl and Roberts."
27 Written statement of George Tenet, in testimony before the joint committees, October 17, 2002.
16
severe consequences. Did the intelligence community fail the Director of Central Intelligence by not offering more support to the Counter-Terrorism Center, or did the Director of Central Intelligence fail the Counter-Terrorism Center by not bringing in more government-wide talent and skills?
Only after 9/11 did the various intelligence and law-enforcement entities begin to put aside their parochialism and work together in a more productive manner. With better leadership of the intelligence community, this condition would not have been prevalent before 9/11. It would not have taken that monumental disaster for our nation to get the members of the community to cooperate with one another.
One of the purposes of the Joint Inquiry, as stated in the preamble to the House and Senate committees' "Initial Scope" document, was to "lay the basis for assessing the accountability of institutions and officials of government." The JIS Report, however, apparently fails to identify which officials within the intelligence community had responsibility, before 9/11, for strategic and tactical warning of terrorist activity. Instead, Recommendation # 16 suggests that discovering who is accountable should be the job of the Inspectors General of the various agencies.
Inadequate Scope
The failures that led to 9/11 occurred not only in the intelligence community. The JIS was selective about what threads of inquiry it was willing to follow beyond the intelligence community. Failure to examine the State Department's visa-issuance process must rank as the most glaring of these omissions because the answer to the question -- could 9/11 have been prevented -- is yes, if State Department personnel had merely followed the law and not granted non-immigrant visas to 15 of the 19 hijackers in Saudi Arabia.
We repeat: If our own laws regarding the issuance of visas had been followed by the State Department, most of the hijackers would not have been able to obtain visas, and 9/11 would not have happened. Because the entire culture of the State Department is geared toward facilitating smooth relations with foreign governments, State Department personnel have tended to ignore the potential effect of their practices on national security.
An October, 2002 report of the General Accounting Office found that, before 9/11, there was among U .S. consular officers abroad a wide divergence of opinions and practices regarding
17
"the authority of consular officers to deny questionable applicants a visa; the role of the visa process in ensuring national security; and the types of changes . .. appropriate given the need for heightened border security." [28]
Section 214(b) of the Immigration and Nationality Act essentially creates a presumption against the issuance of visas to single young men without visible means of support. Consular officers are empowered with broad authority to deny visas in cases where the applicant fails to overcome this presumption. Section 214(b), which pertains to non-immigrant visas, specifically provides that applicants for such visas must demonstrate that they: 1) have a residence abroad and strong ties to a country that they have no intention of abandoning; 2) intend to leave the United States in a timely manner; and 3) intend to engage in legitimate activities related to the non-immigrant category.
_______________
28 "Border Security: Visa Process Should Be Strengthened as an Antiterrorism Tool," General Accounting Office, October, 2002, p. 3.
18
The failure of several of the terrorist hijackers, including the ringleader, Mohammed Atta, to completely fill out their applications provided ample reason for denying the visas. Only one of the 15 terrorists who were from Saudi Arabia provided an actual address; the rest listed only general locations, such as "California," "New York," "Hotel D.C." and "Hotel." [29] Only three of the 15 provided the name and street address of present employer or school as required on the application. Only one of these applications had additional documentation or explanatory notes provided by a consular officer that addressed any discrepancy or problem with the original application.
It was the official position of the State Department's Bureau of Consular Affairs for over a year, that 13 of the 15 terrorists from Saudi Arabia had been personally interviewed and that there was nothing in their visa applications or in the interviews that should have prevented issuance of their visas. According to the GAO, however, only two of the Saudi applicants were actually interviewed, and all 19 hijackers had substantial omissions and inconsistencies on their visa applications that should have raised concerns about why they wanted visas.
_______________
29 "Visas for Terrorists," Joel Mowbray, National Review, October 28, 2002.
19
The GAO reported that these applicants were presumed to be eligible based upon pre-9/11 internal State Department policies that stressed that all applicants from Saudi Arabia and the United Arab Emirates were to be considered "good cases" and, therefore, exempt from interviews. Moreover, the GAO noted that applicants from these two countries were not required to "complete their applications or [provide] supporting documentation." [30] Why was this so? The pervasiveness in Saudi Arabia of Wahhabism, a radical, anti-American variant of Islam, was well-known before 9/11. The JIS should have inquired why the country of Saudi Arabia was given such preferential treatment by the State Department and whether the intelligence agencies were complicit in the policy.
III. Comments on Recommendations
When there is a crisis, there is a tendency to look for easy solutions. A case in point is the first and most publicized Recommendation to come out of this investigation: the creation of a new "Director of National Intelligence." Good policies, good leadership, adequate resources, and will can better protect the American people from terrorism than simply creating new offices and rearranging organizational charts. And, as we have attempted to show, policy, resources, and leadership were issues that were not treated in sufficient depth by the JIS. It is not at all clear that a new intelligence "czar" could succeed where the Director of Central Intelligence has not. For that matter, the Report does not even conclude that DCI Tenet or any predecessor DCI did fail. The disconnect between the JIS' investigative efforts and the Recommendation supposedly based on them is remarkable.
On the merits of the "Director of National Intelligence" idea itself, we would concur with some of the points made by Vice Chairman Shelby in his Statement of Additional Views. Separating the job of the head of the intelligence community from the directorship of the CIA is an idea of some value. It has been endorsed by a number of post-Cold War studies of intelligence-community reform. However, we in the House and Senate intelligence committees have not yet deliberated enough on this question to draw any conclusions.
_______________
30 GAO report, p. 17.
20
As indicated above, we are particularly troubled by the JIS Report's Recommendation #16, calling for lower-level personnel to be held accountable by the various agencies' Inspectors General. It is doubtful whether this would improve the functioning of the intelligence agencies. Accountability of this kind would, in our view, have a troubling result: exacerbating what so many people quoted herein cited as a pervasive problem, namely, aversion to risk. Accountability of those at the very top is what is needed; it alone produces accountability at the intervening levels, and among officers in the field who run down the leads to find terrorists.
It would be expecting too much to think that U.S. authorities should have predicted that the attack of 9/11 would come. But the level of dysfunction in the security and intelligence agencies comes as a shock to Americans, who had faith in the expertise of the intelligence community. To restore that faith it must improve its performance, and in this regard, the proposition "First things first" is only common sense. Our duty to understand precedes our ability to improve. The JIS Report, in not fully coming to terms with what produced the intelligence failures it identified, left that duty unfulfilled. These Additional Views are offered not to criticize those who worked very hard under difficult circumstances to file a Report by the end of the 107th Congress, but to provide a more complete perspective for those who are charged to further investigate the terrorist attacks of September 11, 2001.
21
- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
Part 9 of 11
LAW ENFORCEMENT SENSITIVE. Additional Views of Senator Carl Levin
A fair reading of the facts contained in the Joint Inquiry report has led me to a deeply troubling conclusion:
Prior to September 11th, United States intelligence officials possessed terrorist information that if properly handled could have disrupted, limited, or possibly prevented the terrorist attacks against the World Trade Center Towers, the Pentagon, and United Airlines Flight 93. At crucial points in the twenty-one months leading up to September 11th, this intelligence information was either not shared or was not acted upon, and, as a result, opportunities to thwart the terrorist plot were squandered.
While the Joint Inquiry did not uncover a "smoking gun" leading up to September 11th, a number of "lit fuses" were known to counter-terrorism officials during a period of time when our Intelligence Community was at a heightened state of alert over imminent attacks from al-Qaeda. The report details how in the months leading up to September 11th these fuses were allowed to burn and how attempts to extinguish them were shockingly frustrated.
Two of the terrorists hijackers -- al-Mihdhar and al-Hazmi -- were allowed to enter the United States in January 2000 because the CIA, who knew the two to be linked with al-Qaeda and the 1998 East African embassy bombings, failed repeatedly to place them on a entry watchlist. One of the two -- al Mihdhar -- was able to leave and re-enter the United States in 2001 and, according to the FBI, may have spent his time abroad organizing the travel of the twelve terrorists who constituted the hijacking "muscle" into the United States.
On June 11, 2001, at a meeting of FBI and CIA officials, FBI field agents from New York investigating al-Qaeda's responsibility for the deadly U.S.S. Cole bombing, pressed for information regarding the CIA's interest in al-Mihdhar and al-Hazmi and their attendance at the January 2000 Malaysia meeting of al-Qaeda terrorists, which included the person responsible for planning the U.S.S. Cole attack. The CIA official at the meeting denied the FBI agent's request and withheld basic and relevant information about the suspected terrorists because he did not believe he had the authority to share the information.
Two and half months after this June 11, 2001, meeting, and after the two terrorists had been determined to have entered the country and were watchlisted, a FBI New York agent pressed FBI headquarters to use full criminal resources to find these at-large members of al- Qaeda. The agent's request was denied by the FBI's National Security Law Unit which cited a "wall" that prevented the sharing of intelligence information with criminal case agents. Invoking this so-called "wall" was erroneous however, and, as a result, the FBI's search for the terrorists in the two weeks leading up to the attacks was unnecessarily hamstrung.
(LES) The FBI's Minneapolis field office opened an international terrorism investigation of Zacarias Moussaoui and soon after arrested him on August 16, 2001. After the arrest, the CIA urgently solicited its stations around the world for additional information on Moussaoui, who it characterized as a "suspect airline suicide attacker" who might be "involved in a larger plot to target airlines traveling from Europe to the U.S." And yet, over the next three weeks FBI Minneapolis officials were frustrated in their efforts to obtain a FISA search warrant of Moussaoui's belongings by legal officials at FBI headquarters based on an incorrect reading of the search warrant requirements, a mistake now acknowledged by the FBI. After September 11th, Moussaoui's belongings revealed links to al-Qaeda officials which connected him to the planners of the terrorist plot.
Finally, while the Joint Inquiry report addresses at length the FBI's mishandling of the July 10, 2001, Phoenix Electronic Communication, it fails to note that many of the individuals identified by the FBI Phoenix agent as being part of a suspected al-Qaeda cell infiltrating the American civil aviation industry were the subject of "UBL-related investigations" by the FBI after the terrorist attacks. The warnings contained in the Phoenix Electronic Communication were largely ignored before September 11th. But surprisingly, despite all the subsequent attention given to the Phoenix document, the FBI Director, in the year after the terrorists attacks, was unable to inform the Senate Select Committee on Intelligence and the Joint Inquiry how many of the suspects identified by the Phoenix agent were linked to al-Qaeda and of the status of the investigation.
LAW ENFORCEMENT SENSITIVE. Additional Views of Senator Carl Levin
A fair reading of the facts contained in the Joint Inquiry report has led me to a deeply troubling conclusion:
Prior to September 11th, United States intelligence officials possessed terrorist information that if properly handled could have disrupted, limited, or possibly prevented the terrorist attacks against the World Trade Center Towers, the Pentagon, and United Airlines Flight 93. At crucial points in the twenty-one months leading up to September 11th, this intelligence information was either not shared or was not acted upon, and, as a result, opportunities to thwart the terrorist plot were squandered.
While the Joint Inquiry did not uncover a "smoking gun" leading up to September 11th, a number of "lit fuses" were known to counter-terrorism officials during a period of time when our Intelligence Community was at a heightened state of alert over imminent attacks from al-Qaeda. The report details how in the months leading up to September 11th these fuses were allowed to burn and how attempts to extinguish them were shockingly frustrated.
Two of the terrorists hijackers -- al-Mihdhar and al-Hazmi -- were allowed to enter the United States in January 2000 because the CIA, who knew the two to be linked with al-Qaeda and the 1998 East African embassy bombings, failed repeatedly to place them on a entry watchlist. One of the two -- al Mihdhar -- was able to leave and re-enter the United States in 2001 and, according to the FBI, may have spent his time abroad organizing the travel of the twelve terrorists who constituted the hijacking "muscle" into the United States.
On June 11, 2001, at a meeting of FBI and CIA officials, FBI field agents from New York investigating al-Qaeda's responsibility for the deadly U.S.S. Cole bombing, pressed for information regarding the CIA's interest in al-Mihdhar and al-Hazmi and their attendance at the January 2000 Malaysia meeting of al-Qaeda terrorists, which included the person responsible for planning the U.S.S. Cole attack. The CIA official at the meeting denied the FBI agent's request and withheld basic and relevant information about the suspected terrorists because he did not believe he had the authority to share the information.
Two and half months after this June 11, 2001, meeting, and after the two terrorists had been determined to have entered the country and were watchlisted, a FBI New York agent pressed FBI headquarters to use full criminal resources to find these at-large members of al- Qaeda. The agent's request was denied by the FBI's National Security Law Unit which cited a "wall" that prevented the sharing of intelligence information with criminal case agents. Invoking this so-called "wall" was erroneous however, and, as a result, the FBI's search for the terrorists in the two weeks leading up to the attacks was unnecessarily hamstrung.
(LES) The FBI's Minneapolis field office opened an international terrorism investigation of Zacarias Moussaoui and soon after arrested him on August 16, 2001. After the arrest, the CIA urgently solicited its stations around the world for additional information on Moussaoui, who it characterized as a "suspect airline suicide attacker" who might be "involved in a larger plot to target airlines traveling from Europe to the U.S." And yet, over the next three weeks FBI Minneapolis officials were frustrated in their efforts to obtain a FISA search warrant of Moussaoui's belongings by legal officials at FBI headquarters based on an incorrect reading of the search warrant requirements, a mistake now acknowledged by the FBI. After September 11th, Moussaoui's belongings revealed links to al-Qaeda officials which connected him to the planners of the terrorist plot.
Finally, while the Joint Inquiry report addresses at length the FBI's mishandling of the July 10, 2001, Phoenix Electronic Communication, it fails to note that many of the individuals identified by the FBI Phoenix agent as being part of a suspected al-Qaeda cell infiltrating the American civil aviation industry were the subject of "UBL-related investigations" by the FBI after the terrorist attacks. The warnings contained in the Phoenix Electronic Communication were largely ignored before September 11th. But surprisingly, despite all the subsequent attention given to the Phoenix document, the FBI Director, in the year after the terrorists attacks, was unable to inform the Senate Select Committee on Intelligence and the Joint Inquiry how many of the suspects identified by the Phoenix agent were linked to al-Qaeda and of the status of the investigation.
- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
Part 10 of 11
Senator Barbara A. Mikulski
As a member of the Senate Intelligence Committee, I voted in support of the recommendations of the Joint Intelligence Inquiry.
Protecting the American people is the most important responsibility I have as a United States Senator. We owe it to the victims of the September 11th and anthrax attacks, their families, and the nation to find answers. Who knew what and when before the September 11th attacks? And if they didn't know, why? The purpose of the joint inquiry was to ask the tough questions and use the answers to detect, deter and disrupt future attacks.
We must put in place an intelligence framework to meet the threats of the twenty-first century. We need a national debate and national consensus on the best way to prevent terrorism, protect the nation and preserve the Constitution and civil liberties.
A new framework demands reform. Our intelligence agencies must change. They must change their culture and how they operate. Congress and the Administration must make sure these agencies have the right resources to do their jobs. That means new technology, better training, and increased funding. The time for status quo is over. The threats to America are real and potentially devastating. We must be rigorous and unflinching in pursuit of reform.
