
WE WILL NOT BE CHILLED!
MIKE'S VODKA [Mike Masnick of TechDirt]
by Tara Carreon
January 30, 2017

YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.







"At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system. The fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users' needs."
— Crocker, David. Framework and Function of the "MS" Personal Message System. Santa Monica, CA: RAND Corporation, December 1977.
Since the system is to be used for communication which is exemplified in older and heavily-exercised technology, it is assumed that users have an extensive conceptual model of the communication domain. It is further assumed that a system which performs in ways which deviate from that model will be viewed as "idiosyncratic" and impeding the efforts of the user. Problems occurring during this sort of interaction can be expected to be as irritating as having a pen which leaks or a typewriter with keys that jam. Therefore, a major design goal for MS is to provide an integrated set of necessary and sufficient functions which conform to the target user's cognitive model of a regular office-memo system. At this stage, no attempt is being made to emulate a full-scale inter-organization mail system....
The level of the MS project effort has also had a major effect upon the system's design. To construct a fully-detailed and monolithic message processing environment requires a much larger effort than has been possible with MS. In addition, the fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to users' needs. Consequently, important segments of a full message environment have received little or no attention and decisions have been made with the expectation that other Unix capabilities will be used to augment MS. For example, MS has fairly primitive data-base management (i.e., filing and cataloging) facilities and message folders have been implemented in a way which allows them to be modified by programs, such as text editors, which access them directly, rather than through the message system.
-- Framework and Functions of the "MS" Personal Message System: A Report prepared for Defense Advanced Research Projects Agency, by David H. Crocker
“One day, electronic mail, like Edison’s bulb, may also permeate and pervade our lives. It’s practical applications are unlimited. Not only is mail sent electronically, as many telexes and teletypes are capable of doing, but it offers a computational service that automates a secretary’s or file clerk’s work of writing a memorandum, document or letter, editing, filing, and retrieving. If electronic mail systems become a reality, they will surely create different patterns of communication, attitudes, and styles. Volumes of written work, for example, shall become obsolete.”
-- V.A. Shiva Ayyadurai, 1981


YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.



"At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system [p.4]…. The fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users' needs. [p.7]”
— Crocker, David. Framework and Function of the "MS" Personal Message System. Santa Monica, CA: RAND Corporation, December 1977.
Since the system is to be used for communication which is exemplified in older and heavily-exercised technology, it is assumed that users have an extensive conceptual model of the communication domain. It is further assumed that a system which performs in ways which deviate from that model will be viewed as "idiosyncratic" and impeding the efforts of the user. Problems occurring during this sort of interaction can be expected to be as irritating as having a pen which leaks or a typewriter with keys that jam. Therefore, a major design goal for MS is to provide an integrated set of necessary and sufficient functions which conform to the target user's cognitive model of a regular office-memo system. At this stage, no attempt is being made to emulate a full-scale inter-organization mail system....
The level of the MS project effort has also had a major effect upon the system's design. To construct a fully-detailed and monolithic message processing environment requires a much larger effort than has been possible with MS. In addition, the fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to users' needs. Consequently, important segments of a full message environment have received little or no attention and decisions have been made with the expectation that other Unix capabilities will be used to augment MS. For example, MS has fairly primitive data-base management (i.e., filing and cataloging) facilities and message folders have been implemented in a way which allows them to be modified by programs, such as text editors, which access them directly, rather than through the message system.
-- Framework and Functions of the "MS" Personal Message System: A Report prepared for Defense Advanced Research Projects Agency, by David H. Crocker



YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.

