PropOrNot: Is It Propaganda or Not?: Your Friendly Neighborhood Propaganda Identification Service, Since 2016!
Black Friday Report: On Russian Propaganda Network Mapping
By The PropOrNot Team
November 26th, 2016
NOTICE: THIS WORK MAY BE PROTECTED BY COPYRIGHT
YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.
Web: http://www.propornot.com
Twitter: http://www.twitter.com/propornot
Reddit: http://www.reddit.com/r/propornot/
Email: [email protected]
Thanks to the Generous Sponsorship of: Nobody (Funding? Hah!)
Executive Summary:
Russia’s attempts to influence the U.S. election via hacking and selectively leaking sensitive U.S. government and political data were not conducted in isolation. They were accompanied by large-scale, long-term efforts to build online “fake news” propaganda outlets with significant audiences in the U.S. PropOrNot has so far identified over 200 distinct websites, YouTube channels, and Facebook groups which qualify as Russian propaganda outlets according to our criteria and target audiences in the United States. Drawing on existing research and using a combination of automated and manual review techniques, we estimate the regular U.S. audiences of these outlets to number in the tens of millions. We are currently gathering data to measure that more precisely, but are confidant that it includes at least 15 million Americans.
Table of Contents:
• Background on PropOrNot
• Characteristics of Identified Sites
• Methodology
• A Prior-Research Case Study: ZeroHedge.com
• Spidering, Correlating, Reviewing, Spidering
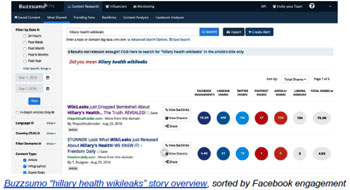
• Following a Specific Story: The Tale of the Painted Jets
• Following a Specific Story: The Tale Hillary Clinton’s “Parkinson’s”
• Following a Specific Story: Ourselves!
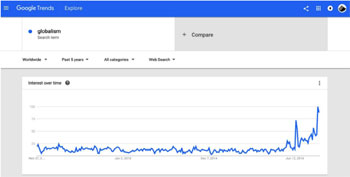
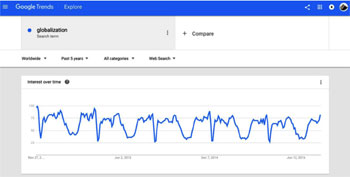
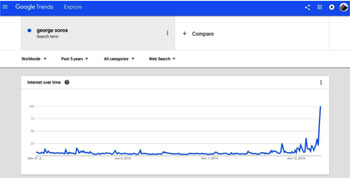
• Using Google Trends to Measure Larger-Scale Effects
• Preliminary Conclusions
• Next Steps
Introduction and Context
Throughout the election season of 2016, an increasing number of reporters and journalists have done remarkable work investigating the origins and operations of “fake news” outlets on the internet. Some notable examples include:
How Facebook powers money machines for obscure political 'news' sites
By Dan Tynan, Aug 24 2016, The Guardian
Online Scam Artists Are Using Hoaxes About Terrorist Attacks To Make Money
By Craig Silverman, Aug 19 2016, Buzzfeed News
Facebook Made This Sketchy Website’s Fake Story A Top Trending Topic
Craig Silverman, Aug 29 2016, Buzzfeed News
We Tracked Down A Fake-News Creator In The Suburbs. Here's What We Learned
Larua Sydell, Nov 23 2016, NPR
Seattle’s own ‘click-bait’ news site serves up red meat for liberals
Danny Westneat, Nov 25, 2016, Seattle Times
How Fake News Goes Viral: A Case Study
Sapna Maheshwari, November 20 2016, New York Times
Buzzfeed News in particular has done pioneering analytical work on this, and their stories on the “fake news” issue are an excellent resource. Public discussion has now correctly recognized that “fake news” is a serious problem with real-world consequences, and a number of innovative actors have started to discuss, research, and develop potential solutions. However, the public discussion of all this has, until very recently, generally assumed that the “fake news” problem has been mostly driven by “clickbait”-style commercial motivations:
Renegade Facebook Employees Form Task Force To Battle Fake News
Sheera Frenkel, Nov 14 2016, BuzzFeed News
Facebook's Fight Against Fake News Was Undercut by Fear of Conservative Backlash
Michael Nunez, Nov 14 2016, Gizmodo
Here’s a Chrome Extension That Will Flag Fake-News Sites for You
By Brian Feldman, Nov 15, 2016, New York Magazine
We Have a Bad News Problem, Not a Fake News Problem
By David Mikkelson, Nov 17 2016, Snopes
How to Spot Fake News
By Lori Robertson and Eugene Kiely, Nov 18 2016, FactCheck.org
This evolving thread of stories analyzing “fake news” has been simultaneously accompanied by a very different but parallel thread of stories and public discussion about Russian cyberespionage, propaganda, and “active measures” targeted at the West. Reporting on this initially focused on Russian-backed comment-troll farms, but quickly expanded beyond that:
Documents Show How Russia’s Troll Army Hit America
By Max Seddon, Jun 2 2014, Buzzfeed News
The Agency: From a nondescript office building in St. Petersburg, Russia, an army of well-paid “trolls” has tried to wreak havoc all around the Internet — and in real-life American communities
By Adrian Chen, Jun 2 2015, New York Times