While we protect America, we must also protect our Constitution and civil liberties.
There must be a vigorous national debate about the need for a domestic intelligence agency. The American people have a right to know, a right to be heard and a right to be included. The debate must be conducted in the sunshine. Congress should review any proposals through the committee process. Public comment should be encouraged through hearings, town halls meetings and other forums.
The American people must be informed and involved. Reform cannot be achieved in secret or by executive fiat. A decision on a new intelligence agency should be based on a national debate and national consensus, not partisan politics.
This debate must take place, and it must happen soon. I have no doubt that if America goes to war against Iraq, terrorists will go to war against America -- on American soil. America will be part of the battlefield. We must be prepared.
That is why I support the important concrete changes recommended by the Joint Inquiry Committee to revamp, reform and reinvigorate the Intelligence Community.
• Creating a Cabinet-level Director of National Intelligence position. This gives one person responsibility and authority over every element of the Intelligence Community -- to set priorities, assign personnel, and manage a unified budget. Breaking down silos and ending turf battles must be top priority. Putting a single person in charge is a solid first step to real reform.
• Creation of a national watchlist center. Four of the terrorists involved in the September 11th attacks were stopped by local law enforcement for speeding or for not having a driver's license. When the police officers did the checks, there were no flashing yellow lights about these men. Today local law enforcement knows more about dead- beat dads than death threat terrorists. Something is really wrong here. We need to fix it. Creating a national watchlist center will ensure that information about potential terrorists is available to those who need it -- ftom Customs inspectors to local cops on the beat. Creating better technologies for intelligence. Our intelligence community must stay ahead of the curve on developing and using new technologies. We need to make sure our ears on the world don't go deaf because of commercial encryption or huge volumes of data.
• Reforming the FBI. The FBI must be more effective and efficient in both law enforcement and preventing terrorism. That means better analysis and training, modernizing computer systems to share information, and cooperation with other intelligence agencies.
Senator Barbara A. Mikulski
As a member of the Senate Intelligence Committee, I voted in support of the recommendations of the Joint Intelligence Inquiry.
Protecting the American people is the most important responsibility I have as a United States Senator. We owe it to the victims of the September 11th and anthrax attacks, their families, and the nation to find answers. Who knew what and when before the September 11th attacks? And if they didn't know, why? The purpose of the joint inquiry was to ask the tough questions and use the answers to detect, deter and disrupt future attacks.
We must put in place an intelligence framework to meet the threats of the twenty-first century. We need a national debate and national consensus on the best way to prevent terrorism, protect the nation and preserve the Constitution and civil liberties.
A new framework demands reform. Our intelligence agencies must change. They must change their culture and how they operate. Congress and the Administration must make sure these agencies have the right resources to do their jobs. That means new technology, better training, and increased funding. The time for status quo is over. The threats to America are real and potentially devastating. We must be rigorous and unflinching in pursuit of reform.
While we protect America, we must also protect our Constitution and civil liberties.
There must be a vigorous national debate about the need for a domestic intelligence agency. The American people have a right to know, a right to be heard and a right to be included. The debate must be conducted in the sunshine. Congress should review any proposals through the committee process. Public comment should be encouraged through hearings, town halls meetings and other forums.
The American people must be informed and involved. Reform cannot be achieved in secret or by executive fiat. A decision on a new intelligence agency should be based on a national debate and national consensus, not partisan politics.
This debate must take place, and it must happen soon. I have no doubt that if America goes to war against Iraq, terrorists will go to war against America -- on American soil. America will be part of the battlefield. We must be prepared.
That is why I support the important concrete changes recommended by the Joint Inquiry Committee to revamp, reform and reinvigorate the Intelligence Community.
• Creating a Cabinet-level Director of National Intelligence position. This gives one person responsibility and authority over every element of the Intelligence Community -- to set priorities, assign personnel, and manage a unified budget. Breaking down silos and ending turf battles must be top priority. Putting a single person in charge is a solid first step to real reform.
• Creation of a national watchlist center. Four of the terrorists involved in the September 11th attacks were stopped by local law enforcement for speeding or for not having a driver's license. When the police officers did the checks, there were no flashing yellow lights about these men. Today local law enforcement knows more about dead- beat dads than death threat terrorists. Something is really wrong here. We need to fix it. Creating a national watchlist center will ensure that information about potential terrorists is available to those who need it -- ftom Customs inspectors to local cops on the beat. Creating better technologies for intelligence. Our intelligence community must stay ahead of the curve on developing and using new technologies. We need to make sure our ears on the world don't go deaf because of commercial encryption or huge volumes of data.
• Reforming the FBI. The FBI must be more effective and efficient in both law enforcement and preventing terrorism. That means better analysis and training, modernizing computer systems to share information, and cooperation with other intelligence agencies.
- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
Part 11 of 11
ADDITIONAL VIEWS. Congressman Tim Roemer
I want to begin by congratulating the leadership of the Joint Inquiry for their bipartisanship, productivity, and helpful recommendations. In the history of Congress, very few joint inquiries have been created, let alone been successful. Congress, as an institution, can look at this bicameral and bipartisan accomplishment with pride.
Although I generally embrace the findings and recommendations of the report, there are several areas where further emphasis is needed and additional improvements must be made.
One of my great frustrations during my service on the Permanent Select Committee on Intelligence has been the degree to which access to information is restricted, either from the committee or within the committee, often for reasons that have little or no correlation to national security. Many times, these restrictions have the effect of impairing the ability of members of the committee to make fully informed decisions on important budgetary or policy matters. For example, during the Joint Inquiry, it became clear that individual government officials had been briefed about certain terrorist related information before September 11. The substance of these briefings was declassified and made public. The dates that these briefings took place were declassified. Thus, sensitive information that might reveal sources, methods, or expose national security concerns, is not part of the equation here. But the identity of the participants in the briefings, even by reference to the title of the offices they held, was not declassified. In other words, a judgment was made that national security would not be endangered if the American people knew the specifics about information their government possessed about terrorism, but would be threatened if they knew who in their government knew that information. There are few things more destructive, in my judgment, to the bond of trust between the people and their government than refusing to declassify information which might be politically uncomfortable or embarrassing. Classification should be for important national security reasons, and references to title and positions should not be classified or asserted as covered under the doctrine of executive privilege.
12-17-02, 11:45am
The executive branch suffers from a tendency toward over classification which, especially in the area of intelligence, diminishes Congress' ability to effectively oversee budget and policy decisions. I hope that the procedures through which information is classified will be streamlined. Additionally, we must accelerate the pace of review for declassification of information already classified. As part of these efforts, I strongly encourage the administration to reconsider its decision to maintain the classification of titles and positions in the matter of concern to the Joint Inquiry.
The Joint Inquiry focused almost totally, given the jurisdiction of the two committees, on the September 11-related activities of the intelligence agencies. Although these agencies have significant responsibilities on security issues, and terrorism issues specifically, those responsibilities are not exclusive in either area. To understand fully how the September 11 attacks were successfully conducted requires a look well beyond the borders of the intelligence community. Issues like the Federal Aviation Administration (FAA) and airline security; the manner in which visa applications are reviewed; the procedures used to grant entry into the United States at points of entry, as well as those used to monitor our borders; and issues related to the security of our ports, particularly our ability to track the movement of cargo, all need to be scrutinized. A more thorough and comprehensive look at the September 11 attacks, and ways to prevent attacks in the future, needs to be done. I am hopeful that the recently established national commission will complete that job.
The Joint Inquiry would have benefited greatly, in my judgment, had it been able to hear directly from the most senior national security officials in the current administration. For various reasons, the Secretaries of State and Defense, the Attorney General, and the National Security Advisor were not questioned directly about issues related to the September 11 attacks. I do not believe that the record of the national commission will be complete unless this shortcoming is addressed.
I agree with those who urge a more exhaustive investigation of the means through which the September 11 hijackers were supported financially while they were planning and training for the attacks. Money combines with ideology to form the lifeblood of terrorism. Shutting off the
2
12-17-02.11'45 am
flow of funds, whatever their source, is critical to winning the war against terrorism. Of particular concern is whether other nations, either wittingly or as a result of less than aggressive efforts to monitor financial transactions within their own borders, may have provided support to the September 11 hijackers, or may be providing support to other terrorists who would do harm to the United States. I believe it is imperative that every effort be made to fully investigate all financial relationships between terrorist groups and members of the international community. Our Joint Inquiry has scratched the surface of this critical issue; other investigations, including the national commission, must complete this effort.
We also recommended that a Cabinet-level Director of National Intelligence (DNI) be appointed to lead the intelligence community. This grows out of our concern that the current structure is not conducive to the management of the intelligence community as a coherent whole. The intelligence community encompasses more than a dozen agencies and tens of thousands of employees. These entities are diverse in their focus and composition. We found that there were serious difficulties in setting budget and policy priorities across the intelligence community and ensuring their implementation. Thus, the intelligence community is ill equipped to meet the new challenge of global terrorists focused on targets within the United States.
Leadership of the intelligence community should be strengthened through the creation of a new position with sufficient authority, resources, and staff to manage intelligence agencies as a cohesive entity. We believe this Director of National Intelligence should be sufficiently empowered that he or she can exercise the full range of management, budgetary and personnel responsibilities. Making this position a reality, however, will raise a host of practical issues that will require careful consideration by the Congress, not least of which is the question of what authority over the intelligence agencies should remain with the heads of the departments in which these entities reside.
The Joint Inquiry recommends that the new Director of National Intelligence not be permitted to serve as the head of the Central Intelligence Agency (CIA) or any other individual intelligence agency. The intent of this provision is to ensure that leadership of the intelligence community remains focused and consistent across all agencies of the community. However, an
3
12-17-02, 11:45am
argument can be made that a DNI would be more effective if he or she also served as the head of an agency. I would strongly recommend that the Congress and commission study this issue more carefully, and I will remain open to the debate.
The Joint Inquiry recommendations recognized that the workforce of the intelligence community is its greatest resource. All Americans should be thankful for the thousands of individuals employed by U.S. intelligence agencies who make countless sacrifices for our collective security. Yet we have found that these individuals are not as well equipped and well trained as they should be. The Joint Inquiry makes numerous recommendations on measures that should be implemented to enhance the development of the workforce with the skills and expertise, and intelligence tools, needed for success in counterterrorist efforts. First among these is better expertise, especially in languages. Language readiness is woefully inadequate across the intelligence community, and the Congress has repeatedly stressed the need for a strategic plan to remedy the problem with multi- faceted, sustained and creative approaches.
On another personnel matter, the importance of strategic analysis cannot be overstated. This topic is well developed in sections of the report, but I wish to further emphasize that already existing information technology can assist in the development of better analytic products, if fully utilized. The collection agencies disseminate intelligence reports to large numbers of users through cables, whose formats were defined many years ago. These cables tend to provide very little context, so if the recipient is not familiar with the details of the particular topic the importance of the intelligence could be likely missed. This could have contributed to the failure of the CIA to watchlist Nawaf al- Hazmi and Khaled al-Mihdhar. Intelligence reporting formats should be modernized and analytic tools more widely utilized to facilitate the discovery of links between new and previously acquired information. These efforts can contribute to a greater depth and quality of analysis.
Finally, the importance of all collected information is not always well understood by the reports officers who act as collection filters when they create the cables that are disseminated to the all- source analysts. The Joint Inquiry uncovered instances where information was not disseminated, because intelligence thresholds were not met, that in hindsight, would have
4
12-17-02, 11:45am
revealed important information about some of the September 11th hijackers. The Joint Inquiry recommendations and the conference report on the Intelligence Authorization Act for Fiscal Year 2003 both address this issue concerning access to "raw" intelligence. Since seemingly insignificant information given to the right analyst, or appropriately data-mined and correlated by an analytic tool, could help uncover the next plot, such information must be made available to a limited number of analysts for domestic security and force protection purposes.
5
12-17-02, 11:45 am
ADDITIONAL VIEWS. Congressman Tim Roemer
I want to begin by congratulating the leadership of the Joint Inquiry for their bipartisanship, productivity, and helpful recommendations. In the history of Congress, very few joint inquiries have been created, let alone been successful. Congress, as an institution, can look at this bicameral and bipartisan accomplishment with pride.
Although I generally embrace the findings and recommendations of the report, there are several areas where further emphasis is needed and additional improvements must be made.
One of my great frustrations during my service on the Permanent Select Committee on Intelligence has been the degree to which access to information is restricted, either from the committee or within the committee, often for reasons that have little or no correlation to national security. Many times, these restrictions have the effect of impairing the ability of members of the committee to make fully informed decisions on important budgetary or policy matters. For example, during the Joint Inquiry, it became clear that individual government officials had been briefed about certain terrorist related information before September 11. The substance of these briefings was declassified and made public. The dates that these briefings took place were declassified. Thus, sensitive information that might reveal sources, methods, or expose national security concerns, is not part of the equation here. But the identity of the participants in the briefings, even by reference to the title of the offices they held, was not declassified. In other words, a judgment was made that national security would not be endangered if the American people knew the specifics about information their government possessed about terrorism, but would be threatened if they knew who in their government knew that information. There are few things more destructive, in my judgment, to the bond of trust between the people and their government than refusing to declassify information which might be politically uncomfortable or embarrassing. Classification should be for important national security reasons, and references to title and positions should not be classified or asserted as covered under the doctrine of executive privilege.
12-17-02, 11:45am
The executive branch suffers from a tendency toward over classification which, especially in the area of intelligence, diminishes Congress' ability to effectively oversee budget and policy decisions. I hope that the procedures through which information is classified will be streamlined. Additionally, we must accelerate the pace of review for declassification of information already classified. As part of these efforts, I strongly encourage the administration to reconsider its decision to maintain the classification of titles and positions in the matter of concern to the Joint Inquiry.
The Joint Inquiry focused almost totally, given the jurisdiction of the two committees, on the September 11-related activities of the intelligence agencies. Although these agencies have significant responsibilities on security issues, and terrorism issues specifically, those responsibilities are not exclusive in either area. To understand fully how the September 11 attacks were successfully conducted requires a look well beyond the borders of the intelligence community. Issues like the Federal Aviation Administration (FAA) and airline security; the manner in which visa applications are reviewed; the procedures used to grant entry into the United States at points of entry, as well as those used to monitor our borders; and issues related to the security of our ports, particularly our ability to track the movement of cargo, all need to be scrutinized. A more thorough and comprehensive look at the September 11 attacks, and ways to prevent attacks in the future, needs to be done. I am hopeful that the recently established national commission will complete that job.
The Joint Inquiry would have benefited greatly, in my judgment, had it been able to hear directly from the most senior national security officials in the current administration. For various reasons, the Secretaries of State and Defense, the Attorney General, and the National Security Advisor were not questioned directly about issues related to the September 11 attacks. I do not believe that the record of the national commission will be complete unless this shortcoming is addressed.