TABLE 1
The Parts and Detailed Description of the Interoffice Mail System at UMDNJ (1978).
INBOX
This was the physical Inbox where a secretary received incoming documents. It was usually made of wood, metal or plastic. The courier or “office boy” or “mailroom clerk” would deliver postal mail or interoffice memos into this Inbox. Deliveries into the Inbox were done at least twice per day. Sometimes, urgent messages were delivered on an ad hoc basis into the Inbox.
OUTBOX
This was a physical box made of metal, wood, or plastic, where outgoing postal mail or interoffice memos, which were composed, edited, an placed in an envelope, and addressed to the recipient, were made available for pickup and delivery to its recipients. A courier or “office boy” or “mailroom clerk” would come and pick up the items from the Outbox regularly, at least twice per day.
DRAFTS
This was a physical box made of metal, wood, or plastic to hold drafts of memos or letters, which were in the midst of being reviewed and edited. Typically, a secretary would write the memo and put in the Drafts box for review. A superior would then pickup, review and provide “red-line” feedback on the memo or letter, and place back into Drafts box. The secretary would retrieve the edited document, make changes, and place the edited document back in the Drafts box. After the superior gave instructions, the memo or document would be deemed as completed; the secretary would then place the memo in an envelope, and place it in the Outbox for pick up.
FOLDERS
Memos, documents and files were archived and organized in metal cabinets containing metal drawers. Within each drawer, one could organize, categorize and these items in manila folders within each drawer.
TYPEWRITER
A Typewriter was an instrument that allowed a person to create a Memo. It consisted of mechanical components corresponding to all the alphabets in the English language plus the 10 digits of the number system, as well as a number of other special characters. The Typewriter required paper and ink ribbon to convert strokes on the keyboard into letters on the paper. There were many styles of Typewriters, mechanical and later electrical.
MEMO
This was typically a piece of 8 1/2 by 11-inch piece of BOND paper. The top of the Memo had the words “++++++ MEMORANDUM ++++++” written on it and centered. Below, there were the following areas: “To:”, “From:”, “Date:”, “Subject:”, “Body:”, “Cc:”, “Bcc:” (only for view in the sender’s original), and another section with “Encl.:”, if Attachment(s) were included. After the “Subject:”, there was typically a horizontal black line, after which the “Body:” of the memo appeared. Below the “Body:” were the names of people on “Cc:” list, and then the “Encl.:” list, listing the various Attachments.
ATTACHMENTS
A memo could have Attachments or enclosures such as another file folder, another document, a drawing or a photograph, or even a parcel.
CARBON COPIES
Carbon copies were copies of a Memo created by the secretary, who would typically place dark blue carbon paper between two Bond pieces of white paper and roll them into the typewriter, to create the copies. The Bond paper on top was the original, the paper below, was the “Carbon Copy” or “Cc:”. Sometimes, several Carbons were used, and sometimes if the “Cc:” list was too long, the original would be mimeographed on a mimeograph machine. Then, the original “To:” recipient would get the original, the top copy, and each person on the CC list would get copies. This got more complicated if there were multiple recipients in the “To:” field, or a Group in the “To:” field.
BLIND CARBON COPIES
Blind Carbon Copies enabled a secretary to send a Carbon Copy of a Memo to some people, that others on the “To:” and “Cc:” lists were purposely made to unaware, or “blind” except to the secretary who authored the Memo. The “Bcc:” list, in the header of the Memo, was kept by the sender/secretary, only, and others who got Carbon copies, those on the “Cc:” list, did not see e.g. they were “blind” to those receiving the Bcc’s. So only the sender knew who was on the Bcc list.
REGISTERED MEMO
In the office environment of the medical school and hospital at UMDNJ, this was a very important feature, because certain Memos had to be acknowledged as received. A Memo could be flagged as a “Registered Memo,” this would mean that it was treated differently. The delivery person would put it in a different color envelope and ensure that recipient signed a Return Receipt, before it was put into the Inbox. This would assure the sender that the recipient got the Memo.
RETURN RECEIPT
This was a formal receipt that a delivery person would make sure got signed by the recipient who had been sent a Registered Memo. This Return Receipt would then have to get sent back to the original sender.
ENVELOPE
The interoffice envelope was typically a bit larger than an 8 1/2 by 11-inch paper, and was normally gray or yellow in color. The envelope had a red string on the outside so it could be secured for ease of opening and reuse. The outside of the envelope provided columns and rows on which the sender and the recipient could be listed. After a recipient received the envelope, they could recycle the envelope by crossing out the previous sender and recipient and using the blank rows to write the new sender and recipient, name and address.
ADDRESS BOOK
Every office had an Address Book, which listed each person’s first and last names, location, Group affiliation (e.g. surgery, finance, pharmacology), room number and phone number. The Address Book was the cornerstone of each offices’ contact list.
GROUPS
A Group was listed next to someone’s name in the Address Book. Individuals could belong to different Groups. Groups included Surgery, Pharmacology, ICU, IT, etc. One nuance was that the Group names may be the same, but the Group was distinct based on the campus location. For example, the Pharmacology Group at one location may have different people, than the Pharmacology Group at another location. Each location had different people in different Groups.
TRASH BUCKET
A Trash Bucket was typically next to a secretary’s desk on the floor. The bucket was made of either plastic or metal, and was the location of where trash, such as old papers, garbage were deposited.
COMPOSING MEMO
Composing a Memo was done by the action of taking a blank piece of white Bond paper and placing it in the Typewriter. Sometimes, if errors were made during time, a white liquid substance in a small bottle jar, colloquially called “whiteout was used to erase mistakes, and then the typing was done over the whited out area.
SENDING MEMO TO INDIVIDUAL
Memo to an individual meant that the “To:” field had only the name of only one recipient.
SCANNING MAIL
Scanning mail was the process of quickly reading the Envelope in the Inbox, opening the Envelope and quickly reading the top portion of a Memo, such as the “From:”, “Subject:”, lines to get a quick idea whether to read the Memo immediately, discard it into the Trash Bucket to read first, to put for later review, or sometimes to discard altogether e.g. junk mail.
FORWARDING (OR REDISTRIBUTION)
A person receiving and reviewing an incoming Memo in the Inbox could Forward or Re-Distribute the Memo to others. Forwarding literally involved adding a list of other recipients who to review the Memo. This Forward list was sometimes just paper-clipped on the received Memo, and as the forwarded recipients read the Memo, they checked off their name on the paper-clipped list, and passed it on to the next recipient, who had not yet read the Memo.
FORWARDING WITH RETURN RECEIPT REQUESTED (OR REGISTERED MEMO)
This was an important feature to ensure receipt of a forwarded Memo by the recipient. Sometimes, an important Memo, say from a Director, would be received by a Manager, and that Manager wanted to ensure that certain employees in his group received the Memo. Forwarding with Return Receipt enabled the Manager to know exactly when and who got the Memo and who did not get the Memo. Prior to someone receiving the Memo in their Inbox, the delivery person, would not place the Envelope containing the Memo, it in their Inbox, until the recipient, signed the Return Receipt. The Return Receipts from each employee was sent back to the Manager, and thereby the Manager could the number of Return Receipts and know how many actually received the Memo.
EDITING
A memo sometimes would be edited after it was composed. Editing could be iterative based on the feedback received. Editing typically involved the use of whiteout or sometimes starting with new blank piece of paper and retyping the original Memo with the corrections. Editing relied on the use of the Drafts box, as this box served as the point of interaction between the secretary and her superior.
REPLYING
Sometimes instead of writing a new Memo, an individual Replied to a Memo received in the Inbox. When they replied to the Memo, they could either simply send the response Memo or attach the response Memo to the original Memo sent from the sender as an Attachment for the originating sender’s reference.
BROADCAST MEMO
Sometimes a Memo would need to be broadcasted, or sent, to multiple recipients, sometimes hundreds, not just one individual. This involved listing multiple names of recipients in the “To:” field. The original Memo was created with the listing of all people’s names on the “To:” field. Then that original Memo was copied using the carbon paper to copy, if the list was small, or the original Memo was simply mimeographed. Then each copy was stuffed in an Envelope and placed in the Outbox.
SENDING MEMO TO GROUP
In a large organization, within and across facilities, there were different departments such as Pharmacology, Finance, Administration, Surgery, etc., and one may want to send a Memo to a department or Group. A Group involved a listing of many recipients. However, in the “To:” field only the name of the Group would appear. The secretary would then have to look up in the Address Book and print mailing labels for each individual in that Group, and send a copy of the Memo to each recipient; alternatively, sometimes only one copy of the Group Memo was sent to on address, and the recipient, the secretary or administrator of the Group, on the other end, would make copies of the Memo, and distribute it to members of the Group.
DELETING
Sometimes a memo would be thrown into the Trash Bucket for disposal.
PURGING
The contents of Trash Bucket, by request, would be collected and be destroyed.
UPDATING ADDRESS BOOK
Address Books were updated as employees came and left the organization. New people were added, and those who had left were removed. Sometimes a circular was sent out which was the update to the existing Address Book, and one would have to manually insert the changes in an existing Address Book.
PRIORITIZATION
When mail was left in the Inbox, it sometimes was sorted based on some priority, and marked, such as High, Medium or Low by the secretary. And some secretaries, had file folders, for sorting these three categories of Memos.
ARCHIVING
Not all Memos were discarded after they were read. Some Memos were to be kept for storage, and were often put into an archive file cabinet and organized for long–term record keeping.
UNDELIVERABLE NOTIFICATION
Sometimes a Memo could not be delivered even after many Retries. In this case, the delivery person would take the Memo back to the sender with a note on it saying “Undeliverable”.
RETRIES
All mail had to be delivered, or a real effort was made to keep trying to deliver it before being deemed Undeliverable. This meant a policy of “retries” as many as 3 to 5 times, before the attempts were stopped. The number of Retries was a policy decision of the organization.
SECURING DELIVERY
All mail had to be securely delivered. This meant that only the designated recipient had to receive it. Typically this was ensured, as the delivery person knew who was who and knew the secretaries. Moreover, Memos were put in an individual sealed envelope, with a string closure or taped, so they could not be easily opened during transit.
TRANSPORTING
All mail needed to be transported. There were many ways of Transporting. The delivery person could physically pick up the mail and deliver from local office to office, on foot. Another forms of transporting were using pneumatic tubes, in which the Envelope was placed. The pneumatic tubes were sent on a system of train-track-like rails, form office to office. Mail among different buildings and campuses was transported by cars or trucks.
SORTING
Different locations had mail Sorting facilities, where the mail would come in, be sorted by groups, departments, locations, zip code, office numbers, so the delivery was easier. Within each office, the secretary would also perform sorting operations by a memo’s priority, source, etc.
TABLE 2
The Parts of Email, the First Email System as Implemented in the Computer Program Invented by V.A. Shiva Ayyadurai at UMDNJ (1978)
Interoffice Mail System Parts in the First Email System
Inbox
All Fields of Interoffice MemoTo:
From:
Subject: (70 chars length)
Date:
Body:
Cc:
Bcc:
Sending Memo to Individual
Saving a Memo as a Draft
Scanning Mail
Forwarding (or Redistribution)
Forwarding with RETURN RECEIPT (or registered memo)
Composing Memo
Drafts
Editing
Outbox
Replying
Broadcast Memo
Sending Memo to Group
Deleting
Purging
Address Book
Updating Address Book
Searching the Address BookBy Group
By User Name (short name)
By Last Name
By Zipnode (node or location)
Prioritization
Archiving
Carbon Copies
Blind Carbon Copies
Groups
Registered Memo
Return Receipt
Undeliverable Notification
Retries
Secure Delivery – Using username and password
AttachmentsAttaching to a memo
Creating Attachments from scratch
Saving attachments
Attachment editor
Transmission of memo
Multi-Level User Access – User, Manager, Postmaster, System Administrator
Sorting
Memo Formatting – Formatting functions to make sure that a memo on the screen when printed looked akin to the typewritten memo.
PrintingPrint all mail
Print selected memos
Print only the “envelopes”, To, From, Subject, Date
Formatted printing --- memo looked like typewritten one
Exporting of MailExport a single memo to a file
Export a set of memos to a file
Group Management --- Postmaster/Administrator LevelCreating Groups
Deleting Groups
Placing User in a Group
Deleting User from a Group
Displaying Groups
Restricting Group Access --- Particular users could send to certain groups. E.g. Only Postmaster could send to “ALL” for global broadcast.
Postmaster & Systems Administrator FunctionsReports on mail usage by user
Deleting aged mail
Shutdown of the entire system
Startup of the entire system
Deleting Users
Adding Users
Adding a “Zipnode”, new network
Deleting a Zipnode
Disabling a User from logging in to the user interface
Direct starting of mail transmission
Integrated System ComponentsEasy-To-Use User Interface
Word-processor
Integrated Attachment Editor
Relational Database Engine
Modular Inter-Process Communication Protocol
Print Manager for Formatted Printing
Systems Administrator Console
Post Master Console