Salutin' Putin: Inside a Russian troll house
Shaun Walker in St Petersburg, The Guardian, 2 April 2015
While the public discourse correctly recognized that “fake news” was becoming a serious problem, especially in light of the election, very few journalists and researchers sought to systematically connect the dots between fake news and Russian cyberespionage, propaganda, and “active measures” generally. However, as the election season ramped up an increasing number of intrepid reporters and researchers started investigating this connection, which had been discussed extensively in the specialist press for years. Much of this research inspired our efforts at PropOrNot. For example:
Unmasking the Men Behind Zero Hedge, Wall Street's Renegade Blog
By Tracy Alloway and Luke Kawa, Apr 29, 2016, Bloomberg
Social Network Analysis Reveals Full Scale of Kremlin's Twitter Bot Campaign
Lawrence Alexander, Apr 2 2015, Global Voices
When Online Kremlin Propaganda Leaves the Web, It Looks Like This
Lawrence Alexander, Sep 29 2015, StopFake
Social Media as a Tool of Hybrid Warfare ,
Sanda Svetoka, Jul 7 2016, NATO StratCom
The Fringes of Disinfo: A Network Based on Referrers
By Andrew Aaron Weisburd, Feb 7 2016, in активные мероприятия
Putin's Army Of Internet Trolls Is Influencing The Hillary Clinton Email Scandal
By Paul Roderick Gregory, 5 June 2016, Forbes
Donald Trump and Vladimir Putin: Russia's information war meets the US election
By Chris Zappone, 15 June 2016, Sydney Morning Herald
The Kremlin’s Candidate: In the 2016 election, Putin’s propaganda network is picking sides
Michael Crowley, May/June 2016, Politico
Prof. Chodakiewicz discusses Russian military and influence operations at US Army Europe Senior Leaders Forum
Marek Jan Chodakiewicz, Jan 27 2015, Institute of World Politics,
Until very recently no public research connected the dots as extensively as this article:
Trolling for Trump: How Russia Is Trying to Destroy Our Democracy
By Andrew Weisburd, Clint Watts and JM Berger, Nov 6 2016, War on the Rocks
These previously separate threads of public discussion about “fake news” and about Russian propaganda are now, finally, being connected. In our view, this is long overdue. We at PropOrNot are proud to be contributing to that discussion.
Background on PropOrNot
We are an independent team of concerned American citizens with a wide range of backgrounds and expertise, including professional experience in computer science, statistics, public policy, and national security affairs. We are currently volunteering our time and skills to identify propaganda - particularly Russian propaganda - targeting a U.S. audience. We collect public-record information connecting propaganda outlets to each other and their coordinators abroad, analyze what we find, act as a central repository and point of reference for related information, and organize efforts to oppose it.
Some of our members have been aware of Russian influence operations in a professional context for quite some time, but others have become increasingly aware of existing research on the subject in light of recent events in Ukraine, Western Europe Europe, and the Middle East. We formed PropOrNot as an effort to prevent propaganda from distorting U.S. political and policy discussions. We hope to strengthen our cultural immune systems against hostile influence and improve public discourse generally.
We are completely independent, because we not funded by anyone, and we have no formal institutional affiliations. We are nonpartisan, in that our team includes all major political persuasions except the pro-Russian kind. We are anonymous for now, because we are civilian Davids taking on a state-based adversary Goliath, and we take things like the international Russian intimidation of journalists , “Pizzagate”-style mob harassment , and the assassination of Jo Cox very seriously, but we can in some cases provide background information about ourselves on a confidential basis to professional journalists. We do not publicly describe all of our sources and methods, although again, we can in some cases provide much more detail to journalists and other researchers in order to contextualize their reporting.
The growth of computers, the Internet, and niche marketing means that you don't have to be a Goliath to get along. Like David's sling, these new technologies empower the little guy to compete more effectively. They have, in fact, spawned a veritable army of Davids, now busily competing with the Goliaths in all sorts of fields. And, as with the beer, even where that competition is no real threat to the big guys, it tends to push them to do a better job.