I agree with those who urge a more exhaustive investigation of the means through which the September 11 hijackers were supported financially while they were planning and training for the attacks. Money combines with ideology to form the lifeblood of terrorism. Shutting off the
2
12-17-02.11'45 am
flow of funds, whatever their source, is critical to winning the war against terrorism. Of particular concern is whether other nations, either wittingly or as a result of less than aggressive efforts to monitor financial transactions within their own borders, may have provided support to the September 11 hijackers, or may be providing support to other terrorists who would do harm to the United States. I believe it is imperative that every effort be made to fully investigate all financial relationships between terrorist groups and members of the international community. Our Joint Inquiry has scratched the surface of this critical issue; other investigations, including the national commission, must complete this effort.
We also recommended that a Cabinet-level Director of National Intelligence (DNI) be appointed to lead the intelligence community. This grows out of our concern that the current structure is not conducive to the management of the intelligence community as a coherent whole. The intelligence community encompasses more than a dozen agencies and tens of thousands of employees. These entities are diverse in their focus and composition. We found that there were serious difficulties in setting budget and policy priorities across the intelligence community and ensuring their implementation. Thus, the intelligence community is ill equipped to meet the new challenge of global terrorists focused on targets within the United States.
Leadership of the intelligence community should be strengthened through the creation of a new position with sufficient authority, resources, and staff to manage intelligence agencies as a cohesive entity. We believe this Director of National Intelligence should be sufficiently empowered that he or she can exercise the full range of management, budgetary and personnel responsibilities. Making this position a reality, however, will raise a host of practical issues that will require careful consideration by the Congress, not least of which is the question of what authority over the intelligence agencies should remain with the heads of the departments in which these entities reside.
The Joint Inquiry recommends that the new Director of National Intelligence not be permitted to serve as the head of the Central Intelligence Agency (CIA) or any other individual intelligence agency. The intent of this provision is to ensure that leadership of the intelligence community remains focused and consistent across all agencies of the community. However, an
3
12-17-02, 11:45am
argument can be made that a DNI would be more effective if he or she also served as the head of an agency. I would strongly recommend that the Congress and commission study this issue more carefully, and I will remain open to the debate.
The Joint Inquiry recommendations recognized that the workforce of the intelligence community is its greatest resource. All Americans should be thankful for the thousands of individuals employed by U.S. intelligence agencies who make countless sacrifices for our collective security. Yet we have found that these individuals are not as well equipped and well trained as they should be. The Joint Inquiry makes numerous recommendations on measures that should be implemented to enhance the development of the workforce with the skills and expertise, and intelligence tools, needed for success in counterterrorist efforts. First among these is better expertise, especially in languages. Language readiness is woefully inadequate across the intelligence community, and the Congress has repeatedly stressed the need for a strategic plan to remedy the problem with multi- faceted, sustained and creative approaches.
On another personnel matter, the importance of strategic analysis cannot be overstated. This topic is well developed in sections of the report, but I wish to further emphasize that already existing information technology can assist in the development of better analytic products, if fully utilized. The collection agencies disseminate intelligence reports to large numbers of users through cables, whose formats were defined many years ago. These cables tend to provide very little context, so if the recipient is not familiar with the details of the particular topic the importance of the intelligence could be likely missed. This could have contributed to the failure of the CIA to watchlist Nawaf al- Hazmi and Khaled al-Mihdhar. Intelligence reporting formats should be modernized and analytic tools more widely utilized to facilitate the discovery of links between new and previously acquired information. These efforts can contribute to a greater depth and quality of analysis.
Finally, the importance of all collected information is not always well understood by the reports officers who act as collection filters when they create the cables that are disseminated to the all- source analysts. The Joint Inquiry uncovered instances where information was not disseminated, because intelligence thresholds were not met, that in hindsight, would have
4
12-17-02, 11:45am
revealed important information about some of the September 11th hijackers. The Joint Inquiry recommendations and the conference report on the Intelligence Authorization Act for Fiscal Year 2003 both address this issue concerning access to "raw" intelligence. Since seemingly insignificant information given to the right analyst, or appropriately data-mined and correlated by an analytic tool, could help uncover the next plot, such information must be made available to a limited number of analysts for domestic security and force protection purposes.
5
12-17-02, 11:45 am
- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
APPENDICES
APPENDIX
THE SENATE SELECT COMMITTEE ON INTELLIGENCE AND HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE INITIAL SCOPE OF JOINT INQUIRY
(148 Cong. Rec. H3493 (daily ed. Jun 5,2002))
Congress of the United States
Washington, D.C. 20515
PREAMBLE
To reduce the risk or future terrorist attacks; to honor the memories of the victims of the September 11 terrorist attacks by conducting a thorough search for facts to answer the many questions that their families and many Americans have raised; and to lay a basis for assessing the accountability of institutions and officials of government:
THE SENATE SELECT COMMITTEE ON INTELLIGENCE AND HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE ADOPT THIS INITIAL SCOPE OF JOINT INQUIRY
Pursuant to section 5(a)(l) of Senate Resolution 400, 94thCongress, Rule 6 of the Rules of Procedure of the Senate Select Committee on Intelligence, Rule X1(1)(b) of the Rules of the House of Representatives, and Rule 9 of the Rules of Procedure of the House Permanent Select Committee on Intelligence, the two Committees have authorized an investigation, to be conducted as a Joint Inquiry, into the Intelligence Community's activities before and after the September 11, 2001 terrorist attacks on the United States. The Committees have undertaken this Joint Inquiry pursuant to their responsibility to oversee and make continuing studies of the intelligence activities and programs of the United States Government and all other authority vested in the Committees.
The purpose of this Joint Inquiry is --
(a) to conduct an investigation into. and study of: all matters that may have any tendency to reveal the full facts about --
(1) the evolution of the international terrorist threat to the United States, the response of the United States Government including that of the Intelligence Community to international terrorism, from the creation of the Director of Central Intelligence's Counterterrorist Center in 1986 to the present. and what the Intelligence Community had, has, or should have learned from all sources of information, including any terrorist attacks or attempted ones, about the international terrorist threat to the United States;
(2) what the Intelligence Community knew prior to September 11 about the scope and nature of any possible attacks against the United States or United States interests by international terrorists, including by any of the hijackers or their associates, and what was done with that information;
(3) what the Intelligence Community has learned since the events of September 11 about the persons associated with those events, and whether any of that information suggests actions that could or should have been taken to learn of, or prevent, those events;
(4) whether any information developed before or after September 11 indicates systemic problems that may have impeded the Intelligence Community from learning of or preventing the attacks in advance. or that, if remedied. could help the Community identify and prevent such attacks in the future;
(5) how and to what degree the elements of the Intelligence Community have interacted with each other, as well as other parts of federal, state, and local governments with respect to identifying, tracking. assessing. and coping with international terrorist threats; as well as biological, chemical, radiological, or nuclear threats, whatever their source (such as the Anthrax attack of 2001).
(6) the ways in which the Intelligence Community's responses to past intelligence problems and challenges, whether or not related to international terrorism, have affected its counterterrorism efforts; and
(7) any other information that would enable the Joint Inquiry, and the Committees in the performance of their continuing responsibilities, to make such recommendations, including recommendations for new or amended legislation and any administrative or structural changes, or other actions. as they determine to be necessary or desirable to improve the ability of the Intelligence Community to learn of, and prevent, future international terrorist attacks; and
(b) to fulfill the Constitutional oversight and informing functions of the Congress with regard to the matters examined in the Joint Inquiry.
APPENDIX
THE SENATE SELECT COMMITTEE ON INTELLIGENCE AND HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE
SUPPLEMENTAL JOINT INQUIRY RULES
148 Cong. Rec. S5032 (daily ed. Jun 5, 2002)
148 Cong. Rec. H3493 (daily ed. Jun 12, 2002)
HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE
SUPPLEMENTAL JOINT INQUIRY RULES
In connection with the Joint Inquiry with the Senate Select Committee on Intelligence into the events of September 11, 2001, authorized by the House Permanent Select Committee on Intelligence ("HPSCI"') pursuant to Rule XI(1)(b) of the Rules of the House of Representatives and Rule 9 of HPSCI's Rules of Procedure, and pursuant to Rule XI(2)(a) of the Rules of the House of Representatives, HPSCI adopts the following Joint Inquiry Rules to supplement HPSCI's Rules for purposes of the Joint Inquiry only:
JOINT INQUIRY RULE 1. JOINT PROCEEDINS
1.1. HPSCI may conduct hearings jointly with the Senate Select Committee on Intelligence. All joint hearings shall be considered hearings of both Committees.
1.2. The Rules of Procedure of HPSCI and the Senate Select Committee on Intelligence shall apply in all hearings and other proceedings of this Joint Inquiry, except where superseded by these Joint Inquiry Rules, provided that, at any joint hearing, if any rules of the two Committees are inconsistent, the rules of that Committee whose Chairman or his designee is presiding shall apply.
1-3. For the purposes of the proceedings of this Joint Inquiry, all employees on :the staff of either Committee working on the Joint Inquiry shall be considered to be acting on behalf of both Committees.
JOINT INQUIRY RULE 2. HEARINGS
2.1, All testimony at hearings shall be taken under oath or affirmation.
JOINT INQUIRY RULE 3. DEPOSITIONS
3.l. All testimony taken, and all documents, records, or other materials produced, at a deposition of the Senate Select Committee on Intelligence shall be considered part of the record of both Committees.
SENATE SELECT COMMITTEE ON INTELLIGENCE
SUPPLEMENTAL JOINT INQUIRY RULES
In connection with the Joint Inquiry with the House Permanent Select Committee on Intelligence into the events of September 11, 2001, authorized by the Senate Select Committee on Intelligence ("SSCI") pursuant to section 5(a)(1) of Senate Resolution 400, 94th Congress, and Rule 6 of the SSCI's Rules of Procedure, and pursuant to Rule XXVI.2 of the Standing Rules of the Senate, the SSCI adopts the following Joint Inquiry Rules to supplement the SSCI's Rules of Procedure for purposes of the Joint Inquiry only:
JOINT INQUIRY RULE 1. JOINT PROCEEDINGS
1.1. The SSCI may conduct hearings jointly with the House Permanent Select Committee on Intelligence. All joint hearings shall be considered hearings of both Committees.
1.2. The Rules of Procedure of both the SSCI and the House Permanent Select Committee on Intelligence shall apply in all hearings and other proceedings of this Joint Inquiry, except where superseded by these Joint Inquiry Rules, provided that, at any joint hearing, if any rules of the two Committees .are inconsistent, the rules of that Committee whose Chairman or his designee is presiding shall apply.
1.3. For the purposes of the proceedings of this Joint Inquiry, all employees on the staff of either Committee working on the Joint Inquiry shall be considered to be acting on behalf of both Committees.
JOINT INQUIRY RULE 2. HEARINGS
2.1. All testimony at hearings shall be taken under oath or affirmation.
2.2. Subpoenas for the attendance of witnesses, or the production of documents, records, or other materials, at hearings may be authorized by vote of the SSCI pursuant to SSCI Rule 2, or by the SSCI's Chairman and Vice Chairman, acting jointly.
JOINT INQUIRY RULE 3. DEPOSITIONS
3.1. All testimony taken, and all documents, records, or other materials produced, at a deposition of the SSCI shall be considered part of the record of both Committees.
3.2. Subpoenas for depositions and notices for the taking of depositions may be authorized by vote of the SSCI pursuant to SSCI Rule 2, or by the SSCI's Chairman and Vice Chairman, acting jointly, and shall be issued and served as provided in SSCI Rule 7. Deposition notices shall specify a time and place of examination and the name or names of Committee members or staff who will take the deposition. Depositions shall be in private and shall, for purposes of the rules of both Committees, be deemed to be testimony given before the Committees in executive session.
3.3. Witnesses shall be examined upon oath administered by a member of the SSCI or by an individual authorized by local law to administer oaths. Questions may be propounded by members or staff of either Committee. If a witness objects to a question and refuses to testify, the Committee members or staff present may proceed with the deposition, or may, at that time or subsequently, seek a ruling on the objection from the Chairman of the SSCI or any member of the SSCI designated by the Chairman. The SSCI shall not initiate procedures leading to civil or criminal enforcement unless the witness refuses to testify after having been ordered and directed to answer by the Chairman or a member designated by the Chairman.
3.4. Procedures for the attendance of counsel for witnesses at, and for the inspection, correction, and filing of transcripts of, depositions shall be as provided in SSCI Rules 8.4 and 8.7.
APPENDIX
JOINT INQUIRY HEARINGS
APPENDIX
LIST OF HEARING WITNESSES
List of Hearing Witnesses
The following is a list of witnesses who appeared before Joint Inquiry hearings conducted by the House Permanent Select Committee on Intelligence and the Senate Select Committee on Intelligence in open or closed session. Affiliations listed are as of the date of appearance.
APPENDIX
INTERVIEWS CONDUCTED IN THE COURSE OF THE JOINT INQUIRY
INTERVIEWS CONDUCTED IN THE COURSE OF THE JOINT INQUIRY *
[ ], Assistant Legal Attache, Paris, Federal Bureau of Investigation
[ ], Program Manager, Counterterrorist Center, Central Intelligence Agency
[ ], Inspection Division, Federal Bureau of Investigation
[ ], Assistant General Counsel, Federal Bureau of Investigation
[ ], Directorate of Science and Technology, Central Intelligence Agency
Maj. Gen. Keith Alexander, Intelligence and Security Command, Land Information Warfare Agency
[ ], Counterterrorist Center, Central Intelligence Agency
Charles E. Allen, Associate Director of Central Intelligence for Collection
[ ], Special Agent, Newark Field Office, Federal Bureau of lnvestiigation
[ ], Special Agent, Washington Field Office, Federal Bureau of Investigation
[ ], Associate Director for Intelligence, Joint Chiefs of Staff
[ ], New York Field Office, Federal Bureau of Investigation
[ ], New York Field Office, Federal Bureau of Investigation
[ ], Headquarters', Defense Intelligence Agency
________________
* Note: This is only a partial list of persons from whom the Joint Inquiry acquired information. It includes persons who were present for group discussions, as well as those who were interviewed individually. Foreign government officials are not included. Interviewee affiliations are as of the date of interview. Names have been redacted for both national security and privacy reasons.