Systems and Software Consortium, Inc. (SSCI) is the new name of the Software Productivity Consortium, SSCI President and CEO Dr. Jim Kane announced today. SSCI is a non-profit consortium where leading aerospace, defense, IT, financial industry, educational and government organizations collaborate on the challenges faced in building critical systems. Coupled with its new identity, the Consortium also launched a new website (http://www.systemsandsoftware.org) to better inform its members, employees and the public about the evolving, dynamic and critical mission of SSCI.
SSCI President and CEO Dr. Jim Kane said, "Our focus is clearly on our members' needs. We have realigned our current offerings and are investing more heavily in new solutions that help members manage risk, advance the business value of their systems engineering activities, and drive business performance."
SSCI solutions are now focused on delivering value in three key areas:
* Value-driven process improvement, where SSCI's unique expertise in systems and software process improvement helps members implement high- maturity, measurable processes to increase quality and productivity
while reducing cycle time.
* Lifecycle strategies for complex systems, including minimizing risk, designing and validating architectures, defining system requirements and interfaces, implementing team approaches, and improving mission assurance.
* Integrating systems and software engineering through proven engineering methods for agile, secure systems development, effective project management, in-depth measurement and analysis, and automated testing and verification.
These solutions reflect an increased emphasis on serving members' needs in complex systems and software development.
Dr. Kane added, "Part of the challenge we face is keeping our members up to date and aware of industry changes and accompanying solutions developed through the Consortium. Our new name and website help us better serve our
members, and convey our core focus more efficiently."
SSCI will continue in its successful collaborative assistance through delivering software process expertise, much like in past contributions with Consortium members in key DoD programs like the DD(X) next generation surface combatant ship and the F-35 Joint Strike Fighter.
About the Systems and Software Consortium, Inc. (SSCI)
SSCI is a nonprofit partnership of the nation's leading systems integrators and federal government contractors, as well as selected government affiliates, exclusively focused on helping its members improve the business performance of their systems and software programs. SSCI delivers value by improving systems and software engineering tools and methods that members can apply to their programs resulting in better performance and greater efficiencies. The Consortium also offers members a trusted environment in which to collaborate on common problems and jointly invest in solution development. Current industry members include, BAE Systems, Boeing, Citigroup, CSC, EDS, General Dynamics, Lockheed Martin, Northrop Grumman, Raytheon, Unisys, UTC, and others. For more information see
http://www.systemsandsoftware.org.
-- Systems and Software Consortium, Inc. (SSCI) is New Name for SPC. Name and Website Reflect Expanding Focus on Member Needs, by Systems and Software Consortium, Inc.
"At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system [p.4]…. The fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users' needs. [p.7]”
— Crocker, David. Framework and Function of the "MS" Personal Message System. Santa Monica, CA: RAND Corporation, December 1977.
Since the system is to be used for communication which is exemplified in older and heavily-exercised technology, it is assumed that users have an extensive conceptual model of the communication domain. It is further assumed that a system which performs in ways which deviate from that model will be viewed as "idiosyncratic" and impeding the efforts of the user. Problems occurring during this sort of interaction can be expected to be as irritating as having a pen which leaks or a typewriter with keys that jam. Therefore, a major design goal for MS is to provide an integrated set of necessary and sufficient functions which conform to the target user's cognitive model of a regular office-memo system. At this stage, no attempt is being made to emulate a full-scale inter-organization mail system....
The level of the MS project effort has also had a major effect upon the system's design. To construct a fully-detailed and monolithic message processing environment requires a much larger effort than has been possible with MS. In addition, the fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to users' needs. Consequently, important segments of a full message environment have received little or no attention and decisions have been made with the expectation that other Unix capabilities will be used to augment MS. For example, MS has fairly primitive data-base management (i.e., filing and cataloging) facilities and message folders have been implemented in a way which allows them to be modified by programs, such as text editors, which access them directly, rather than through the message system.
-- Framework and Functions of the "MS" Personal Message System: A Report prepared for Defense Advanced Research Projects Agency, by David H. Crocker

YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.
Myth #1: “Email was created on the ARPANET”
Myth #2: “Ray Tomlinson invented ‘email’ and sent the first ‘email’”
Myth #3: “The ‘@’ symbol equals the invention of ‘email’”
Myth #4: “RFCs demonstrate ‘email’ existed prior to 1978”
Myth #5: “CTSS, developed in 1960s, is ‘email’
“Given the term email was not used prior to 1978, and there was no intention to emulate ‘… a full-scale, inter-organizational mail system,” as late as December 1977 [by the ARPANET], there is no ‘controversy’ here, except the one created by industry insiders, who have a vested interest.”
-- (Wired, Who Invented Email, Just Ask…Noam Chomsky, June 6, 2012)
“A set of different elements so connected or related as to perform a unique function not performable by the elements alone.”
"At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system [p.4]…. The fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users' needs. [p.7]”
— Crocker, David. Framework and Function of the "MS" Personal Message System. Santa Monica, CA: RAND Corporation, December 1977.
Since the system is to be used for communication which is exemplified in older and heavily-exercised technology, it is assumed that users have an extensive conceptual model of the communication domain. It is further assumed that a system which performs in ways which deviate from that model will be viewed as "idiosyncratic" and impeding the efforts of the user. Problems occurring during this sort of interaction can be expected to be as irritating as having a pen which leaks or a typewriter with keys that jam. Therefore, a major design goal for MS is to provide an integrated set of necessary and sufficient functions which conform to the target user's cognitive model of a regular office-memo system. At this stage, no attempt is being made to emulate a full-scale inter-organization mail system....
The level of the MS project effort has also had a major effect upon the system's design. To construct a fully-detailed and monolithic message processing environment requires a much larger effort than has been possible with MS. In addition, the fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to users' needs. Consequently, important segments of a full message environment have received little or no attention and decisions have been made with the expectation that other Unix capabilities will be used to augment MS. For example, MS has fairly primitive data-base management (i.e., filing and cataloging) facilities and message folders have been implemented in a way which allows them to be modified by programs, such as text editors, which access them directly, rather than through the message system.
-- Framework and Functions of the "MS" Personal Message System: A Report prepared for Defense Advanced Research Projects Agency, by David H. Crocker



“The very simple systems (SNDMSG, RD, and READMAIL) did not integrate the reading and creation functions, had different user interfaces, and did not provide sufficient functionality for simple message processing.”—Vittal, John. MSG: A Simple Message System. Cambridge, MA: North-Holland Publishing Company, 1981.
“I was making improvements to the local inter-user mail program called SNDMSG. The missing piece was that the experimental CPYNET protocol had no provision for appending to a file; it could just send and receive files. Adding the missing piece was a no-brainer—just a minor addition to the protocol.”—Tomlinson, Ray, retrieved April 7, 2012.
http://openmap.bbn.com/~tomlinso/ray/fi ... frame.html
“Because the ‘@’ was a line kill character in Multics, sending mail from Multics to other hosts used the control argument -at instead.”—Van Vleck, Tom. History of Electronic Mail, http://www.multicians.org/thvv/mail-history.html, April 7, 2012.
“[T]he BBN guys - who always seemed to get to write the histories and hence always seemed to have claimed to have invented everything, anyway, perhaps because BBN was the only "for-profit" to furnish key members of the original Network Working Group.”—Padlipsky, M.A., ARPANET contributor and author of more than 20 RFC specifications), “And they argued all night….”,
http://archive.is/dx2TK
“[E]mail underpinnings were further cemented in 1977's RFC 733, a foundational document of what became the internet itself.”
“This specification is intended strictly as a definition of what is to be passed between hosts on the ARPANET. It is not intended to dictate either features which systems on the Network are expected to support, or user interfaces to message creating or reading programs.”— http://tools.ietf.org/rfc/rfc733.txt
“The proposed uses [of MAIL] were communication from ‘the system’ to users, informing them that files had been backed up, communication to the authors of commands with criticisms, and communication from command authors to the CTSS manual editor.” -http://www.multicians.org/thvv/mail-history.html, retrieved April 18th, 2012

YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.