-- An Army of Davids: How Markets and Technology Empower Ordinary People to Beat Big Media, Big Government, and Other Goliaths, by Glenn Reynolds
By enabling virtually anybody with a computer to disclose information to world, the Internet is dissolving the boundaries between professional journalists and amateurs. Glenn Reynolds, a law professor and author of the very popular blog Instapundit, extols the virtues of the amateur journalist in his book, An Army of Davids. With the growth of blogs, he observes, "power once concentrated in the hands of a professional few has been redistributed into the hands of the amateur many." Known as The Blogfather because he created one of the first blogs, Reynolds argues that "technology has made it possible for individuals to become not merely pamphleteers, but vital sources of news and opinion that rival large metropolitan publishers in audience and influence." For Reynolds, these developments are marvelous: "I don't think that weblogs and flash media will replace Big Media any time soon. But I keep seeing evidence that they're doing a better and better job of supplementing, and challenging, Big Media coverage. I think that's a wonderful thing, and it's one reason why I'm such an evangelist for the spread of enabling technologies like Web video and cheap digital cameras."
-- The Future of Reputation: Gossip, Rumor, and Privacy on the Internet, by Daniel J. Solove
It’s the volume of work being produced that tips you off that you may be dealing with a professional hatchet-man. As I review the products of research into Popehat, I’m struck by the amount of time spent on the activity, and the very large number of his Rapeutation victims. I gradually have drifted from thinking that it was absurd to imagine he’d be getting paid to conduct Rapeutations to entertaining the possibility in theory, to definitely not ruling it out.
He could be working for somebody steady, like Lenny Sands works for Howard Hughes in James Ellroy’s “American Tabloid,” stalking and exposing Hollywood personalities Hughes wants to pressure for business purposes, or wants to crush because they obstruct his right wing social agendas. Or he could run a sleaze-for-hire shop of that sort that have existed in LA since the first swindlers showed up to sell whatever suckers would pay for. Ellroy’s character Ward Littell, a lawyer/FBI agent who turns from a Kennedy worshipper to a conspirator in his assassination, is the very epitome of a person who traffics in black information, gathered from law enforcement, private investigators and freelance mercenaries at a very high level. Ken Popehat White might be a sort of micro-version of Ward Littell, gathering his information from his “army of Davids,” and spreading his poison through the same network.
-- Sparking Up A Cyber-Frankenstein: Pushing Yellow Journalism To The Megacrowd, by Charles Carreon
Safe inside his cover story, Popehat is machinating like L. Ron Hubbard targeting suppressives. His head thrust against his periscope, he ceaselessly scans the sea for the latest foolish captain to pilot the S.S. Douchebag into his sights. “Fire 1! Fire 2!” A pause to gauge the effects, then, “We hit her amidships!” Popehat’s crew roars with triumph, and Popehat himself, oblivious to all but the delicious sensation of having his hindquarters laved by eager tongues, hoarsely exhorts his “army of Davids” to further reputational mayhem.
-- Embarrassing Followers, by Charles Carreon
http://www.popehat.com/2012/12/26/vote-in-the-secondannual-popehat-censorious-asshat-of-the-year-poll/ White conceived a special dislike for the Lawyer, recruiting readers to play a “Twitter hashtag game: #charlescarreonnewcareers,” and recruited them as an “Army of Davids” to “take a screenshot or print … to pdf [any] web page” showing that the Lawyer had made “an inconsistent statement [or] shows hypocrisy.” (Carreon Dec. ¶ 5; Exhibit 1.) When served with a subpoena for documents in this case, White responded with the disclosure that he had exchanged over 200 emails with the Gripesite Operator, and refused to produce anything, claiming that the Lawyer possesses “animus” towards White. (Carreon Dec. ¶ 5; Exhibit 2.)
Much of the footnote is true. I am a criminal defense attorney. I have a libertarian following. I deride attorneys, including Mr. Carreon, as censorious asshats. I conceived a special dislike for Mr. Carreon. I made up a hashtag game about him, and recruited people to point out where Mr. Carreon and his wife had engaged in rhetoric that was inconsistent with his contrived pearl-clutching horror over the contents of Mr. Inman's blog.
-- In Which Charles Carreon Says Mostly True Things About Me In A Footnote, by Ken White
You guys who keep coming up with the examples of falsehood and hypocrisy just rock. You're the Army of Davids. Do me a favor — whenever you find a good web page showing an inconsistent statement, or an item that shows hypocrisy, take a screenshot or print it to pdf in case he memory-holes it.
-- Kenneth Paul White, Popehat.com
Think of it as Mitt Romney’s revenge. When Romney suggested, back during the 2012 election, that Russia was the biggest geopolitical threat facing America, Barack Obama mocked him with a line lifted from Seinfeld, saying “The 1980s are now calling to ask for their foreign policy back because the Cold War’s been over for 20 years.”