John Arriza, Director, TIPOFF Watchlist Program, Department of State
[ ], National Security Agency Representative to Counterterrorist Center
Maureen Baginski, Director, Signals Intelligence Directorate, National Security Agency
James Baker, Counsel for Intelligence Policy, Department of Justice
[ ], New York Field Office, Federal Bureau of Investigation
[ ], Assistant Legal Attache, Singapore, Federal Bureau of Investigation
[ ], New York Field Office, Federal Bureau of Investigation
[ ], Defense Attache, US. Army, Tel Aviv, Israel
[ ], Counterterrorist Center, Central Intelligence Agency
Samuel "Sandy" Berger, Former Assistant to the President for National Security Affairs
Richard Betts, Professor, Columbia University
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, Oklahoma City Field Office, Federal Bureau of Investigation
Joe Billy, Special Agent In-Charge, New York Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
Cofer Black, Former Chief, Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
William Black, Deputy Director, National Security Agency
[ ], Defense Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Foreign Broadcast Information Service, Central Intelligence Agency
[ ], Section Chief; Counterintelligence Division, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Office of General Counsel, Counterterrorist Center, Central Intelligence Agency
Marion E. (Spike) Bowman, Deputy General Counsel for National Security Affairs, Federal Bureau of Investigation
[ ], Former NSA Detailee to Counterterrorist Center, Central Intelligence Agency
[ ], Directorate of Operations, Central Intelligence Agency
[ ], Chief of Language School, Central Intelligence Agency
John Brennan, Executive Director, Central Intelligence Agency
[ ] , [ }, [ }, Central Intelligence Agency
[ ], Private Citizen
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], Radical Fundamentalist Unit, Federal Bureau of Investigation
Robert Bryant, Former Deputy Director, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
Jeffrey Builta, Defense Intelligence Agency
[ ], [ }, [ }, Central Intelligence Agency
[ ], Joint Counterintelligence Assessment Group, Department of Defense
[ ], Former Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Counterterrorism Office, National Security Unit, Immigration and Naturalization Service
[ ], Senior Science Advisor, Joint Chiefs of Staff
[ ], Headquarters, Defense Intelligence Agency
[ ], Central Intelligence Agency
Lt. Gen. Michael Canavan, U.S. Army (Ret), Former Commander, Joint Special Operation/)' Command
[ ], Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
Amb. Timothy Carney, Former US Ambassador to Sudan
[ ], Former Chief; CIA Counterterrorist Center, Central Intelligence Agency
[ ], Supervisory Special Agent, FBI Representative to Department of State
[ ], Counterterrorism Center, Central Intelligence Agency
James T. Caruso, FBI Deputy Executive Assistant Director for Counterintelligence and Counterterrorism
[ ], Counterterrorism Center, Central Intelligence Agency
Ed Chase, Office of Management and Budget
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency Representative to Deputy Director of Central Intelligence
Richard Clarke, Former National Coordinator for Counterterrorism, Clinton and Bush Administrations
[ ], Boston Field Office, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], Counterterrorism Center, Central Intelligence Agency (Retired)
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Headquarters, Federal Bureau of Investigation
[ ], Civil Aviation Security Field Office, Minneapolis Airport, Department of Transportation
Jay Corcoran, Director of Intelligence, U.S. Customs Service
[ ], Information Operation Specialist, Federal Bureau of Investigation
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], [ i, [ i, Central Intelligence Agency
[ ], National Security Agency
Roger Cressey, National Security Counsel
William P. Crowell, Former Deputy Director, National Security Agency
[ ] , Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Counterterrorism Center, Central Intelligence Agency
Pasquale D' Amuro, Assistant Director, Counterterrorist Division, Federal Bureau of Investigation
Maj. Gen. Keith Dayton, Director of Operations, Defense Intelligence Agency
[ ], National Security Agency
[ ], Special Agent, Phoenix Field Office, Federal Bureau C!,( Investigation
John Deutch, Former Director of Central Intelligence
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ], Assistant Legal Attache, Islamabad, Federal Bureau of Investigation
[ ], Division Chief Central Intelligence Agency
[ ], Inspection Division, Federal Bureau of Investigation
Patrick Duecy, Director, Joint Intelligence Task Force, Defense Intelligence Agency
[ ] , Director, Executive Secretary, Central Intelligence Agency
[ ], Legal Attache, London, England, Federal Bureau of Investigation
[ ], Special Agent, Boston Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Department of State Representative to Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Headquarters, Federal Bureau of Investigation
[ ],Radical Fundamentalist Unit, Federal Bureau of Investigation
[ ], [ ], [ ], [ }, [ ],
Central Intelligence Agency
[ ], U.S, Customs Service
[ ], Legal Attache, Brussels and The Hague, Federal Bureau of Investigation
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Radical Fundamentalist Unit, Federal Bureau of Investigation
[ ], Office of General Counsel, Counterterrorist Center, Central intelligence Agency
Louis J. Freeh, Former Director, Federal Bureau of Investigation
Vice Adm. Scott Fry , Commander, 6th Fleet, Former Deputy Director of Operations, Joint Chiefs of Staff
[ ], Former Federal Bureau of Investigation Special Agent
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Portland Field Office, Federal Bureau of Investigation
[ ], Federal Bureau of Investigation
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Federal Bureau of Investigation Representative to Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Acting Legal Attache, Tel Aviv, Israel, Federal Bureau of Investigation
[ ] , Special Agent, Federal Bureau of Investigation
[ ], Language Specialist, Federal Bureau of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Federal Bureau of Investigation
[ ], Private Citizen
[ ], Legal Attache, Berlin, Federal Bureau of Investigation
[ ], Central Intelligence Agency
[ ], Special Agent, Federal Bureau of Investigation
[ ], [ ], Central Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
William Gore, Special Agent In-Charge, San Diego Field Office, Federal Bureau of Investigation
Brig. Gen. Scott Gration, Former Deputy Director Information Operations, Joint Chiefi' of Staff
[ ], Counterterrorist Referent, [ ], Central Intelligence Agency
[ ], [ ], Central Intelligence Agency
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Chief Language Services Division, Federal Bureau of Investigation
[ ], Former [ ] Division Chief of Operations, [ ],
Central Intelligence Agency
[ ], National Security Agency
Carol Haave, Deputy Assistant Secretary of Defense for Security and Information Operations
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], National Imagery and Mapping Agency
Lee Hamilton, Former House Permanent Select Committee on Intelligence Chairman,
Director, Woodrow Wilson International Center for Scholars,
Director, Center on Congress at Indiana University
[ ], Supervisory Special Agent, Federal Bureau of Investigation
John Hamre, Former Deputy Secretary of Defense, Former Comptroller, Department of Defense
[ ], Associate Deputy Director of Central Intelligence for Operations for Resources,
Plans and Policy
[ ] , Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Former Supervisory Special Agent, Phoenix Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], National Imagery and Mapping Agency
[ ], Headquarters, Federal Bureau of Investigation
[ ], Immigration and Naturalization Service
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation Retiree
Richard Haver, Special Assistant for Intelligence, Office of the Secretary of Defense
Lt. Gen Michael Hayden, Director, National Security Agency
Christine Healey, Minority Counsel, House Permanent Select Committee on Intelligence
[ ], Booz Allen & Hamilton
[ ], General Accounting Office
Frederick Hitz, Former Inspector General, Central Intelligence Agency
[ ], National Security Agency
[ ], [ ], Division Chief Central Intelligence Agency
[ ], Acting Legal Attache, London, England, Federal Bureau of Investigation
[ ], Private Citizen
Karl Inderfurth, Former Assistant Secretary of State for South Asia
[ ], National Security Agency
Rear Adm. Lowell E. Jacoby, Director, Defense Intelligence Agency, Joint Chiefs of Staff
[ ] , Central Intelligence Agency
[ ] , Special Agent, Federal Bureau of Investigation
Robert Jervis, Professor, Columbia University
[ ], [ ], [ ], Central Intelligence Agency
[ ] , Special Agent, Boston Field Office, Federal Bureau of Investigation
[ ], Defense Intelligence Agency
[ ], Special Agent, Minneapolis Field Office, Federal Bureau of Investigation
[ ], National Security Agency Representative to Federal Bureau of Investigation
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency
Donald Kerr, Deputy Director of Central Intelligence for Science and Technology
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Defense Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], National Security Agency Representative to Federal Bureau of Investigation
[ ], Directorate for Science and Technology, Central Intelligence Agency
[ ], Former Counterterrorist Center, Central Intelligence Agency
David Kris, Associate Deputy Attorney General, Department of Justice
Capt. Michael Kuhn, US. Navy
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Phoenix Field Office, Federal Bureau of Investigation
Thomas Kuster, Director of Counterterrorism Policy, Department of Defense
[ ] , Assistant Special Agent In-Charge, San Diego Field Office,
Federal Bureau of Investigation
[ ], Supervisory Special Agent, Boston Field Office, Federal Bureau of Investigation
[ ], Language Specialist, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Headquarters, Federal Bureau of Investigation
Matthew Levitt, Washington Institute for Near East Policy
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Headquarters, Federal Bureau of Investigation
[ ] , Deputy Assistant Director, Inspection Division, Federal Bureau of Investigation
[ ], National Security Agency
[ ], National Security Agency
John Louder, National Reconnaissance Agency
Mark Lowenthal, Associate Director of Central Intelligence for Analysis and Production
[ ], Department of State
[ ], Headquarters, Federal Bureau of Investigation
[ ], Federal Bureau of Investigation
[ ], Supervisory Special Agent, Cleveland Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ] , Central Intelligence Agency
Claudio Manno, Federal Aviation Administration, Transportation Security Administration
[ ], Headquarters, Federal Bureau of Investigation
[ ], Headquarters, Federal Bureau of Investigation
[ ] , National Security Agency
[ ], Department of State
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], U.S. Navy
[ ], Assistant Special Agent In-Charge, New York Field Office, Federal Bureau of Investigation
Mary McCarthy, Former Senior Director for Intelligence Programs, National Security Council
Steven McCraw, Special Agent In-Charge, San Antonio Field Office, Federal Bureau of Investigation
[ ], Immigration and Naturalization Service Representative to Federal Bureau
of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
Barbara McN amara, Former Deputy Director, National Security Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Federal Bureau of Investigation
Mark Miller, Central Intelligence Agency Representative to Federal Bureau of Investigation
[ ] , Chief Information Officer, Central Intelligence Agency
[ ], Immigration and Naturalization Service
[], National Security Agency
Lt. Gen. Kenneth Minihan, Former Director, National Security Agency
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ] , Special Agent, Dallas Field Office, Federal Bureau of Investigation
[ ], Special Agent, Dallas Field Office, Federal Bureau of Investigation
[ ], Office of Homeland Security
[ ], National Security Agency
[ ], Defense Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ] , Division Chief National Security Agency
[ ], [ ], [ ], Central Intelligence Agency
[ ], Former Analyst, Federal Bureau of Investigation
[ ], Analyst, Central Intelligence Agency
Lt. Gen. Gregory Newbold, Former Director of Operations, Joint Chiefs of Staff
[ ], Central Intelligence Agency
Glenn Nordin, Assistant Director of Intelligence Policy (Language), Department of Defense
[ ], Immigration and Naturalization Service
[ ], Defense Intelligence Agency
[ ], Headquarters, Federal Bureau of Investigation
[ ], Former Chief Counterterrorist Center, Central Intelligence Agency
[ ], Central Intelligence Agency Analyst, [ ]
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Analyst, Central Intelligence Agency
[ ] , Customs Representative to CIA Counterterrorist Center
[ ], Headquarters, Federal Bureau of Investigation
James Pavit, Deputy Director of Central Intelligence for Operations
[ ], Defense Intelligence Agency
[ ], Central Intelligence Agency Representative to FBI New York Field Office
[ ], Supervisory Special Agent, Dallas Field Office, Federal Bureau of Investigation
[ ], [ ], [ J] Central Intelligence Agency
Thomas Pickard, Former Deputy Director, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ], Assistant Special Agent In-Charge, Sacramento Field Office, Federal Bureau of Investigation
Paul Pillar, National Intelligence Officer for Near East, South Africa, Central Intelligence Agency
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation
John Pistole, Deputy Assistant Director, Counterterrorism Division, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Assistant General Counsel, Federal Bureau of Investigation
[ ], Unit Chief Federal Bureau of Investigation
[ ], Deputy Director, Office of Budget, Central Intelligence Agency
[ ], Office of General Counsel, National Security Agency
[ ], Assistant Special Agent In-Charge, Boston Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Analyst, Counterterrorist Center, Central Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
COL Richard G. Reynolds, Defense Attache, Amman, Jordan
Keith Rhodes, Chief Technologist, Center for Technology and Engineering, General Accounting Office
Susan Rice, Former Senior Director for African Affairs, National Security Council
[ ], Analyst, [ ], Central Intelligence Agency
[ ], Central Intelligence Agency
[ ], U. S. Customs Service
[ ], Language School, Central Intelligence Agency
[ ], Federal Aviation Administration
Michael Rolince, Headquarters, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Federal Bureau of Investigation Special Agent attached to Joint Terrorist Task Force
[ ], Special Agent, Minneapolis Field Office, Federal Bureau of Investigation
Colleen Rowley, Principal Legal Advisor, Minneapolis Field Office, Federal Bureau of Investigation
Mary Ryan, Assistant Secretary of State for Consular Affairs
[ ], Office of General Counsel, Federal Bureau of Investigation
[ ], Federal Aviation Administration Representative to Federal Bureau of Investigation
[ ], Special Agent, Minneapolis Field Office, Federal Bureau of Investigation
Jerry Savage, Office of Inspector General, Department of Defense
[ ], Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Central Intelligence Agency, [ ]
[ ], Central Intelligence Agency
[ ], Central Intelligence Agency
John Schuhart, Director, Resource Management Office, Community Management Staff
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], National Security Agency Representative to Deputy Director of Central Intelligence
[ ], [ ], [ ], Central Intelligence Agency
[ ], Oklahoma City Field Office, Federal Bureau of Investigation
[ ], Directorate of Science and Technology, Central Intelligence Agency
[ ], National Security Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], National Security Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
Michael Sheehan, Ambassador to the UN; former Coordinator for Counterterrorism, Department of State
Michael Sheehy, Minority Staff Director, House Permanent Select Committee on Intelligence
Gen. Hugh Shelton, Former Chairman, Joint Chiefs of Staff
[ ], Director, Office of the Budget, Central Intelligence Agency
[ ], Defense Intelligence Agency
[ ], Central Intelligence Agency, [ ], [ ]
[ ], Deputy Counsel for Operations, Department of Justice
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
James Sloan, Director, Financial Crimes Enforcement Network, Department of Treasury
[ ], National Security Agency
[ ], Immigration and Naturalization Representative to CIA Counterterrorist Center
[ ] , Special Agent, Kansas City Field Office, Federal Bureau of Investigation
[ ], Department of State
[ ], Special Agent, New York City Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Headquarters Analyst, Federal Bureau of Investigation
[ ], Counterterrorist Center Analyst, Central Intelligence Agency
[ ], National Security Agency
Roy Surrett, Director of Intelligence, U.S. Customs Service
[ ], Supervisory Special Agent San Diego Field Office, Federal Bureau of Investigation
[ ], Language Specialist, Federal Bureau of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
Francis X. Taylor, Ambassador at Large for Coordination and Implementation of Government-wide
US. Counterterrorism Policy, Department of State
Richard Taylor, Former Deputy Director of Operations, National Security' Agency
[ ] , Joint Intelligence Task Force-Counterterrorism, Defense Intelligence Agency
[ ], Headquarters Analyst, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Inspection Division, Federal Bureau of Investigation
[ ], Supervisory Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
Frances Fragos Townsend, Former Counsel for Intelligence Policy, Department of Justice
[ ], Central Intelligence Agency
[ ], Directorate of Operations Senior Official, Central Intelligence Agency
[ ], Boston Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Headquarters Analyst, Federal Bureau of Investigation
[ ], Analyst, National Security Agency
[ ] , Chicago Field Office, Federal Bureau of Investigation (Retired)
[ ], [ ], [ ], [ ], Central Intelligence Agency
[ ], Defense Intelligence Agency
[ ], Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Chief of Operations, [ ] Central Intelligence Agency
Maj. Gen. Ward, U.S. Army, Vice Director of Operations, Joint Chiefs of Staff
[ ], Defense Intelligence Agency, Department of Defense
[ ], Directorate for Science and Technology, Central Intelligence Agency
Dale Watson, Executive Assistant Director for Counterterrorism and Counterintelligence,
Federal Bureau of Investigation
William Webster, Former Director of Central Intelligence, Former Director, Federal Bureau of Investigation
[ ], [ ], [ ], [ ], National Security Agency
[ ], Financial Review Group, Federal Bureau of Investigation
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center Analyst, Central Intelligence Agei1cy
Linton Wells, Principal Deputy Assistant Secretary of Defense (Command, Control, Communications
and Intelligence), Department of Defense
[ ], Central Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
Mary Jo White, Former U.S. Attorney for the Southern District of New York
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Former Special Agent, Milwaukee Field Office, Federal Bureau of Investigation
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation
[ ] , Central Intelligence Agency
[ ], Central Intelligence Agency Representative to Federal Bureau of Investigation
[ ], [ ], [ ], [ ], National Security Agency
Vice Adm. Thomas Wilson (Ret), Former Director, Defense Intelligence Agency
[ ] , Boston Field Office, Federal Bureau of Investigation
[ ], National Security Law Unit, Federal Bureau of Investigation
[ ], Finance Division, Federal Bureau of Investigation
James Woolsey, Former Director of Central Intelligence
[ ], Former Special Agent, Chicago Field Office, Federal Bureau of Investigation
Austin Yamada, Deputy Assistant Secretary of Defense for Special Operations, Department of Defense
[ ], Special Agent, Oklahoma City Field Office, Federal Bureau of Investigation
Wayne Zaidemann, Legal Attache, Amman, Jordan, Federal Bureau of Investigation
APPENDIX
THE SENATE SELECT COMMITTEE ON INTELLIGENCE AND HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE INITIAL SCOPE OF JOINT INQUIRY
(148 Cong. Rec. H3493 (daily ed. Jun 5,2002))
Congress of the United States
Washington, D.C. 20515
PREAMBLE
To reduce the risk or future terrorist attacks; to honor the memories of the victims of the September 11 terrorist attacks by conducting a thorough search for facts to answer the many questions that their families and many Americans have raised; and to lay a basis for assessing the accountability of institutions and officials of government:
THE SENATE SELECT COMMITTEE ON INTELLIGENCE AND HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE ADOPT THIS INITIAL SCOPE OF JOINT INQUIRY
Pursuant to section 5(a)(l) of Senate Resolution 400, 94thCongress, Rule 6 of the Rules of Procedure of the Senate Select Committee on Intelligence, Rule X1(1)(b) of the Rules of the House of Representatives, and Rule 9 of the Rules of Procedure of the House Permanent Select Committee on Intelligence, the two Committees have authorized an investigation, to be conducted as a Joint Inquiry, into the Intelligence Community's activities before and after the September 11, 2001 terrorist attacks on the United States. The Committees have undertaken this Joint Inquiry pursuant to their responsibility to oversee and make continuing studies of the intelligence activities and programs of the United States Government and all other authority vested in the Committees.