Massachusetts Institute of Technology
TECHTALK
September 2, 1981
Volume 26, Number 5
The Class of 1985 arrives to meet the Institute
by Joanne Miller
Staff Writer
Some 1,040 strong, the Class of 1985 arrived at MIT last week to hear a welcoming greeting and some words of advice from President Paul E. Gray at the Freshman Picnic in Killian Court.
"It is a happy moment as the cycle of the year begins," he said to the assembled freshmen, their advisors and associate advisors. He noted that it was the first time so many of the class would be together in one place, something that won't happen again until they gather there nearly four years hence to receive their degrees.
He told the freshmen not to overcommit themselves in narrow academic pursuits, to take initiative in creating individual opportunities for themselves and not to lose sleep over academic survival.
Who are these freshmen? Well, for one thing, 258 -- just about 25 percent -- of them are freshwomen, the largest number ever. The freshmen come from 45 states -- Alaska, Idaho, Nevada, Iowa and South Dakota are unrepresented this year -- and 26 foreign countries.
They were selected from 5,458 applicants, also the largest number ever. Ninety per cent of them were in the top tenth of their high school classes, in schools that rank, and more than half of them enter with some college credit already behind them.
They are accomplished in a variety of other ways as well. One designed an electronic mail system now being used at the New Jersey College of Medicine and Dentistry; another designed and built solar panels now in use at his high school; a third designed a nutrition program for high school wrestlers, and a fourth owns a gasohol plant.
There are, as usual, many musical talents, including a young woman who has played first violin with the Chicago Symphony Orchestra, a freshman who has sung with no fewer than five school and community choirs, one who is a dancer and choreographer for Chinese opera, and one who is a leader of a harmonica band.
Among their individual pursuits they list: toymaking, marquetry, rare bird breeding, filmmaking, fly-tying and puppetry. There is also a sheep breeder, a horse trainer and a pilot with the Civil Air Patrol.
They have also taken an active part in community service. One organized a cancer walkathon that raised $32,000; another built a haunted house for an annual community project. One is a volunteer firefighter; another is an amateur magician who performed at an international children's festival.
Sports play an important part in many of their lives. One freshwoman organized a women's soccer team. Two are skaters of note, one a silver medallist in US Figure Skating Association competition and one who played for the Canadian National Hockey Team. There is a freshman who has coached a women's football team and a freshwoman who has managed a wrestling team.
In sum, the Class of 1985, like those that preceded it, arrives with a wealth of talents and abilities that will contribute much to the richness of our community.
“That to secure these rights [of life, liberty, and the pursuit of happiness] Governments are instituted among men … that whenever any form of Government becomes destructive of these ends, it is the right of the people to alter or abolish it ….”

YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.
“At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system [p.4]…. The fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users' needs [p.7].”
—Crocker, David. Framework and Function of the “MS” Personal Message System. Santa Monica, CA: RAND Corporation, December 1977.
Since the system is to be used for communication which is exemplified in older and heavily-exercised technology, it is assumed that users have an extensive conceptual model of the communication domain. It is further assumed that a system which performs in ways which deviate from that model will be viewed as "idiosyncratic" and impeding the efforts of the user. Problems occurring during this sort of interaction can be expected to be as irritating as having a pen which leaks or a typewriter with keys that jam. Therefore, a major design goal for MS is to provide an integrated set of necessary and sufficient functions which conform to the target user's cognitive model of a regular office-memo system. At this stage, no attempt is being made to emulate a full-scale inter-organization mail system....
The level of the MS project effort has also had a major effect upon the system's design. To construct a fully-detailed and monolithic message processing environment requires a much larger effort than has been possible with MS. In addition, the fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to users' needs. Consequently, important segments of a full message environment have received little or no attention and decisions have been made with the expectation that other Unix capabilities will be used to augment MS. For example, MS has fairly primitive data-base management (i.e., filing and cataloging) facilities and message folders have been implemented in a way which allows them to be modified by programs, such as text editors, which access them directly, rather than through the message system.
-- Framework and Functions of the "MS" Personal Message System: A Report prepared for Defense Advanced Research Projects Agency, by David H. Crocker
In 1978, Dr. Ayyadurai created a system of computer programs, which were the first full-scale emulation of the interoffice, inter-organizational mail system;
Shiva named his system “email”;
The system, email, which he solely created, contained all the features that are strikingly similar, if not exact, to the features and functions in modern email programs such as Gmail, Hotmail, Yahoo, etc.; and,
Prior to 1978, there was no intention of other electronic messaging developers, dating as far back to the Morse Code telegraph of the 1800s, to develop email.
In 1978, when Shiva created email, there was no mechanism to protect software inventions, through either Copyright or Patent;
In 1980, the Copyright Act of 1976 was amended to become the Computer Software Act of 1980, which allowed software inventors to have their software inventions protected through Copyright. Even then the Supreme Court did not recognize Software Patents;
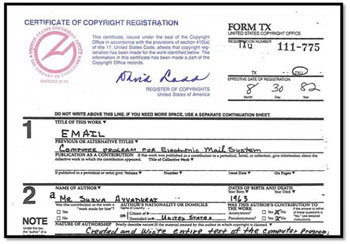
In 1981, Shiva applied for a Copyright to protect his invention of email, which required him to submit copies of portions of his code and User’s Manual to the Library of Congress that made his work publicly accessible; and,
On August 30, 1982, he received official recognition by the U.S. government as the inventor of email, when he was issued the first Copyright for “Email”, “Computer Program for Electronic Mail System”.
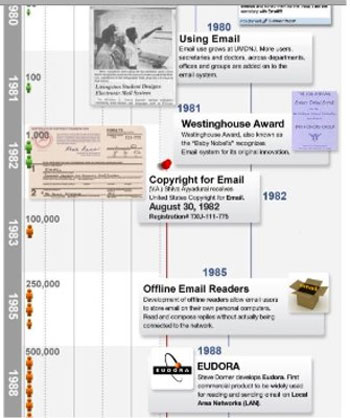
The West Essex Tribune Article of 1980;
The Honors Award letter and Certificate from Westinghouse Science Talent Search Committee in 1981; and,
The acknowledgement of Shiva’s invention of email on the front-page of Tech Talk on September 2, 1981, wherein Shiva was one of three students, among the incoming class of 1,041, who was highlighted.
June 11, 2012 11:10 p.m.
Speech emerged from our need to articulate grievances. At some point, yelling and pushing was no longer enough, and smacking on the head with stones just hurt too damn much, and we had to find a way to talk about it. It began with grunts and growls. Or maybe pleas for mercy. Maybe the first time a voice kept a stone from breaking a head, that was speech. Yes, I think that would be.
But I can’t speak a word that will stop anonymous cybervandals from posting phony Amazon reviews panning my book, giving my girls shit on Twitter, trying to take down my websites, sending me hatemail, signing me up for free email offers, ordering me pizza, sending me bags of poop, certificates of jerkdom, and really, the kindest one, a free package of Attends. It’s at times like these that having a deep understanding of the universe and an abiding trust in the universe’s merciful nature comes in really handy.
But eventually, sanctity wears thin and you start to seethe.
-- The Real Diary of Charles Carreon, by Charles Carreon
“I seem to have stepped into a mess by accident. Last Friday, I read the new Huffington Post articles about your contributions to e-mail. Afterwards, as an experienced Wikipedia editor, I had a look at the "Email" article, and was surprised that you hadn't received credit for your contributions. Since I have had a great deal of experience writing Wikipedia articles, I got right to work and added several suitable additions to provide credit to your contributions. Right away, my edits were deleted, without discussion, not edited to improve them, but just flat-out deleted. This is the kind of behavior an editor encounters when editing an article on the 2nd Amendment, abortion or other extremely hot topics. The response to my edits has included personal attacks, calling me “ignorant”, “reckless” and the like. Although most editors have been less insulting than that, they have generally been aggressive in rapidly deleting my additions.”
(September 2, 2014, experienced Wikipedia Editor)