Well, you wouldn’t know that to listen to Democrats talking today. Senate Minority Leader Harry Reid, D-Nev., has been issuing dark warnings of Russian election-tampering. In a letter sent to FBI Director James Comey, Reid warned that the threat of Russian election-tampering is more serious than generally appreciated (it’s like he’s been reading my columns on the subject or something!) and “may include the intent to falsify official election results.”
-- The Russians are coming, the Russians are coming!, by Glenn Harlan Reynolds
The leaks that are out are allegedly from a hacker calling himself Guccifer 2.0, but given that many suspect this is just a blind for Russian intelligence.
-- Putin for president 2016, by Glenn Harlan Reynolds
We are American, although our team includes Ukrainian-American, Iraqi-American, and quite a few other varieties of American members. We are united in our overall objectives: to identify, help counter, and eventually deter Russian propaganda. Any time an outlet consistently echoes, repeats, or refers its audience to Russian propaganda, we’re going to analyze it and call it out.
Characteristics of Identified Sites
We at PropOrNot do not reach our conclusions lightly. We have arrived at them after systematically employing a combination of manual and automated analysis, building on the work of other researchers and journalists, in order to map out a related collection of websites, social media, video, and other outlets, which:
1. Include official state-owned and semi-official Russian propaganda outlets, such as Russia Today , Sputnik News , Russia Insider , etc.;
2. Consistently cite official state-owned and semi-official Russian propaganda outlets, including the Russian defense ministry and other official spokespeople;
3. Consistently reuse text directly from official state-owned and semi-official Russian propaganda outlets and government spokespeople, often without attribution;
4. Have a history of generally echoing the Russian propaganda "line", by using themes, arguments, talking points, images, and other content similar to those used by official state-owned and semi-official Russian propaganda outlets;
5. Have a history of echoing the Russian propaganda "line" in ways unrelated to the purported focus of their branding, and in sequence with (at the same time as, or shortly after) official state-owned and semi-official Russian propaganda outlets;
6. Qualify as propaganda under a rigorous definition: “A systematic form of purposeful persuasion that attempts to influence the emotions, attitudes, opinions, and actions of specific target audiences for political, ideological, and religious purposes, through the controlled transmission of deceptive, selectively-omitting, and one-sided messages (which may or may not be factual) via mass and direct media channels”;
7. Have in many cases already been called out by other fact-checkers, researchers, journalists, or debunkers;
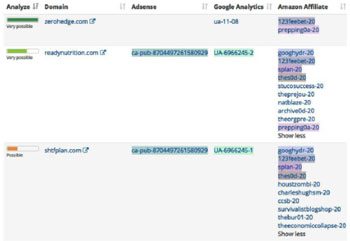
8. Share technical “tells” suitable for automated analysis, such as Google Analytics IDs, Amazon affiliate codes, WHOIS data, hosting data, ad-network utilization, SEO techniques, referral patterns, in some cases strongly suggesting direct Russian involvement;
9. Refer their audiences to each other, via hyperlinks and other means, at disproportionately high rates;
10. Are consistently visited by the same audiences, both directly and via search, demonstrating that those intra-network referrals build “brand loyalty” in their audiences over time;
11. Are consistently visited by their audiences after searches for terms which congrue with the Russian propaganda “line”, and are unrelated to the purported focus of their branding;
12. Are categorized as "similar sites" by automated services in spite of their purportedly distinct focuses;
13. Have content characterized by automated services in ways that are consistently very different from their purported subjects, but align with the Russian propaganda “line”;
14. Have content aligning with the “Eurasianist” philosophy of Alexander Dugin ;
15. Include specialized sites targeted at a wide range of seemingly unrelated audiences, including U.S. military veterans, Wall St. finance industry professionals, environmentalists, peace activists, racists, conspiracy theorists, and political junkies;
16. Appear to be effectively influencing public opinion in significant and very problematic ways, by promoting:
a. Conspiracy theories about and protests against U.S. military exercises (“Jade Helm”),
b. Isolationism and “anti-interventionism” for the US, but not for Russia,
c. Support for policies like Brexit, and the breakup of the EU and Eurozone,
d. Opposition to Ukrainian resistance to Russia and Syrian resistance to Assad,
e. Support for the anti-vax, anti-Zika spraying, anti-GMO, 9/11-”truther”, gold-standard, and other related movements;
17. Have extremely large audiences in the U.S., such that tens of millions of people appear to use them as primary “news” sources, supplanting actual journalism;
18. Appear to be part of a larger “active measures”-style Russian influence operation, which also includes hacking and selectively leaking sensitive U.S. government and political data, along with more-traditional espionage and military activity, intended to:
a. Confuse public opinion, encourage paranoia and passivity, and distract American audiences away from relying on actually-accurate journalism,
b. Blunt opposition to and strengthen popular support for Russian strategic priorities.