The purpose of this Joint Inquiry is --
(a) to conduct an investigation into. and study of: all matters that may have any tendency to reveal the full facts about --
(1) the evolution of the international terrorist threat to the United States, the response of the United States Government including that of the Intelligence Community to international terrorism, from the creation of the Director of Central Intelligence's Counterterrorist Center in 1986 to the present. and what the Intelligence Community had, has, or should have learned from all sources of information, including any terrorist attacks or attempted ones, about the international terrorist threat to the United States;
(2) what the Intelligence Community knew prior to September 11 about the scope and nature of any possible attacks against the United States or United States interests by international terrorists, including by any of the hijackers or their associates, and what was done with that information;
(3) what the Intelligence Community has learned since the events of September 11 about the persons associated with those events, and whether any of that information suggests actions that could or should have been taken to learn of, or prevent, those events;
(4) whether any information developed before or after September 11 indicates systemic problems that may have impeded the Intelligence Community from learning of or preventing the attacks in advance. or that, if remedied. could help the Community identify and prevent such attacks in the future;
(5) how and to what degree the elements of the Intelligence Community have interacted with each other, as well as other parts of federal, state, and local governments with respect to identifying, tracking. assessing. and coping with international terrorist threats; as well as biological, chemical, radiological, or nuclear threats, whatever their source (such as the Anthrax attack of 2001).
(6) the ways in which the Intelligence Community's responses to past intelligence problems and challenges, whether or not related to international terrorism, have affected its counterterrorism efforts; and
(7) any other information that would enable the Joint Inquiry, and the Committees in the performance of their continuing responsibilities, to make such recommendations, including recommendations for new or amended legislation and any administrative or structural changes, or other actions. as they determine to be necessary or desirable to improve the ability of the Intelligence Community to learn of, and prevent, future international terrorist attacks; and
(b) to fulfill the Constitutional oversight and informing functions of the Congress with regard to the matters examined in the Joint Inquiry.
APPENDIX
THE SENATE SELECT COMMITTEE ON INTELLIGENCE AND HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE
SUPPLEMENTAL JOINT INQUIRY RULES
148 Cong. Rec. S5032 (daily ed. Jun 5, 2002)
148 Cong. Rec. H3493 (daily ed. Jun 12, 2002)
HOUSE PERMANENT SELECT COMMITTEE ON INTELLIGENCE
SUPPLEMENTAL JOINT INQUIRY RULES
In connection with the Joint Inquiry with the Senate Select Committee on Intelligence into the events of September 11, 2001, authorized by the House Permanent Select Committee on Intelligence ("HPSCI"') pursuant to Rule XI(1)(b) of the Rules of the House of Representatives and Rule 9 of HPSCI's Rules of Procedure, and pursuant to Rule XI(2)(a) of the Rules of the House of Representatives, HPSCI adopts the following Joint Inquiry Rules to supplement HPSCI's Rules for purposes of the Joint Inquiry only:
JOINT INQUIRY RULE 1. JOINT PROCEEDINS
1.1. HPSCI may conduct hearings jointly with the Senate Select Committee on Intelligence. All joint hearings shall be considered hearings of both Committees.
1.2. The Rules of Procedure of HPSCI and the Senate Select Committee on Intelligence shall apply in all hearings and other proceedings of this Joint Inquiry, except where superseded by these Joint Inquiry Rules, provided that, at any joint hearing, if any rules of the two Committees are inconsistent, the rules of that Committee whose Chairman or his designee is presiding shall apply.
1-3. For the purposes of the proceedings of this Joint Inquiry, all employees on :the staff of either Committee working on the Joint Inquiry shall be considered to be acting on behalf of both Committees.
JOINT INQUIRY RULE 2. HEARINGS
2.1, All testimony at hearings shall be taken under oath or affirmation.
JOINT INQUIRY RULE 3. DEPOSITIONS
3.l. All testimony taken, and all documents, records, or other materials produced, at a deposition of the Senate Select Committee on Intelligence shall be considered part of the record of both Committees.
SENATE SELECT COMMITTEE ON INTELLIGENCE
SUPPLEMENTAL JOINT INQUIRY RULES
In connection with the Joint Inquiry with the House Permanent Select Committee on Intelligence into the events of September 11, 2001, authorized by the Senate Select Committee on Intelligence ("SSCI") pursuant to section 5(a)(1) of Senate Resolution 400, 94th Congress, and Rule 6 of the SSCI's Rules of Procedure, and pursuant to Rule XXVI.2 of the Standing Rules of the Senate, the SSCI adopts the following Joint Inquiry Rules to supplement the SSCI's Rules of Procedure for purposes of the Joint Inquiry only:
JOINT INQUIRY RULE 1. JOINT PROCEEDINGS
1.1. The SSCI may conduct hearings jointly with the House Permanent Select Committee on Intelligence. All joint hearings shall be considered hearings of both Committees.
1.2. The Rules of Procedure of both the SSCI and the House Permanent Select Committee on Intelligence shall apply in all hearings and other proceedings of this Joint Inquiry, except where superseded by these Joint Inquiry Rules, provided that, at any joint hearing, if any rules of the two Committees .are inconsistent, the rules of that Committee whose Chairman or his designee is presiding shall apply.
1.3. For the purposes of the proceedings of this Joint Inquiry, all employees on the staff of either Committee working on the Joint Inquiry shall be considered to be acting on behalf of both Committees.
JOINT INQUIRY RULE 2. HEARINGS
2.1. All testimony at hearings shall be taken under oath or affirmation.
2.2. Subpoenas for the attendance of witnesses, or the production of documents, records, or other materials, at hearings may be authorized by vote of the SSCI pursuant to SSCI Rule 2, or by the SSCI's Chairman and Vice Chairman, acting jointly.
JOINT INQUIRY RULE 3. DEPOSITIONS
3.1. All testimony taken, and all documents, records, or other materials produced, at a deposition of the SSCI shall be considered part of the record of both Committees.
3.2. Subpoenas for depositions and notices for the taking of depositions may be authorized by vote of the SSCI pursuant to SSCI Rule 2, or by the SSCI's Chairman and Vice Chairman, acting jointly, and shall be issued and served as provided in SSCI Rule 7. Deposition notices shall specify a time and place of examination and the name or names of Committee members or staff who will take the deposition. Depositions shall be in private and shall, for purposes of the rules of both Committees, be deemed to be testimony given before the Committees in executive session.
3.3. Witnesses shall be examined upon oath administered by a member of the SSCI or by an individual authorized by local law to administer oaths. Questions may be propounded by members or staff of either Committee. If a witness objects to a question and refuses to testify, the Committee members or staff present may proceed with the deposition, or may, at that time or subsequently, seek a ruling on the objection from the Chairman of the SSCI or any member of the SSCI designated by the Chairman. The SSCI shall not initiate procedures leading to civil or criminal enforcement unless the witness refuses to testify after having been ordered and directed to answer by the Chairman or a member designated by the Chairman.
3.4. Procedures for the attendance of counsel for witnesses at, and for the inspection, correction, and filing of transcripts of, depositions shall be as provided in SSCI Rules 8.4 and 8.7.
APPENDIX
JOINT INQUIRY HEARINGS
JOINT INQUIRY HEARINGS
Date / Subject/Substance / Status
Jun 4, 2002 / Business Meeting / Closed
Jun 5 / Evolution Of The Threat / Closed
Jun 6 / Evolution of The Threat / Closed
Jun 11 / Richard Clarke, Former National Coordinator for Security, Infrastructure, and Counterterrorism / Closed
Jun 12 / The Intelligence Community Before September 11 Airplanes As Weapons / Closed
Jun 18 Lt. General Michael Hayden Director, National Security Agency / Closed
-- / Robert Mueller Director of the Federal Bureau of Investigation / Closed
-- / George Tenet Director of Central Intelligence / Closed
Jun 19 / Lt. General Michael Hayden Director, National Security Agency / Closed
-- / George Tenet Director of Central Intelligence / Closed
-- / Robert Mueller Director of the Federal Bureau of Investigation / Closed
Jul 16 / Technical Collection / Closed
Jul 18 / Technical Collection / Closed
Jul 23 / Financial Campaign / Closed
Jul 25 / Analysis & Language / Closed
Sep 12 / Covert Action / Closed
Sep 18 / Representatives Of September 11 Victims' Families / Open
Sep 19 / Richard Armitage Deputy Secretary Of State / Open
-- / Samuel Berger Former National Security Advisor To The President / Open
-- / Brent Scowcroft Former National Security Advisor To The President / Open
-- / Paul Wolfowitz Deputy Secretary Of Defense / Open
Sep 20 / The Hijackers / Open
Sep 24 / Moussaoui & The Phoenix Electronic Communication / Open
Sep 26 / Moussaoui & The Phoenix Electronic Communication / Closed
Sep 26 / Response To The Terrorist Threat / Open
Oct 1 / Information Sharing / -- Open
Oct 3 / Proposed Reorganization Of The Intelligence Community / Open
Oct 8 / Lessons Learned / Open
Oct 9 / FBI/CIA Issues / Open
Oct 10 / FBI/CIA Issues / Closed
-- / Robert Mueller Director of the Federal Bureau of Investigation / Closed
-- / George Tenet Director of Central Intelligence / Closed
Oct 17 / Lt. General Michael Hayden Director, National Security Agency / Open
-- / Robert Mueller Director of the Federal Bureau of Investigation / Open
-- / George Tenet Director of Central Intelligence / Open
Dec 10 / Business Meeting / Closed
APPENDIX
LIST OF HEARING WITNESSES
List of Hearing Witnesses
The following is a list of witnesses who appeared before Joint Inquiry hearings conducted by the House Permanent Select Committee on Intelligence and the Senate Select Committee on Intelligence in open or closed session. Affiliations listed are as of the date of appearance.
June 4, 2002 / Business Meeting (No Witnesses)
June 5, 2002 / Alonzo Robertson, Joint Inquiry Staff
-- / John Keefe, Joint Inquiry Staff
June 6, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / Alonzo Robertson, Joint Inquiry Staff
-- / John Keefe, Joint Inquiry Staff
June 11, 2002 / Richard Clarke, Special Advisor to the President for Cyberspace Security, Executive Office of the President, former Coordinator for Security, Infrastructure, and Counterterrorism, National Security Council, 1993 - 2001.