"The efforts to belittle the innovation of a 14-year-old child should lead to reflection on the larger story of how power is gained, maintained, and expanded, and the need to encourage, not undermine, the capacities for creative inquiry that are widely shared and could flourish, if recognized and given the support they deserve. The angry reaction to the news of his invention of EMAIL and the steps taken to belittle the achievement are most unfortunate. They suggest an effort to dismiss the fact that innovation can take place by anyone, in any place, at any time. And they highlight the need to ensure that innovation must not be monopolized by those with power — power which, incidentally, is substantially a public gift."
— Prof. Noam Chomsky, inventorofemail.com, April 2012
YOU ARE REQUIRED TO READ THE COPYRIGHT NOTICE AT THIS LINK BEFORE YOU READ THE FOLLOWING WORK, THAT IS AVAILABLE SOLELY FOR PRIVATE STUDY, SCHOLARSHIP OR RESEARCH PURSUANT TO 17 U.S.C. SECTION 107 AND 108. IN THE EVENT THAT THE LIBRARY DETERMINES THAT UNLAWFUL COPYING OF THIS WORK HAS OCCURRED, THE LIBRARY HAS THE RIGHT TO BLOCK THE I.P. ADDRESS AT WHICH THE UNLAWFUL COPYING APPEARED TO HAVE OCCURRED. THANK YOU FOR RESPECTING THE RIGHTS OF COPYRIGHT OWNERS.
“Email, upper case, lower case, any case, is the electronic version of the interoffice, inter-organizational mail system, the email we all experience today — and email was invented in 1978 by a 14-year-old working in Newark, NJ. The facts are indisputable.” (Garling, 2012)
-- Professor Noam Chomsky, MIT, Institute Professor & Professor of Linguistics




"At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system [p.4]…. The fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users' needs [p.7].” (Crocker, 1977)
-- Mr. David Crocker ARPANET Researcher, December 1977


“[Email]’s practical applications are unlimited. Not only is mail sent electronically, as many telexes and teletypes are capable of doing, but it offers a computational service that automates a secretary’s or file clerk’s work of writing a memorandum, document or letter, editing, filing, and retrieving. If electronic mail systems become a reality, they will surely create different patterns of communication, attitudes, and styles. Volumes of written work, for example, shall become obsolete.” (Ayyadurai, 1981)
-- V.A. Shiva Ayyadurai in 1981, Livingston High School Thomas Alva Edison/Max McGraw Awards Application