Please bear in mind that these characteristics of propaganda outlets are motivation-agnostic. They are independent of questions about whether the sites we’ve identified are being knowingly directed and paid by Russian intelligence officers, or whether they even knew they were echoing Russian propaganda at any particular point--if they display these characteristics, they are at the very least acting as " useful idiots " of the Russian intelligence services, and are worthy of further scrutiny.
We have been following recent reporting about for-profit political, commercial, and other kinds of clickbait, hoax, and fake-news sites, and while our automated tools and our manual techniques have occasionally identified sites as Russian propaganda which others have recently identified as commercially or otherwise motivated, if they meet our criteria, we see no reason not to flag them. Our tools are evolving, but because we focus on behavior, not motivation, we are less interested in why any particular outlet echoes or spreads Russian propaganda, than on whether they do. Whether for money or out of ideological affinity, the end results are the same.
Methodology
We use a combination of manual and automated analysis, including analysis of content, timing, technical indicators, and other reporting, in order to initially identify (“red-flag”) and then confirm an outlet as echoing, repeating, and referring its audience to Russian propaganda.
Our volunteers have developed multiple suites of software tools, leveraging publicly available data and commercial analytics services (like Quantcast , Alexa , SimilarWeb , uStat , SiteLinks , My Web of Trust , AnalyzeID , SocialBlade , and Buzzsumo , among others), in order to discover and perform automated analysis of Russian propaganda outlets, but everything we do is in principle replicable using manual searching and data entry.
We started our automated analysis from the domains and social-media accounts of Russian official and semi-official media outlets, including:
rt.com
sputniknews.com
therussophile.com
russia-insider.com
strategic-culture.org
katehon.org
theduran.com
http://www.fort-russ.com
thesaker.is
pravda.ru
tass.ru
We also drew on other public investigative journalistic reporting which highlights outlets and social media accounts as particularly and unusually pro-Russian, and, after doing our own research sometimes use them as starting points as well. This analysis is used as an example later in this report:
Unmasking the Men Behind Zero Hedge, Wall Street's Renegade Blog
By Tracy Alloway and Luke Kawa, Apr 29, 2016, Bloomberg
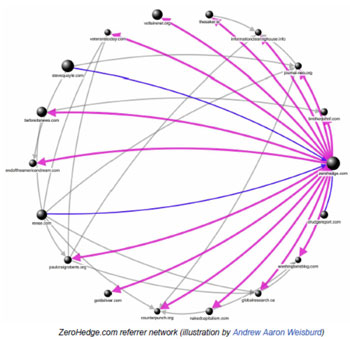
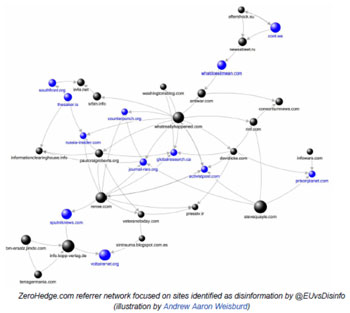
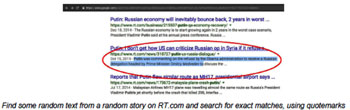
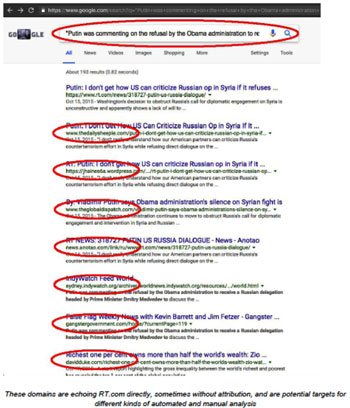
We then use our custom tools to “spider” out from those identified sites and accounts, discovering new, connected propaganda sites and social media accounts by examining their technical characteristics, including Google Analytics IDs, Amazon affiliate codes, WHOIS data, hosting data, ad-network utilization, SEO techniques, social media activity, and word-frequency metrics. We can then graph the results in various ways that highlight degrees of similarity, like this ego network diagram :
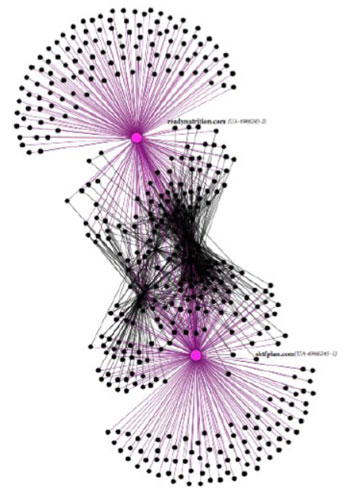
Ego network diagram illustrating link distance distance metric and density overlap between sites sharing technical identifiers (in this case, a Google Analytics ID)
We use previous reporting and automated analysis along with a systematic manual analysis process in order to flag, check, and double-check anything we review, in order to rigorously identify and expose Russian propaganda, avoid false positives and McCarthyism, and effectively encourage others to get their news from more reliable sources. As such, we have developed and use the following steps, or Checks, when performing manual analysis of potential propaganda outlets and highlighting them in various ways:
1) Check to see whether the social-media account/commenter/outlet consistently cites obvious Russian propaganda outlets such as Russia Today/rt.com, the Russian defense ministry, and other official Russian spokespeople.