June 12, 2002 / Miles Kara, Joint Inquiry Staff
-- / Patti Litman, Joint Inquiry Staff
-- / Michael Jacobson, Joint Inquiry Staff
June 18, 2002 / George Tenet, Director of Central Intelligence
-- / Robert Mueller, Director, Federal Bureau of Investigation
-- / Lieutenant General Michael Hayden, USAF, Director, National Security Agency
June 19, 2002 / George Tenet, Director of Central Intelligence
-- / Robert Mueller, Director, Federal Bureau of Investigation
-- / Lieutenant General Michael Hayden, USAF, Director, National Security Agency
July 16, 2002 / Robert Rosenwald, Joint Inquiry Staff
-- / Patti Litman, Joint Inquiry Staff
July 18, 2002 / Lieutenant General Michael Hayden, USAF, Director, National Security Agency
-- / Dr. Donald Kerr, Deputy Director of Central Intelligence for Science and Technology
-- / James Caruso, Deputy Assistant Director for Counterterrorism and Counterintelligence, Federal Bureau of Investigation
July 23, 2002 / David Aufltauser, General Counsel, Department of Treasury
-- / James Sloan, Director, Financial Crimes Enforcement Network
-- / Richard Newcomb, Office of Foreign Assets Control
-- / Dennis Lormel, Section Chief, Financial Review Group, Federal Bureau of Investigation
July 25, 2002 / Central Intelligence Agency Officer
-- / Defense Intelligence Agency Officer
-- / National Security Agency Officer
-- / Federal Bureau of Investigation Supervisor
-- / Central Intelligence Agency Officer
Sept. 12, 2002 / Counterterrorist Center Officers, Central Intelligence Agency
-- / Cofer Black, Former Chief, Counterterrorist Center, Central Intelligence Agency
Sept. 18, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / Kristin Breitweiser, Co-Founder of September 11th Advocates
-- / Stephen Push, Co-Founder and Treasurer of Families of September 11th
Sept. 19, 2002 / Richard Armitage, Deputy Secretary of State
-- / Paul Wolfowitz, Deputy Secretary of Defense
-- / General Brent Scowcroft, USAF (Ret.) National Security Advisor, Ford Administration and George H. W. Bush Administration
-- / Samuel Berger, National Security Advisor, Clinton Administration, Second Term
Sept. 20, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / CIA Officer
-- / FBI Special Agent
-- / Michael Rolince, Special Agent-in-Charge, Washington Field Office, Federal Bureau of Investigation
-- / Christopher Kojm, Deputy for Intelligence Policy and Coordination, Bureau of intelligence and Research, Department of State
Sept. 24, 2002 Eleanor Hill, Director, Joint Inquiry Staff
-- / FBI Special Agent, Minneapolis Field Office
-- / FBI Special Agent, Phoenix Field Office
-- / FBI Supervisor, FBI Headquarters
Sept. 26, 2002 / Cofer Black, Former Chief, Counterterrorist Center, Central Intelligence Agency
-- / Dale Watson, Former Executive Director, Counterintelligence and Counterterrorism Division, Federal Bureau of Investigation
-- / FBI Special Agent, Minneapolis Field Office
-- / FBI Special Agent, Phoenix Field Office
-- / FBI Supervisor, FBI Headquarters
-- / Michael Rolince, Special Agent-in-Charge, Washington Field Office, Federal Bureau of Investigation
-- / M. E. Bowman, Deputy General Counsel, Federal Bureau of Investigation
Oct 1, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / James S. Gilmore, III, Former Governor of the Commonwealth of Virginia and Chairman, Advisory Panel to Assess Capabilities for Domestic Response to Terrorism
-- / Amb. Francis X. Taylor, Counterterrorism Coordinator, Department of State
-- / Claudio Manno, Acting Associate Under Secretary for Intelligence, Transportation Security Agency
-- / Joseph B. Greene, Assistant Commissioner for Investigations, U.S. Immigration and Naturalization Service
-- / Louis E. Andre, Special Assistant to the Director for Intelligence, J-2, Defense Intelligence Agency
-- / Edward T. Norris, Police Commissioner, City of Baltimore, MD
Oct 3, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / Lee Hamilton, Former Chairman, House Permanent Select Committee on Intelligence, Director, Woodrow Wilson International Center for Scholars
-- / Judge William Webster, Former Director of Central Intelligence and Former Director, Federal Bureau of Investigation
-- / Lieutenant General William Odom, USA (Ret.), Former Director, National Security Agency
-- / Frederick Hitz, Former Inspector General, Central Intelligence Agency
Oct 8, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / Warren Rudman, Former U.S. Senator
-- / Judge Louis Freeh, Former Director, Federal Bureau of Investigation
-- / Mary Jo White, Former U.S. Attorney, Southern District of New York
-- / Paul Pillar, National Intelligence Officer for Near East/South Africa, Central Intelligence Agency
Oct 9, 2002 / Pasquale D' Amuro, FBI Executive Assistant Director
-- / CIA Official
-- / FBI Special Agent
Oct 10, 2002 / George Tenet, Director of Central Intelligence
-- / Robert Mueller, Director, Federal Bureau of Investigation
Oct 17, 2002 / Eleanor Hill, Director, Joint Inquiry Staff
-- / George Tenet, Director of Central Intelligence
-- / Robert Mueller, Director, Federal Bureau of Investigation
-- / Lieutenant General Michael Hayden, USAF, Director, National Security Agency
APPENDIX
INTERVIEWS CONDUCTED IN THE COURSE OF THE JOINT INQUIRY
INTERVIEWS CONDUCTED IN THE COURSE OF THE JOINT INQUIRY *
[ ], Assistant Legal Attache, Paris, Federal Bureau of Investigation
[ ], Program Manager, Counterterrorist Center, Central Intelligence Agency
[ ], Inspection Division, Federal Bureau of Investigation
[ ], Assistant General Counsel, Federal Bureau of Investigation
[ ], Directorate of Science and Technology, Central Intelligence Agency
Maj. Gen. Keith Alexander, Intelligence and Security Command, Land Information Warfare Agency
[ ], Counterterrorist Center, Central Intelligence Agency
Charles E. Allen, Associate Director of Central Intelligence for Collection
[ ], Special Agent, Newark Field Office, Federal Bureau of lnvestiigation
[ ], Special Agent, Washington Field Office, Federal Bureau of Investigation
[ ], Associate Director for Intelligence, Joint Chiefs of Staff
[ ], New York Field Office, Federal Bureau of Investigation
[ ], New York Field Office, Federal Bureau of Investigation
[ ], Headquarters', Defense Intelligence Agency
________________
* Note: This is only a partial list of persons from whom the Joint Inquiry acquired information. It includes persons who were present for group discussions, as well as those who were interviewed individually. Foreign government officials are not included. Interviewee affiliations are as of the date of interview. Names have been redacted for both national security and privacy reasons.
John Arriza, Director, TIPOFF Watchlist Program, Department of State
[ ], National Security Agency Representative to Counterterrorist Center
Maureen Baginski, Director, Signals Intelligence Directorate, National Security Agency
James Baker, Counsel for Intelligence Policy, Department of Justice
[ ], New York Field Office, Federal Bureau of Investigation
[ ], Assistant Legal Attache, Singapore, Federal Bureau of Investigation
[ ], New York Field Office, Federal Bureau of Investigation
[ ], Defense Attache, US. Army, Tel Aviv, Israel
[ ], Counterterrorist Center, Central Intelligence Agency
Samuel "Sandy" Berger, Former Assistant to the President for National Security Affairs
Richard Betts, Professor, Columbia University
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, Oklahoma City Field Office, Federal Bureau of Investigation
Joe Billy, Special Agent In-Charge, New York Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
Cofer Black, Former Chief, Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
William Black, Deputy Director, National Security Agency
[ ], Defense Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Foreign Broadcast Information Service, Central Intelligence Agency
[ ], Section Chief; Counterintelligence Division, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Office of General Counsel, Counterterrorist Center, Central Intelligence Agency
Marion E. (Spike) Bowman, Deputy General Counsel for National Security Affairs, Federal Bureau of Investigation
[ ], Former NSA Detailee to Counterterrorist Center, Central Intelligence Agency
[ ], Directorate of Operations, Central Intelligence Agency
[ ], Chief of Language School, Central Intelligence Agency
John Brennan, Executive Director, Central Intelligence Agency
[ ] , [ }, [ }, Central Intelligence Agency
[ ], Private Citizen
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], Radical Fundamentalist Unit, Federal Bureau of Investigation
Robert Bryant, Former Deputy Director, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
Jeffrey Builta, Defense Intelligence Agency
[ ], [ }, [ }, Central Intelligence Agency
[ ], Joint Counterintelligence Assessment Group, Department of Defense
[ ], Former Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Counterterrorism Office, National Security Unit, Immigration and Naturalization Service
[ ], Senior Science Advisor, Joint Chiefs of Staff
[ ], Headquarters, Defense Intelligence Agency
[ ], Central Intelligence Agency
Lt. Gen. Michael Canavan, U.S. Army (Ret), Former Commander, Joint Special Operation/)' Command
[ ], Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
Amb. Timothy Carney, Former US Ambassador to Sudan
[ ], Former Chief; CIA Counterterrorist Center, Central Intelligence Agency
[ ], Supervisory Special Agent, FBI Representative to Department of State
[ ], Counterterrorism Center, Central Intelligence Agency
James T. Caruso, FBI Deputy Executive Assistant Director for Counterintelligence and Counterterrorism
[ ], Counterterrorism Center, Central Intelligence Agency
Ed Chase, Office of Management and Budget
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency Representative to Deputy Director of Central Intelligence
Richard Clarke, Former National Coordinator for Counterterrorism, Clinton and Bush Administrations
[ ], Boston Field Office, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], Counterterrorism Center, Central Intelligence Agency (Retired)
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Headquarters, Federal Bureau of Investigation
[ ], Civil Aviation Security Field Office, Minneapolis Airport, Department of Transportation
Jay Corcoran, Director of Intelligence, U.S. Customs Service
[ ], Information Operation Specialist, Federal Bureau of Investigation
[ ], Counterterrorism Center, Central Intelligence Agency
[ ], [ i, [ i, Central Intelligence Agency
[ ], National Security Agency
Roger Cressey, National Security Counsel
William P. Crowell, Former Deputy Director, National Security Agency
[ ] , Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Counterterrorism Center, Central Intelligence Agency
Pasquale D' Amuro, Assistant Director, Counterterrorist Division, Federal Bureau of Investigation
Maj. Gen. Keith Dayton, Director of Operations, Defense Intelligence Agency
[ ], National Security Agency
[ ], Special Agent, Phoenix Field Office, Federal Bureau C!,( Investigation
John Deutch, Former Director of Central Intelligence
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ], Assistant Legal Attache, Islamabad, Federal Bureau of Investigation
[ ], Division Chief Central Intelligence Agency
[ ], Inspection Division, Federal Bureau of Investigation
Patrick Duecy, Director, Joint Intelligence Task Force, Defense Intelligence Agency
[ ] , Director, Executive Secretary, Central Intelligence Agency
[ ], Legal Attache, London, England, Federal Bureau of Investigation
[ ], Special Agent, Boston Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Department of State Representative to Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Headquarters, Federal Bureau of Investigation
[ ],Radical Fundamentalist Unit, Federal Bureau of Investigation
[ ], [ ], [ ], [ }, [ ],
Central Intelligence Agency
[ ], U.S, Customs Service
[ ], Legal Attache, Brussels and The Hague, Federal Bureau of Investigation
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Radical Fundamentalist Unit, Federal Bureau of Investigation
[ ], Office of General Counsel, Counterterrorist Center, Central intelligence Agency
Louis J. Freeh, Former Director, Federal Bureau of Investigation
Vice Adm. Scott Fry , Commander, 6th Fleet, Former Deputy Director of Operations, Joint Chiefs of Staff
[ ], Former Federal Bureau of Investigation Special Agent
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Portland Field Office, Federal Bureau of Investigation
[ ], Federal Bureau of Investigation
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Federal Bureau of Investigation Representative to Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Acting Legal Attache, Tel Aviv, Israel, Federal Bureau of Investigation
[ ] , Special Agent, Federal Bureau of Investigation
[ ], Language Specialist, Federal Bureau of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Federal Bureau of Investigation
[ ], Private Citizen
[ ], Legal Attache, Berlin, Federal Bureau of Investigation
[ ], Central Intelligence Agency
[ ], Special Agent, Federal Bureau of Investigation
[ ], [ ], Central Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
William Gore, Special Agent In-Charge, San Diego Field Office, Federal Bureau of Investigation
Brig. Gen. Scott Gration, Former Deputy Director Information Operations, Joint Chiefi' of Staff
[ ], Counterterrorist Referent, [ ], Central Intelligence Agency
[ ], [ ], Central Intelligence Agency
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Chief Language Services Division, Federal Bureau of Investigation
[ ], Former [ ] Division Chief of Operations, [ ],
Central Intelligence Agency
[ ], National Security Agency
Carol Haave, Deputy Assistant Secretary of Defense for Security and Information Operations
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], National Imagery and Mapping Agency
Lee Hamilton, Former House Permanent Select Committee on Intelligence Chairman,
Director, Woodrow Wilson International Center for Scholars,
Director, Center on Congress at Indiana University
[ ], Supervisory Special Agent, Federal Bureau of Investigation
John Hamre, Former Deputy Secretary of Defense, Former Comptroller, Department of Defense
[ ], Associate Deputy Director of Central Intelligence for Operations for Resources,
Plans and Policy
[ ] , Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Former Supervisory Special Agent, Phoenix Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], National Imagery and Mapping Agency
[ ], Headquarters, Federal Bureau of Investigation
[ ], Immigration and Naturalization Service
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation Retiree
Richard Haver, Special Assistant for Intelligence, Office of the Secretary of Defense
Lt. Gen Michael Hayden, Director, National Security Agency
Christine Healey, Minority Counsel, House Permanent Select Committee on Intelligence
[ ], Booz Allen & Hamilton
[ ], General Accounting Office
Frederick Hitz, Former Inspector General, Central Intelligence Agency
[ ], National Security Agency
[ ], [ ], Division Chief Central Intelligence Agency
[ ], Acting Legal Attache, London, England, Federal Bureau of Investigation
[ ], Private Citizen
Karl Inderfurth, Former Assistant Secretary of State for South Asia
[ ], National Security Agency
Rear Adm. Lowell E. Jacoby, Director, Defense Intelligence Agency, Joint Chiefs of Staff
[ ] , Central Intelligence Agency
[ ] , Special Agent, Federal Bureau of Investigation
Robert Jervis, Professor, Columbia University
[ ], [ ], [ ], Central Intelligence Agency
[ ] , Special Agent, Boston Field Office, Federal Bureau of Investigation
[ ], Defense Intelligence Agency
[ ], Special Agent, Minneapolis Field Office, Federal Bureau of Investigation
[ ], National Security Agency Representative to Federal Bureau of Investigation
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], National Security Agency
Donald Kerr, Deputy Director of Central Intelligence for Science and Technology
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Defense Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], National Security Agency Representative to Federal Bureau of Investigation
[ ], Directorate for Science and Technology, Central Intelligence Agency
[ ], Former Counterterrorist Center, Central Intelligence Agency
David Kris, Associate Deputy Attorney General, Department of Justice
Capt. Michael Kuhn, US. Navy
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Phoenix Field Office, Federal Bureau of Investigation
Thomas Kuster, Director of Counterterrorism Policy, Department of Defense
[ ] , Assistant Special Agent In-Charge, San Diego Field Office,
Federal Bureau of Investigation
[ ], Supervisory Special Agent, Boston Field Office, Federal Bureau of Investigation
[ ], Language Specialist, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Headquarters, Federal Bureau of Investigation
Matthew Levitt, Washington Institute for Near East Policy
[ ], Supervisory Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Headquarters, Federal Bureau of Investigation
[ ] , Deputy Assistant Director, Inspection Division, Federal Bureau of Investigation
[ ], National Security Agency
[ ], National Security Agency
John Louder, National Reconnaissance Agency
Mark Lowenthal, Associate Director of Central Intelligence for Analysis and Production
[ ], Department of State
[ ], Headquarters, Federal Bureau of Investigation
[ ], Federal Bureau of Investigation
[ ], Supervisory Special Agent, Cleveland Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ] , Central Intelligence Agency
Claudio Manno, Federal Aviation Administration, Transportation Security Administration
[ ], Headquarters, Federal Bureau of Investigation