“[T]he[Raytheon/]BBN guys - who always seemed to get to write the histories and hence always seemed to have claimed to have invented everything, anyway, perhaps because BBN was the only "for-profit" to furnish key members of the original Network Working Group.”
-- Mr. M.A. Padlipsky, ARPANET Researcher
“What continue[s] to be deplorable are the childish tantrums of industry insiders who now believe that by creating confusion on the case of ‘email,’ they can distract attention from the facts….Given the term email was not used prior to 1978, and there was no intention to emulate ‘…a full-scale, inter-organizational mail system,” as late as December 1977, there is no controversy here, except the one created by industry insiders, who have a vested interest.”
-- Professor Noam Chomsky, MIT, Institute Professor & Professor of Linguistics
“Under ARPANET several major innovations occurred: email (or electronic mail), the ability to send simple messages to another person across the network,” (Bellis, 2012)
“At this time, no attempt is being made to emulate a full-scale, inter-organizational mail system. p.4” (Crocker, 1977)
“The level of the MS project effort has also had a major effect upon the system’s design. To construct a fully-detailed and monolithic message processing environment requires a much larger effort than has been possible with MS. In addition, the fact that the system is intended for use in various organizational contexts and by users of differing expertise makes it almost impossible to build a system which responds to all users’ needs. p.7” (Crocker, 1977)
“The idea of sending ‘letters’ using [the Compatible Time-Sharing System] was resisted by management, as a waste of resources.” (Van Vleck, 2001)
“The idea of initially sending ‘letters’ using [the Compatible Time-Sharing System] was resisted by management, as a waste of resources.” (Nightingale and Song, 2014b)
BEFORE (a)
Note: Van Vleck clearly states that CTSS management resisted allowing him to create a system for sending "letters" e.g. To, From, Cc, Bcc, etc, but would allow him to create a system for sending/receiving, requests, e.g. text messages.
Here is the Original Text
"The Idea of sending 'letters' using CTSS was resisted by management, as a waste of resources. However, CTSS Operations did need a facility to inform users when a request to retrieve a file from tape had been completed, and we proposed MAIL as a solution for this need."
AFTER (b)
Note: Now, "initially" added -- subtle but a BIG difference.
Here is the Revised Text
"The Idea of sending 'letters' using CTSS was initially resisted by management, as a waste of resources. However, CTSS Operations did need a facility to inform users when a request to retrieve a file from tape had been completed, and we proposed MAIL as a solution for this need."
BEFORE (a)
1971 Ray Tomlinson develops an email application for over the ARPAN ... message had been received Tomlinson chose the "@" sign for email ...
1970 - Monty Python Spam Skit airs
1960s Email developed for time share computers (individuals could me ...
1890s, USPS declared it illegal to deliver paper messages through pneu ...
AFTER (b)
1971 Ray Tomlinson develops an email application for over the ARPAN ... received Tomlinson chose the "@" sign for email addresses.
1970 - Monty Python Spam Skit airs
1965 Noel Morris and Tom Van Vleck invent email
1960s Email developed for time share computers (individuals could me ...
1890s, USPS declared it illegal to deliver paper messages through pneu ...
“Ray Tomlinson invented email in 1971.” ("Ask.com - What's Your Question?", 2012)
“Ray Tomlinson sent the first email.” ("A Brief History of Email in the Federal Government.", 2012)
“Ray Tomlinson is credited with inventing email in 1972. Like many of the Internet inventors, Tomlinson worked for Bolt Beranek and Newman as an ARPANET contractor.” ("History of Internet/Email.", 2012)
“The very simple systems (SNDMSG, RD, and READMAIL) did not integrate the reading and creation functions, had different user interfaces, and did not provide sufficient functionality for simple message processing.” (Vittal, 1981)
“I was making improvements to the local inter-user mail program called SNDMSG. The idea occurred to me that CPYNET could append material to a mailbox file just as readily as SNDMSG could. SNDMSG could easily incorporate the code from CPYNET and direct messages through a network connection to remote mailboxes in addition to appending messages to local mailbox files. The missing piece was that the experimental CPYNET protocol had no provision for appending to a file; it could just send and receive files. Adding the missing piece was a no-brainer—just a minor addition to the protocol.” (Tomlinson, 2012).
“I don't believe Ray Tomlinson invented ‘e-mail.’ And not because of the quibble that we called it netmail originally, though that does offer an excuse to observe that I personally find the term ‘e-mail’ awfully cutesy, and references to ‘sending an e-mail’ syntactic slime. Nor because of the semi-quibble that ‘mail’ had been around intra-Host on several of the Host operating systems since well before anybody realized they were Hosts, though that one has a great deal of abstract ‘historical’ appeal. No, it's because I have a completely clear memory that Ray wasn't even at the FTP meeting where we decided to add mail to the protocol.” (Padlipsky, 2000)
“When [Tomlinson] is remembered at all, it is as the man who picked ‘@’ as the locator symbol in electronic addresses. In truth though, he is the inventor of e-mail, the application that launched the digital information revolution. And yet the breakthrough he made was such a simple evolutionary step that hardly anyone noticed it till later.” (“The Invention of Email,” 1998)
“Because the ‘@’ was a line kill character in Multics, sending mail from Multics to other hosts used the control argument -at instead.” (Van Vleck, 2012)
“Do folks remember that ‘@’ was the Multics line-kill character? We were opposed to Ray Tomlinson's famous (or is it infamous?) selection of @ as the character that separated the user name from the host name…. Early versions … allowed the use of space-a-t-space (i.e., ‘at’) in place of the ‘@’ to accommodate Multics (and the mail composition software I wrote used the syntax -at on the command line)” (Pogran, 2012).
“Early versions of ARPANET email specs allowed the use of space-a-t-space (i.e., " at ") in place of the ‘@’ to accommodate Multics and the mail composition software I wrote used the syntax -at on the command line to begin composing an email….” (Pogran, 2012)
“…email underpinnings were further cemented in 1977's RFC 733, a foundational document of what became the Internet itself.” (Biddle 2012)
“In 1977 these features and others went from best practices to a binding standard in RFC 733.” (Biddle, 2012)
"This specification is intended strictly as a definition of what is to be passed between hosts on the ARPANET. It is NOT intended to dictate either features which systems on the Network are expected to support, or user interfaces to message creating or reading programs."
“Some of RFC #733's features failed to gain adequate acceptance.” (Crocker et al., 1977)
“Prospective users, system designers, and service offering companies often compile lists of potential services [of electronic mail systems]… Nobody claims that these lists are complete, and most often it is admitted freely that these lists represent a first cut synthesis of services offered by other communication facilities. Unfortunately, these lists mostly convey just a number of buzz-words which everybody interprets in his own fashion.” (Shicker, 1981)
“By the mid-1970s, other user-oriented e-mail programs arrived on the scene. Two of the more popular examples were ‘Hermes’ at Bolt, Beranek, and Newman, now BBN—a wholly owned subsidiary of Raytheon — and ‘Laurel,’ which was in use at Xerox PARC.” (Crocker, 2012)
“A client program of Grapevine generally obtains services through code…. The primary clients of Grapevine are various mail interface programs, of which Laurel is most widely used.” (Schroeder, 1984)
“…the Grapevine system was first made available to a limited number of clients during 1980.” (Birrel, 1980)
“… know what if any email systems based on unofficial internet standards were implemented before 1979.” (Tesler 2012)
“In systems like SEND MESSAGE and its successors, such as HERMES, ON-TYME, and COMET, there is no provision for immediate response. A message is sent into a mailbox for later access by the recipient. No automatic filing is provided: any searching of message files requires users to write their own search programs, and to flag those messages they want to retain or erase. The burden is placed on users to manage their own files, and a fairly detailed understanding of programming and file structures is required. Both senders and receivers must learn about 20 commands, and if they misuse them they can jeopardize the entire data structure. Some messages may even be lost in the process.” (Vallee, 1984)
“Dave Farber gave a bit of history of mail systems listing names of all the systems that anybody had ever heard of (see Appendix A)…. It was noted that most of the mail systems were not formal projects (in the sense of explicitly sponsored research), but things that ‘just happened’.” (Postel, 1982b)
MSG started from a set of primitive message processing operations. Several of the commands listed above were not implemented in the initial version of MSG:
Creation: Answer and Forward
Motion: Move
File operations: Write
Marking: Mark and Unmark
User-interface and Profile: Koncise, Verbose, and Zap profile
Miscellaneous: Print date and Comment
It became clear, even before MSG was first publicly released, that the operations of Put and Delete were so commonly used together that a combining operation (Move) should be included in the functionality of the system. This was the first major modification.