2) Check to see whether the social-media account/commenter/outlet has a history of reusing text directly from obvious Russian propaganda outlets, especially without attribution.
3) Check to see whether the social-media account/commenter/outlet has a history of generally echoing the Russian propaganda "line" by using themes, arguments, talking points, images, and other content similar to those used by obvious Russian propaganda outlets. These themes include:
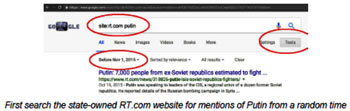
● How wonderful, powerful, innocent, and righteous Russia and Russia's friends are: Putin, Donald Trump, Bashar al-Assad, Syria, Iran, China, radical political parties in the US and Europe, etc. Investigate this by searching for mentions of, for example, "russia", on their site by Googling for "site:whateversite.com russia", and seeing what comes up.
● How terrible, weak, aggressive, and corrupt the the opponents of Russia and their friends are: The US, Obama, Hillary Clinton, the EU, Angela Merkel, NATO, Ukraine, Jewish people, US allies, the "mainstream media", and democrats, the center-right or center-left, and moderates of all stripes. Investigate this by searching for mentions of, for example, "NATO", on their site by Googling for "site:whateversite.com NATO" and seeing what comes up.
● An obvious bias towards Russia and Russian-backed policy in foreign affairs, including:
○ How fantastic Brexit and Ukrainian/Georgian separatism is, but how terrible Chechen separatists are,
○ How advanced Russian technology is, and how dangerous Western technology is,
○ How great it is when Western secrets get exposed, but how terrible it is when Russian ones do,
○ How militarily powerful Russia and their friends are, and how weak and craven Russia's enemies and their friends are, etc.
● How dangerous standing up to Russia would be: It would inevitably result in "World War 3", nuclear devastation, etc, and regardless of who shot first or is bombing civilians where now, would be the West's fault. Russian propaganda never suggests it would just result in a Cold War 2 and Russia's eventual peaceful defeat, like the last time.
● Pre-emptive discouragement of critical analysis: Assertions about them "having the truth", or the need to "wake up the sheeple", or how the "mainstream media" can't be trusted.
● Hyperbolic alarmism, anti-Western conspiracist insinuations, "Eurasianism", racism, gold-standard nuttery and attacks on the US dollar, 9/11-trutherism, anti-Semitism, anti-"globalism", anti-vax/anti-GMO paranoia, and generally ridiculous over-the-top assertions, which cites Russian propaganda outlets as "evidence".
Please review our Frequently Asked Questions and our Reference Articles pages on our site for more background.
4) Check to see whether the social-media account/commenter/outlet has a history of echoing the Russian propaganda "line" in weird ways:
● Do they have propaganda-like content that mentions Russia in a positive light for no clear reason?
● Do they have propaganda-like content that randomly extols Russia and belittles the US?
● Do they have propaganda-like content unrelated to the purported focus of their branding?
● Does the timing of their propaganda-like content coincide with or closely follow similar content on known Russian propaganda outlets?
5) Check to see whether the social-media account/commenter/outlet lacks the hallmarks of good actual journalism: Are the stories factual? Are the facts placed in appropriate context? Do the headlines match the content? Are the agendas of the sources clearly disclosed? Are there good explanations? Does it bring clarity to complicated issues? Is there an absence of hype?
6) Check to see whether the social-media account/commenter/outlet has been called out by other fact-checkers, journalists, debunkers, etc, already.
7) Check to see whether the social-media account/commenter/outlet steadfastly avoids coherently proposing constructive solutions to anything. The point of propaganda isn't just to get people worked up--it's also to create a sense of decision paralysis, and fear of a complex and seemingly frightening world.
8) Given all that, check to see whether the social-media account/commenter/outlet qualifies under our definition of propaganda:
A systematic form of persuasion that attempts to influence the emotions, attitudes, opinions, and actions of specified target audiences for political, ideological, and religious purposes, through the controlled transmission of deceptive, selectively-omitting, and one-sided messages (which may or may not be factual) via mass and direct media channels.