[ ], Headquarters, Federal Bureau of Investigation
[ ] , National Security Agency
[ ], Department of State
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], U.S. Navy
[ ], Assistant Special Agent In-Charge, New York Field Office, Federal Bureau of Investigation
Mary McCarthy, Former Senior Director for Intelligence Programs, National Security Council
Steven McCraw, Special Agent In-Charge, San Antonio Field Office, Federal Bureau of Investigation
[ ], Immigration and Naturalization Service Representative to Federal Bureau
of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
Barbara McN amara, Former Deputy Director, National Security Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Federal Bureau of Investigation
Mark Miller, Central Intelligence Agency Representative to Federal Bureau of Investigation
[ ] , Chief Information Officer, Central Intelligence Agency
[ ], Immigration and Naturalization Service
[], National Security Agency
Lt. Gen. Kenneth Minihan, Former Director, National Security Agency
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ] , Special Agent, Dallas Field Office, Federal Bureau of Investigation
[ ], Special Agent, Dallas Field Office, Federal Bureau of Investigation
[ ], Office of Homeland Security
[ ], National Security Agency
[ ], Defense Intelligence Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ] , Division Chief National Security Agency
[ ], [ ], [ ], Central Intelligence Agency
[ ], Former Analyst, Federal Bureau of Investigation
[ ], Analyst, Central Intelligence Agency
Lt. Gen. Gregory Newbold, Former Director of Operations, Joint Chiefs of Staff
[ ], Central Intelligence Agency
Glenn Nordin, Assistant Director of Intelligence Policy (Language), Department of Defense
[ ], Immigration and Naturalization Service
[ ], Defense Intelligence Agency
[ ], Headquarters, Federal Bureau of Investigation
[ ], Former Chief Counterterrorist Center, Central Intelligence Agency
[ ], Central Intelligence Agency Analyst, [ ]
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Analyst, Central Intelligence Agency
[ ] , Customs Representative to CIA Counterterrorist Center
[ ], Headquarters, Federal Bureau of Investigation
James Pavit, Deputy Director of Central Intelligence for Operations
[ ], Defense Intelligence Agency
[ ], Central Intelligence Agency Representative to FBI New York Field Office
[ ], Supervisory Special Agent, Dallas Field Office, Federal Bureau of Investigation
[ ], [ ], [ J] Central Intelligence Agency
Thomas Pickard, Former Deputy Director, Federal Bureau of Investigation
[ ], Supervisory Special Agent, Federal Bureau of Investigation
[ ], Assistant Special Agent In-Charge, Sacramento Field Office, Federal Bureau of Investigation
Paul Pillar, National Intelligence Officer for Near East, South Africa, Central Intelligence Agency
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation
John Pistole, Deputy Assistant Director, Counterterrorism Division, Federal Bureau of Investigation
[ ], Special Agent, New York Field Office, Federal Bureau of Investigation
[ ], Assistant General Counsel, Federal Bureau of Investigation
[ ], Unit Chief Federal Bureau of Investigation
[ ], Deputy Director, Office of Budget, Central Intelligence Agency
[ ], Office of General Counsel, National Security Agency
[ ], Assistant Special Agent In-Charge, Boston Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Analyst, Counterterrorist Center, Central Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
COL Richard G. Reynolds, Defense Attache, Amman, Jordan
Keith Rhodes, Chief Technologist, Center for Technology and Engineering, General Accounting Office
Susan Rice, Former Senior Director for African Affairs, National Security Council
[ ], Analyst, [ ], Central Intelligence Agency
[ ], Central Intelligence Agency
[ ], U. S. Customs Service
[ ], Language School, Central Intelligence Agency
[ ], Federal Aviation Administration
Michael Rolince, Headquarters, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Federal Bureau of Investigation Special Agent attached to Joint Terrorist Task Force
[ ], Special Agent, Minneapolis Field Office, Federal Bureau of Investigation
Colleen Rowley, Principal Legal Advisor, Minneapolis Field Office, Federal Bureau of Investigation
Mary Ryan, Assistant Secretary of State for Consular Affairs
[ ], Office of General Counsel, Federal Bureau of Investigation
[ ], Federal Aviation Administration Representative to Federal Bureau of Investigation
[ ], Special Agent, Minneapolis Field Office, Federal Bureau of Investigation
Jerry Savage, Office of Inspector General, Department of Defense
[ ], Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Central Intelligence Agency, [ ]
[ ], Central Intelligence Agency
[ ], Central Intelligence Agency
John Schuhart, Director, Resource Management Office, Community Management Staff
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], National Security Agency Representative to Deputy Director of Central Intelligence
[ ], [ ], [ ], Central Intelligence Agency
[ ], Oklahoma City Field Office, Federal Bureau of Investigation
[ ], Directorate of Science and Technology, Central Intelligence Agency
[ ], National Security Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], National Security Agency
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
Michael Sheehan, Ambassador to the UN; former Coordinator for Counterterrorism, Department of State
Michael Sheehy, Minority Staff Director, House Permanent Select Committee on Intelligence
Gen. Hugh Shelton, Former Chairman, Joint Chiefs of Staff
[ ], Director, Office of the Budget, Central Intelligence Agency
[ ], Defense Intelligence Agency
[ ], Central Intelligence Agency, [ ], [ ]
[ ], Deputy Counsel for Operations, Department of Justice
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
James Sloan, Director, Financial Crimes Enforcement Network, Department of Treasury
[ ], National Security Agency
[ ], Immigration and Naturalization Representative to CIA Counterterrorist Center
[ ] , Special Agent, Kansas City Field Office, Federal Bureau of Investigation
[ ], Department of State
[ ], Special Agent, New York City Field Office, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Headquarters Analyst, Federal Bureau of Investigation
[ ], Counterterrorist Center Analyst, Central Intelligence Agency
[ ], National Security Agency
Roy Surrett, Director of Intelligence, U.S. Customs Service
[ ], Supervisory Special Agent San Diego Field Office, Federal Bureau of Investigation
[ ], Language Specialist, Federal Bureau of Investigation
[ ], Special Agent, San Diego Field Office, Federal Bureau of Investigation
Francis X. Taylor, Ambassador at Large for Coordination and Implementation of Government-wide
US. Counterterrorism Policy, Department of State
Richard Taylor, Former Deputy Director of Operations, National Security' Agency
[ ] , Joint Intelligence Task Force-Counterterrorism, Defense Intelligence Agency
[ ], Headquarters Analyst, Federal Bureau of Investigation
[ ], National Security Agency
[ ], Inspection Division, Federal Bureau of Investigation
[ ], Supervisory Special Agent, San Diego Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
Frances Fragos Townsend, Former Counsel for Intelligence Policy, Department of Justice
[ ], Central Intelligence Agency
[ ], Directorate of Operations Senior Official, Central Intelligence Agency
[ ], Boston Field Office, Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Headquarters Analyst, Federal Bureau of Investigation
[ ], Analyst, National Security Agency
[ ] , Chicago Field Office, Federal Bureau of Investigation (Retired)
[ ], [ ], [ ], [ ], Central Intelligence Agency
[ ], Defense Intelligence Agency
[ ], Federal Bureau of Investigation
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Chief of Operations, [ ] Central Intelligence Agency
Maj. Gen. Ward, U.S. Army, Vice Director of Operations, Joint Chiefs of Staff
[ ], Defense Intelligence Agency, Department of Defense
[ ], Directorate for Science and Technology, Central Intelligence Agency
Dale Watson, Executive Assistant Director for Counterterrorism and Counterintelligence,
Federal Bureau of Investigation
William Webster, Former Director of Central Intelligence, Former Director, Federal Bureau of Investigation
[ ], [ ], [ ], [ ], National Security Agency
[ ], Financial Review Group, Federal Bureau of Investigation
[ ] , Counterterrorist Center, Central Intelligence Agency
[ ], Counterterrorist Center Analyst, Central Intelligence Agei1cy
Linton Wells, Principal Deputy Assistant Secretary of Defense (Command, Control, Communications
and Intelligence), Department of Defense
[ ], Central Intelligence Agency
[ ], [ ], [ ], Central Intelligence Agency
Mary Jo White, Former U.S. Attorney for the Southern District of New York
[ ], Counterterrorist Center, Central Intelligence Agency
[ ], Former Special Agent, Milwaukee Field Office, Federal Bureau of Investigation
[ ], Special Agent, Phoenix Field Office, Federal Bureau of Investigation
[ ] , Central Intelligence Agency
[ ], Central Intelligence Agency Representative to Federal Bureau of Investigation
[ ], [ ], [ ], [ ], National Security Agency
Vice Adm. Thomas Wilson (Ret), Former Director, Defense Intelligence Agency
[ ] , Boston Field Office, Federal Bureau of Investigation
[ ], National Security Law Unit, Federal Bureau of Investigation
[ ], Finance Division, Federal Bureau of Investigation
James Woolsey, Former Director of Central Intelligence
[ ], Former Special Agent, Chicago Field Office, Federal Bureau of Investigation
Austin Yamada, Deputy Assistant Secretary of Defense for Special Operations, Department of Defense
[ ], Special Agent, Oklahoma City Field Office, Federal Bureau of Investigation
Wayne Zaidemann, Legal Attache, Amman, Jordan, Federal Bureau of Investigation
- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
APPENDIX
COUNTERTERRORISM ORGANIZATIONS WITHIN THE INTELLIGENCE COMMUNITY
COUNTERTERRORISM ORGANIZATIONS WITHIN THE INTELLIGENCE COMMUNITY
(As of December 31, 2002)
The U.S. Intelligence Community currently consists of the Office of the Director of Central Intelligence, the Central Intelligence Agency, the National Security Agency, the Defense Intelligence Agency, the National Imagery and Mapping Agency, the National Reconnaissance Office, other specialized offices within the Department of Defense, the intelligence elements of the military services, the Federal Bureau of Investigation, the Department of the Treasury, the Department of Energy, the Bureau of Intelligence and Research of the Department of State, and the Coast Guard.
PRIMARY COUNTERTERRORISM AGENCIES
Central Intelligence Agency (CIA)
The Counterterrorist Center (CTC) is the CIA's primary counterterrorism component. In 1993, a special unit was established within the CTC, the Bin Ladin Issue Station, with personnel from CIA, NSA, FBI and other agencies to develop intelligence on Bin Ladin and his organization. The CIA worked alone and with friendly foreign intelligence services to disrupt Bin Ladin, degrade his ability to engage in terrorism, and bring him to justice.
[Within CTC, several units focus on al-Qa'ida:
• The [ ] Extremist CT Operations Group, the CTC operational arm, tracks al-Qa'ida and other [ ] radical groups. In 1996, the CTC created [the Bin Ladin Issue] Station to target Bin Ladin and his network, [ ]. The CTC's [ ] Extremist Branch also follows a range of radical [ ] groups, which are not part of al-Qa'ida, but often share personnel, provide logistical support, or otherwise assist it.
• The Office of Terrorism Analysis, the CTC's analytic arm, is responsible for providing analytical products on terrorism. OTA now has approximately [-] analysts. Before September 11, its [-] analysts were part of the smaller Assessments and Information Group, which was organized into five branches, only one of which focused (partially) on Bin Ladin.
1
• [The Renditions Group (formerly the Renditions Branch) [ ]. From 1986 to September 2001, the Renditions Branch was involved in several dozen renditions].
• [The Financial Operations Group, which was established after September 11, grew out of the Bin Ladin Station's efforts to track Bin Ladin's financial activities. [ ].
The CIA developed an operational strategy, referred to as "the Plan," so that CTC could react quickly to operational opportunities, renditions, and analysis to disrupt and capture Bin Ladin and his principal lieutenants.
To execute its plan against Bin Ladin, CTC developed a program to train and position personnel and move experienced operations officers into the Center to identify, vet, and hire qualified personnel for counterterrorism assignments. They sought fluency in Mid-East and South-Asian languages, combined with police, military, business, technical, or academic expertise, and established an eight week advanced counterterrorism operations course.
From 1999 to September 11, human intelligence sources against terrorism grew by more than fifty percent. Working across agencies, and in some cases with foreign services, the CIA designed and built [ ] for specific use against Al-Qa'ida inside Afghanistan. By September 11, sufficient collection programs and human networks were in place to cover almost all of Afghanistan.
Federal Bureau of Investigation (FBI)
The FBI within the Department of Justice is the principal law-enforcement arm of the government and the lead agency responsible for counterterrorism in the United States.
In 1999, the Counterterrorism Division was established in FB1 Headquarters, incorporating the International Terrorism Operations Division, the Domestic Terrorism Division, the National Domestic Preparedness Office, and the National Infrastructure Protection Center. The Radical Fundamentalist Unit and the Bin Ladin Unit became operational units within the International Terrorism Operations Section. These units advise field offices on Attorney General Guidelines and coordinate field terrorism investigations.
Since the 1980s, the FBI's New York Field Office has had the principal role in the FBI's counterterrorism effort. It has been the lead field office for Bin Ladin investigations and was the first to establish a Joint Terrorism Task Force of state and federal law enforcement and intelligence personnel.
2
A reorganization of the FBI's Counterterrorism Division was announced in May 2002, which includes:
• Headquarters centralization of counterterrorism programs
• Joint Terrorism Task Forces in all field offices and a National JTTF at Headquarters
• Flying Squads to support field operations
• Enhanced counterterrorism and analytical training Shifting 518 field agents from criminal investigations to counterterrorism
National Security Agency (NSA)
Within NSA, a Department of Defense entity, responsibility for collecting, processing, analyzing, and reporting signals intelligence (SIGINT) is centered principally within the Signals Intelligence Directorate created in February 2001, Within SID, the Counterterrorism Product Line has the lead for SIGINT production on counterterrorism targets. CT Product Line personnel increased from approximately [ ] before September 11 to about [ ] in Apri12002.
A portion of NSA's counterterrorism SIGINT reports comes from other product lines within SID:
• [ ].
• [ ].
• [ ].
• [ ].
Department of State
The Bureau of Intelligence and Research (INR), the intelligence arm of the Department of State, has three units involved in counterterrorism: the Office of Analysis for Terrorism, Narcotics and Crime, the Office of Intelligence Coordination, and the Office of Intelligence Operations. Outside INR, a Coordinator for Counterterrorism is responsible for developing counterterrorism policy.
The State Department also works closely with the Justice Department's Immigration and Naturalization Service to prevent terrorist suspects from entering the United States. To this end, the State Department maintains two key counter-terrorism databases:
3
• TIPOFF, a classified database within INR containing the names of foreigners who are not allowed to enter the United States because of ties to terrorism and other illegal activities and
• The Consular Lookout and Support System (CLASS), an unclassified database designed to assist in visa processing.
Information in TIPOFF and CLASS is derived from the Intelligence Community and other sources, such as the Immigration and Naturalization Service, the Drug Enforcement Agency, the Customs Service, and the Federal Aviation Authority. All consular officers must use the CLASS system before issuing visas.
Defense Intelligence Agencv (DIA)
DIA is the Department ofDefense element that produces and manages intelligence for the Secretary of Defense. Within DIA, the offices principally responsible for counterterrorism include the Defense Human Intelligence Service and the Joint Intelligence Task Force-Combating Terrorism.
Since July 2001, the Joint Terrorism Task Force -Counterterrism (JITF-CT) has been the focal point for all DlA counterterrorism analysis and production. The JITF-CT provides warnings, threat assessments, and all-source analysis and production and serves as a counterterrorism knowledge base within the Department of Defense.
Department of Transportation (DoT)
Within DoT, the U.S. Coast Guard and the Transportation Security Administration playa role in the government's counterterrorism mission. Pursuant to the Intelligence Authorization Act of2 002, the Coast Guard has become an Intelligence Community member. After September 11, DoT established the Transportation Security Administration, within which the Transportation Security Intelligence Service coordinates intelligence support and provides current and strategic warnings on threats to U.S. transportation.