As an example of how this all can work, refer to our example post about this on our site, where we review the domain HangTheBankers.com .
After building on previous reporting, using our automated tools, and then checking our work manually, we again use our software tools to fill in the blanks, collecting a wide range of data about any new target sites discovered through the previous steps, and seeing how they might fit into the existing network of previously red-flagged and identified outlets. We have built out a significant network of websites, YouTube channels, Facebook pages, Twitter accounts, etc, which appear to be part of the same larger Russian influence operation. Every time we feel confidant that we have discovered most of them, we uncover more.
A Prior-Research Case Study: ZeroHedge.com
In some cases, traditional-journalist reporting has uncovered interesting connections between outlets which we have identified, through our multiple overlapping checks and analyses, as Russian propaganda. Take, for example, ZeroHedge.com , which we review on our site, but examine in more technical detail here.
Targeted at Wall St. professionals and people interested in the finance sector, it is now the 407th most-popular site in the United States (according to Alexa.com ), with 18.7m monthly page views in the U.S., averaging roughly 8 minutes a visit (according to SimilarWeb.com ). It is one of the top finance-industry news sources for American audiences, and was rated as one of the top ten most popular financial blogs in the U.S. by Time Magazine .
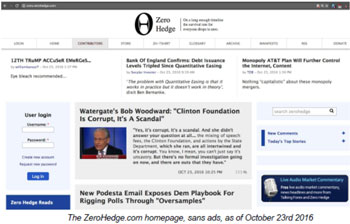
The ZeroHedge.com homepage, sans ads, as of October 23rd 2016
New York Magazine ran an extensive profile of the site, titled The Dow Zero Insurgency , in September 2009, doing some research into the site’s apparent founder, Daniel Ivandjiiski, and including this comment about Zerohedge’s tone:
“It’s nihilist, and that kind of vision lends itself to all manner of overreaching and conspiracy,” says Felix Salmon of Reuters. “You need some kind of critical judgment to separate out the [stories] that make sense and the ones that don’t. Zero Hedge just seems to not care about that. It doesn’t matter if it’s not true.”
LEO STRAUSS'S NIHILIST REVOLUTION: AN APOLOGY FOR TERROR
At the heart of Leo Strauss's political thought is an open apology for terrorism. This idea is illuminated in Strauss's exchange of comments with Alexandre Kojeve, a neo-Hegelian official of the French finance ministry, in the 1950s. At the heart of this debate is the question of the universal and homogenous state, and how philosophers should react to its existence. The universal homogenous state means something like a world where war and underdevelopment have been eliminated, and in which leisure time and well-being are rising. For most people, the universal homogenous state would look like a world of peace, progress, and prosperity.
But for Strauss and Kojeve, peace, progress, and prosperity mean the end of history because they wipe out the higher human values, which depend upon politics, and thus upon war. (Implicit also is the idea that peace, progress, and prosperity are bad for oligarchical domination, a cause dear to Strauss and Kojeve.) Strauss sums it up thus: "This end of History would be most exhilarating, but for the fact that, according to Kojeve, it is the participation in bloody political struggles as well as in real work or, generally expressed, the negating action, which raises man above the brutes." (Strauss 208)
For Strauss and Kojeve, "unlimited technological progress and its accompaniment, which are indispensable conditions of the universal and homogeneous state, are destructive of humanity. It is perhaps possible to say that the universal and homogeneous state is fated to come. But it is certainly impossible to say that man can reasonably be satisfied with it." (Strauss 208) This view of technology is that of the Greek historian called the Old Oligarch (who did not like the long walls and the Athenian navy), and is certainly not that of Plato. For Strauss, Greek philosophy is a screen upon which he projects his own ignorant opinions.
Not caring about what Plato really thought, Strauss advances towards his terrible conclusion: "If the universal and homogeneous state is the goal of History, History is absolutely 'tragic. ' Its completion will reveal that the human problem, and hence in particular the problem of the relation of philosophy and politics, is insoluble." (Strauss 208)
In Strauss's view, the imminent coming of the universal homogeneous state means that all progress accomplished by mankind to date has been worthless: "For centuries and centuries men have unconsciously done nothing but work their way through infinite labors and struggles and agonies, yet ever again catching hope, toward the universal and homogeneous state, and as soon as they have arrived at the end of their journey, they realize that through arriving at it they have destroyed their humanity, and thus returned, as in a cycle, to the prehuman beginnings of History." (Strauss 209)
This raises the question of the violent revolt against the universal homogeneous state, which is what Strauss regards as inevitable and desirable: "Yet there is no reason for despair as long as human nature has not been conquered completely, i.e., as long as sun and man still generate man. There will always be men (andres) who will revolt against a state which is destructive of humanity or in which there is no longer a possibility of noble action or of great deeds." (Strauss 209)
When the real men revolt against too much peace, progress, and prosperity, what will be their program? Strauss: "They may be forced into a mere negation of the universal and homogeneous state, into a negation not enlightened by any positive goal, into a nihilistic negation. While perhaps doomed to failure, that nihilist revolution may be the only great and noble deed that is possible once the universal and homogeneous state has become inevitable. But no one can know whether it will fail or succeed. (Strauss 209, emphasis added)
What can be understood by nihilistic negation and nihilist revolution? In the nineteenth century, nihilism was an ideology of terrorism; the crazed bomb-throwers who assassinated statesmen and rulers across Europe and America (including President McKinley) were atheists, anarchists and nihilists. In the twentieth century, the nihilist revolution was synonymous with some of the most extreme factions of fascism and Nazis. "Long live death!" was a slogan of some of them. With these lines, Strauss has opened the door to fascism, murder, mayhem, war, genocide, and most emphatically to terrorism. And he is not shy about spelling this out.
LEO STRAUSS: BACK TO THE STONE AGE
What will the nihilist revolution look like? Strauss writes: "Someone may object that the successful revolt against the universal and homogeneous state could have no other effect than that the identical historical process which led from the primitive horde to the final state will be repeated." (Strauss 209, emphasis added) The primitive horde or primal horde refers to the human communities of the Paleolithic hunting and gathering societies, to the foragers and cave people of the Old Stone Age. Strauss is endorsing a nihilistic revolt that will have the effect of destroying as much as 10,000 years of progress in civilization, and in hurling humanity back to its wretched predicament in the Paleolithic. Here Strauss finds a momentary common ground with Rousseau, who also had a liking for the Paleolithic; here we are close to the ideas which animated the reign of terror in the French Revolution.
Strauss comes as a Job's comforter to those who have been thrown back into the Old Stone Age: "But would such a repetition of the process -- a new lease on life for man and humanity -- not be preferable to the indefinite continuation of the inhuman end? Do we not enjoy every spring although we know the cycle of the seasons, although we know that winter will come again?" (Strauss 209) Springtime for Leo Strauss has thus acquired the idiosyncratic meaning of a return to the horrors of the Old Stone Age.
Short of turning back the clock to the Paleolithic, Strauss sees one promising possibility latent in Kojeve's universal homogeneous state. This concerns the opportunity for political violence, yet another form of terrorism: "Kojeve does seem to leave an outlet for action in the universal and homogeneous state. In that state the risk of violent death is still involved in the struggle for political leadership .... But the opportunity for action can exist only for a tiny minority. And besides, is this not a hideous prospect: a state in which the last refuge of man's humanity is political assassination in the particularly sordid form of the palace revolution?" (Strauss 209) Such sporadic and limited violence is not enough for Strauss.
Marx and Engels had written about the realm of freedom which would result from higher stages of economic development in the form of a communist utopia. Strauss transforms their communist slogan into an invective against middle class progress and middle class values in general when he concludes this passage with the call: "Warriors and workers of all countries, unite, while there is still time, to prevent the coming of the 'realm of freedom.' Defend with might and main, if it needs to be defended, the 'realm of necessity."' (Strauss 209) Putting aside the superficial polemic against communist utopia, Strauss's goal here is to argue that peace, progress, and prosperity are destructive to oligarchy, and anything must be preferred to such an outcome.
Here we have a blanket endorsement of forms of violence and mayhem, including terrorism and war, in doses large enough to send world civilization back to the Stone Age. This implies genocide on a scale far beyond Hitler, Stalin, and Mao. Today's world population is about 6.25 billion, and barely subsists on the basis of realized technological and industrial progress. But under hunting and gathering conditions, the demographic carrying capacity of the earth would be reduced to 25-50 million. If implemented today, Strauss's program for dismantling the universal homogeneous state would mean a genocide of something approaching 6 billion victims, two whole orders of magnitude beyond Hitler.
And even this must be put into perspective. Strauss notoriously feared to write what he really believed; the public could never face the full truth of his doctrines. Therefore, what we find written in On Tyranny is very likely a somewhat diluted view of his real views. So if Strauss lite, the exoteric version that he felt comfortable publishing at the height of his career, spells up to 6 billion victims, God save us from the full fury of Strauss's esoteric version as it may be transmitted among the neocons infesting and controlling the United States government under the Bush regime.
The most urgent anti-terrorist measure of them all would thus appear to be a purge of neocons from all branches of government (including the Carl Schmitt disciples Scalia, Rehnquist, and Thomas on the Supreme Court), and a general quarantine of neocons as what they really are, neo-fascists and neo-Nazis.
-- 9/11 Synthetic Terror Made in USA, by Webster Griffin Tarpley