Department of Treasury
Within Treasury, the Financial Crimes Enforcement Network is responsible for assisting U.S. intelligence and law enforcement agencies in tracking the movement of terrorist funds.
4
APPENDIX
EVOLUTION OF THE TERRORIST THREAT AND THE U.S. RESPONSE
1983-2001
COUNTERTERRORISM ORGANIZATIONS WITHIN THE INTELLIGENCE COMMUNITY
COUNTERTERRORISM ORGANIZATIONS WITHIN THE INTELLIGENCE COMMUNITY
(As of December 31, 2002)
The U.S. Intelligence Community currently consists of the Office of the Director of Central Intelligence, the Central Intelligence Agency, the National Security Agency, the Defense Intelligence Agency, the National Imagery and Mapping Agency, the National Reconnaissance Office, other specialized offices within the Department of Defense, the intelligence elements of the military services, the Federal Bureau of Investigation, the Department of the Treasury, the Department of Energy, the Bureau of Intelligence and Research of the Department of State, and the Coast Guard.
PRIMARY COUNTERTERRORISM AGENCIES
Central Intelligence Agency (CIA)
The Counterterrorist Center (CTC) is the CIA's primary counterterrorism component. In 1993, a special unit was established within the CTC, the Bin Ladin Issue Station, with personnel from CIA, NSA, FBI and other agencies to develop intelligence on Bin Ladin and his organization. The CIA worked alone and with friendly foreign intelligence services to disrupt Bin Ladin, degrade his ability to engage in terrorism, and bring him to justice.
[Within CTC, several units focus on al-Qa'ida:
• The [ ] Extremist CT Operations Group, the CTC operational arm, tracks al-Qa'ida and other [ ] radical groups. In 1996, the CTC created [the Bin Ladin Issue] Station to target Bin Ladin and his network, [ ]. The CTC's [ ] Extremist Branch also follows a range of radical [ ] groups, which are not part of al-Qa'ida, but often share personnel, provide logistical support, or otherwise assist it.
• The Office of Terrorism Analysis, the CTC's analytic arm, is responsible for providing analytical products on terrorism. OTA now has approximately [-] analysts. Before September 11, its [-] analysts were part of the smaller Assessments and Information Group, which was organized into five branches, only one of which focused (partially) on Bin Ladin.
1
• [The Renditions Group (formerly the Renditions Branch) [ ]. From 1986 to September 2001, the Renditions Branch was involved in several dozen renditions].
• [The Financial Operations Group, which was established after September 11, grew out of the Bin Ladin Station's efforts to track Bin Ladin's financial activities. [ ].
The CIA developed an operational strategy, referred to as "the Plan," so that CTC could react quickly to operational opportunities, renditions, and analysis to disrupt and capture Bin Ladin and his principal lieutenants.
To execute its plan against Bin Ladin, CTC developed a program to train and position personnel and move experienced operations officers into the Center to identify, vet, and hire qualified personnel for counterterrorism assignments. They sought fluency in Mid-East and South-Asian languages, combined with police, military, business, technical, or academic expertise, and established an eight week advanced counterterrorism operations course.
From 1999 to September 11, human intelligence sources against terrorism grew by more than fifty percent. Working across agencies, and in some cases with foreign services, the CIA designed and built [ ] for specific use against Al-Qa'ida inside Afghanistan. By September 11, sufficient collection programs and human networks were in place to cover almost all of Afghanistan.
Federal Bureau of Investigation (FBI)
The FBI within the Department of Justice is the principal law-enforcement arm of the government and the lead agency responsible for counterterrorism in the United States.
In 1999, the Counterterrorism Division was established in FB1 Headquarters, incorporating the International Terrorism Operations Division, the Domestic Terrorism Division, the National Domestic Preparedness Office, and the National Infrastructure Protection Center. The Radical Fundamentalist Unit and the Bin Ladin Unit became operational units within the International Terrorism Operations Section. These units advise field offices on Attorney General Guidelines and coordinate field terrorism investigations.
Since the 1980s, the FBI's New York Field Office has had the principal role in the FBI's counterterrorism effort. It has been the lead field office for Bin Ladin investigations and was the first to establish a Joint Terrorism Task Force of state and federal law enforcement and intelligence personnel.
2
A reorganization of the FBI's Counterterrorism Division was announced in May 2002, which includes:
• Headquarters centralization of counterterrorism programs
• Joint Terrorism Task Forces in all field offices and a National JTTF at Headquarters
• Flying Squads to support field operations
• Enhanced counterterrorism and analytical training Shifting 518 field agents from criminal investigations to counterterrorism
National Security Agency (NSA)
Within NSA, a Department of Defense entity, responsibility for collecting, processing, analyzing, and reporting signals intelligence (SIGINT) is centered principally within the Signals Intelligence Directorate created in February 2001, Within SID, the Counterterrorism Product Line has the lead for SIGINT production on counterterrorism targets. CT Product Line personnel increased from approximately [ ] before September 11 to about [ ] in Apri12002.
A portion of NSA's counterterrorism SIGINT reports comes from other product lines within SID:
• [ ].
• [ ].
• [ ].
• [ ].
Department of State
The Bureau of Intelligence and Research (INR), the intelligence arm of the Department of State, has three units involved in counterterrorism: the Office of Analysis for Terrorism, Narcotics and Crime, the Office of Intelligence Coordination, and the Office of Intelligence Operations. Outside INR, a Coordinator for Counterterrorism is responsible for developing counterterrorism policy.
The State Department also works closely with the Justice Department's Immigration and Naturalization Service to prevent terrorist suspects from entering the United States. To this end, the State Department maintains two key counter-terrorism databases:
3
• TIPOFF, a classified database within INR containing the names of foreigners who are not allowed to enter the United States because of ties to terrorism and other illegal activities and
• The Consular Lookout and Support System (CLASS), an unclassified database designed to assist in visa processing.
Information in TIPOFF and CLASS is derived from the Intelligence Community and other sources, such as the Immigration and Naturalization Service, the Drug Enforcement Agency, the Customs Service, and the Federal Aviation Authority. All consular officers must use the CLASS system before issuing visas.
Defense Intelligence Agencv (DIA)
DIA is the Department ofDefense element that produces and manages intelligence for the Secretary of Defense. Within DIA, the offices principally responsible for counterterrorism include the Defense Human Intelligence Service and the Joint Intelligence Task Force-Combating Terrorism.
Since July 2001, the Joint Terrorism Task Force -Counterterrism (JITF-CT) has been the focal point for all DlA counterterrorism analysis and production. The JITF-CT provides warnings, threat assessments, and all-source analysis and production and serves as a counterterrorism knowledge base within the Department of Defense.
Department of Transportation (DoT)
Within DoT, the U.S. Coast Guard and the Transportation Security Administration playa role in the government's counterterrorism mission. Pursuant to the Intelligence Authorization Act of2 002, the Coast Guard has become an Intelligence Community member. After September 11, DoT established the Transportation Security Administration, within which the Transportation Security Intelligence Service coordinates intelligence support and provides current and strategic warnings on threats to U.S. transportation.
Department of Treasury
Within Treasury, the Financial Crimes Enforcement Network is responsible for assisting U.S. intelligence and law enforcement agencies in tracking the movement of terrorist funds.
4
APPENDIX
EVOLUTION OF THE TERRORIST THREAT AND THE U.S. RESPONSE
1983-2001
Evolution of the terrorist threat and U.S. response, 1983-2001
The Building Threat: Pre-1993
Year / "Big picture" view / Selected, major terrorist events / U.S. institutional responses to terrorism
1979 / Soviet invasion of Afghanistan. Lebanese civil war already underway / -- / --
1980 / -- / -- / First FBI Joint Terrorism Task Force establish in NY City.
1981 / -- / -- / --
1982 / Jun. Israeli invasion of Lebanon. Sep. U.S. Marine peacekeeping presence established in Lebanon following assassination of Lebanese President. / -- / --
1983 / -- / 18 Apr. Bombing of U.S. embassy in Beirut. 63 killed, including CIA's Middle East director. 120 injured. (Islamic Jihad.) 23 Oct. Marine barracks bombing in Beirut. 241 Marines killed. French base attacked. (Islamic Jihad.) / --
1984 / 26 Feb. U.S. Marines depart Lebanon. / 16 Mar. CIA officer William Buckley kidnapped in Beirut. Other U.S. citizens not connected to the U.S. government are kidnapped over the next two years.
12 Apr. Hezbollah bombed restaurant near U.S. airbase near Torrejon, Spain, killing 18 U.S. servicemen. 83 injured.
20 Sep. Hezbollah Bombing of U.S. embassy annex in Beirut. 14 Americans killed. / --
1985 / -- / 14 Jun. TWA 847 hijacked by Hezbollah terrorists.
7 Oct. Achille Laura hijacking. Palestinian Liberation Front took 700 hostages. 1 U.S. citizen killed.
23 Nov. Egypt Air flight from Athens to Malta carrying several U.S. citizens hijacked by Abu Nidal Group.
Dec. Rome Nienna airport bombings by Abu Nidal Organization. / Dec. Vice President's Report on Combating Terrorism. 40 recommendations. Key recommendations: Presidential [directive] regarding terrorism, National Security Decision Directive 207, establish a CTC.
1986 / -- / 30 Mar. Palestinian splinter group detonated a bomb as TWA 840 approached Athens, killing four U.S. citizens.
5 Apr. Bombing of La Belle disco in Berlin, Germany, killing two U.S. servicemen and one Turkish civilian. 200 wounded. Traced to Libyan perpetrators. / 20 Jan. President signs NSDD-207, which delineates broad outlines of U.S. government policy for dealing with terrorism and set in place government-wide mechanisms for responding to the emerging threat.
Feb/Mar. CIA establishes CTC
9 Apr. Operation El Dorado Canyon. U.S. bombing of Libya.
Spring. Directive signed that authorizes CIA to conduct certain counterterrorism activities.
27 Aug. Omnibus Diplomatic Security and Antiterrorism Act expands FBI jurisdiction to include violence against U.S. nationals abroad.
1987 / -- / Sep. Rendition of Fawaz Yunis, wanted for hijacking Royal Jordanian airliner in which 6 Americans killed. [ ]. [ ]. / --
1988 / -- / 17 Feb. U.S. Marine LtCol William Higgins kidnapped/murdered by Iranian-backed Hezbollah.
14 Apr. Organization of Jihad Brigades exploded a car bomb outside a USO club in Naples, Italy, killing one U.S. sailor.
21 Dec. Bombing of Pan Am 103 over Lockerbie, Scotland. / --
1989 / 15 Feb. Soviet withdrawal from Afghanistan completed. / -- / 13 Oct. Terrorist Threat Warning System established.
1990/ Aug. Iraq invades Kuwait. U.S. launches Operation Desert Shield. / -- / --
1991 / Jan-Mar. Operation Desert Storm expels Iraqi forces from Kuwait.
Apr. Operation Provide Comfort. Safe havens for Kurdish refugees in northern Iraq. This operation eventually becomes enforcement of no-fly zones over northern/southern Iraq, operations which continue to this day and resulted in a large, semi-permanent U.S. military presence in the Persian Gulf region. / Jan/Feb. CTC thwarts Iraqi agents' plans worldwide.
18-19 Jan. Iraqi agents planted bombs at the U.S. Ambassador to Indonesia's residence and at the USIS library in Manila / --
1992 / Rise of jihadist movement.
Dec. U.S. Operation Restore Hope to provide Humanitarian relief to Somalia. / Dec. Attack on Aden hotel housing U.S. service members for the operation in Somalia. Possibly the first attack by UBL's network. / --
- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Re: Report of the Joint Inquiry Into the Terrorist Attacks o
The Hunt for bin Ladin, 1993-2001
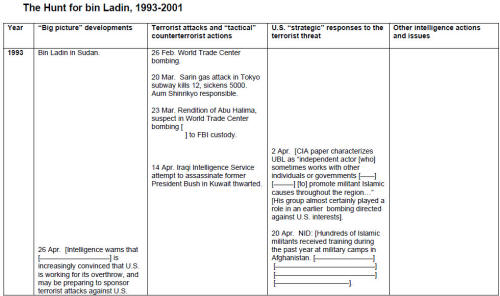
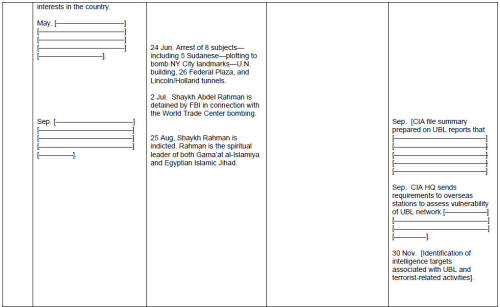

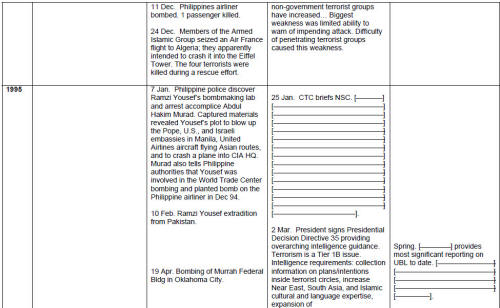
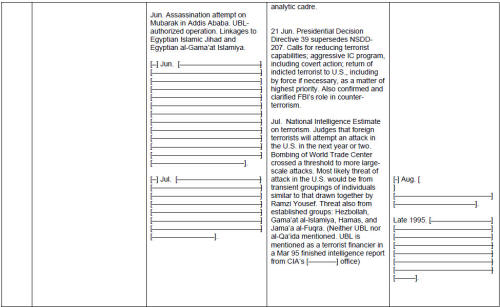
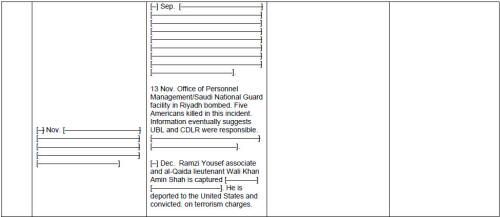
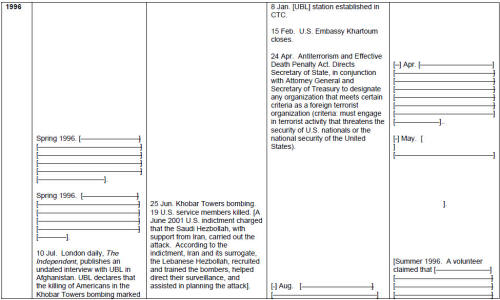
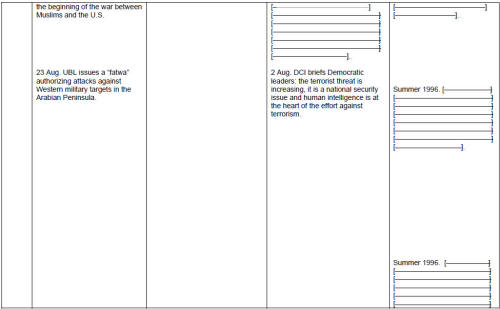












- admin
- Site Admin
- Posts: 36135
- Joined: Thu Aug 01, 2013 5:21 am
Return to Another View on 9/11
Who is online
Users browsing this forum: No registered users and 12 guests