COMPARISON WITH OTHER SYSTEMS
Many of the other CBMSs of the time have already been alluded to. The very simple systems (SNDMSG, RD and READMAIL) did not integrate the reading and creation functions, had different user-interfaces, and did not provide sufficient functionality for simple message processing.
On the other hand, two systems came very close to MSG. BANANARD gained acceptance, but seemed to not have the right functionality. The user-interface seemed to be a little too verbose for experienced users. However, it is important to note that some users still prefer to use BANANARD. These tend to be users who view mail rather than respond to it.
However good MSG is, it is not perfect. Its major drawback is that it does not have a directly integrated message creation facility with the same style of user-interface as the rest of MSG. The result is that users are forced to use two separate interfaces for a single conceptual process -- dealing with mail. In addition, the decision to use SNDMSG limits users because it has no way to edit various fields of the message after a specific field has been completely specified, especially address lists.
“Its major drawback is that it does not have a directly integrated message creation facility….” (Vittal, 1981)
“Electronic mail, or email, was introduced at MIT in 1965 and was widely discussed in the press during the 1970s. Tens of thousands of users were swapping messages by 1980.” (Crisman et al., 2012)
The MAIL Command
A new command should be written to allow a user to send a private message to another user which may be delivered at the receiver's convenience. This will be useful for the system to notify a user that some or all of his files have been backed-up. It will also be useful for users to send authors any criticisms.
MAIL LETTER FILE USER1 USER2 USER3 .... MAIL 'ME'
LETTER FILE is the name of a BCD file which contains the message to be sent.
USERn is the designation of the user who is to receive the message. USERn may be a programmer's name or programmer number or the problem-programmer number. It may also be just the problem number if the message is to go to all users of the same problem number.
MAIL ME is the command given by the receiver when he wants the mail to be printed. The files will be left in permanent mode and should be deleted by the receiver at his convenience.
The MAIL command will create or append to the front of a file called MAIL BOX. System messages to the user will be placed in a file called URGENT MAIL. The LOGIN command will notify the user if he has either kind of mail. MAIL ME will always print URGENT MAIL before MAIL BOX.
BOX'. Because of the appending feature of the MAILing process, the command 'DELETE MAIL BOX' should be issued after a message has been PRINTed, to avoid having to run through previous messages to get to the latest one.)
“The proposed uses [of MAIL],” wrote Tom Van Vleck, “were communication from ‘the system’ to users, informing them that files had been backed up, communication to the authors of commands with criticisms, and communication from command authors to the CTSS manual editor.” (Crisman, 1965)
In systems like SEND MESSAGE and its successors, such as HERMES, ON-TYME, and COMET, there is no provision for immediate response. A message is sent into a mailbox for later access by the recipient. No automatic filing is provided: Any searching of message files requires users to write their own search programs, and to flag those messages they want to retain or erase. The burden is placed on users to manage their own files, and a fairly detailed understanding of programming and file structures is required. Both senders and receivers must learn about 20 commands, and if they misuse them they can jeopardize the entire data structure. Some messages may even be lost in the process. These drawbacks are compensated for by the fact that the cost per message is very low.
“… we need a more specific definition that captures the essence of computer based electronic mail as it actually emerged. Here is one that was developed in discussion with email pioneers Ray Tomlinson, Tom Van Vleck and Dave Crocker:
‘Electronic mail is a service provided by computer programs to send unstructured textual messages of about the same length as paper letters from the account of one user to recipients' personal electronic mailboxes, where they are stored for later retrieval.’ ” (‘SIGCIS Blog’, 2012)
Electronic Mail Systems give me some major concern. The use of the word "mail" brings with it a lot of baggage, and most certainly people are going to get some surprises because of this. A conventional letter always presents itself to the reader in the same format as it had when it left the writer. In the electronic situation, unless rigid controls are exercised over the terminals allowed on the system, there is no guarantee that the recipient will see the same lay out at all. Designers tell us that the way text is presented can significantly alter the attitude the reader has towards printed text. In electronic mail this variable is left wide open!
Users of such computer based mail systems are less intrigued by the various internal mechanisms and resource allocation strategies but require exact definitions of the facilities and services that these systems offer. Prospective users, system designers, and service offering companies often compile lists of potential services, e.g., like the list shown in appendix A. Nobody claims that these lists are complete and most often it is admitted freely that these lists represent a first cut synthesis of services offered by other communication facilities (e.g., postal service, telephone, telegraph, telex, etc.).
Unfortunately, these lists mostly convey just a number of buzz-words which everybody interprets in his own fashion. For example, a multitudiness of ...
... sary obstacle. Much confusion still exists about the requirements for effective communications. One person calls "conferencing" what another calls "mail."
'Electronic Mail' is a term that means different things to different people. To one person, electronic mail may represent a technology as old as the telegraph, while to another, it may mean high-powered computers that relay digitized information. Part of the confusion about what electronic mail really is can be traced to how the term is defined. Usually, electronic mail is defined as any process ...
“To ‘invent’ something you have to devise some kind of new technology or capability that had not existed before. A computer program is not invented; it is ‘written’ or ‘developed.’ So, for example, it would make sense to say that Dan Bricklin and Bob Frankston invented the spreadsheet when they wrote Visicalc. It wouldn’t make sense to say that Google invented the web browser when it developed Google Chrome, as many previous browsers existed, or even that it ‘invented the world’s first Google Chrome’ as that is a specific system rather than a technology.” (‘SIGCIS Blog’, 2012).
“The system [created by Ayyadurai] will still be of interest to historians as a representative example of a low-budget, small scale electronic mail system constructed from off-the-shelf components, including the HP/1000’s communications, word processing, and database programs.” (‘SIGCIS Blog’, 2012)
The human factors of communications are still largely ignored. As new companies get into the field, they hire the best programmers they can find to implement message systems. These programmers are often compiler writers or experts in operating systems and have had no experience in dealing with end users. They have operated in a completely different environment, where communications had a much narrower meaning. Some early successes have also had the unfortunate result of freezing the technical reality of the field for too long. Network mail on the ARPANET is a case in point. Introduced in the early 1970s, electronic mail systems have been very successful on the ARPANET, where they served a highly trained community of technical experts. When it came time to design new systems for wider communities, these same technical experts found it very difficult to be creative in ways that differed from what they had first learned.
“The system will still be of interest to historians as a representative example of a low-budget, small scale electronic mail system constructed from off-the-shelf components, including the HP/1000’s communications, word processing, and database programs.” (‘SIGCIS Blog’, 2012).
“Acknowledgements: Thanks to the dozens of people who sent me hundreds of messages after learning that I was working on a response for the Post. Many helped to read and shape earlier drafts. In no particular order: Evan Koblentz, Catherine Lathwell, Peter Meyer, Dave Walden, Debbie Deutsch, Marie Hicks, James Sumner, Ken Pogran, Tom Van Vleck, Dag Spicer, Mark Weber, JoAnne Yates, Murray Turoff, Al Kossow, Ramesh Subramanian, David Alan Grier, Paul McJones, Nathan Ensmenger, David Hemmendinger, Jeffrey Yost, David Moran, Peggy Kidwell, Debbie Douglas, Alex Bochannek, Bill McMillan, Len Shustek, Petri Paju, Elizabeth Finler, Dave Crocker, Ray Tomlinson, Pierre Mounier Kuhn, James P.G. Sterbenz, Ben Barker, Jim Cortada, and Craig Partridge.” (‘SIGCIS Blog’, 2012)
“By 1980, electronic mail systems aimed at the office environments were readily available from companies such as DEC, Wang, and IBM.” (‘SIGCIS Blog’, 2012)
“[Computer-based message systems] are sold to users who have an interest in implementing electronic mail on their current equipment. Not surprising therefore, many of the vendors in this grouping tend to be minicomputer manufacturers such as Data General and Prime. The reason for this is not so much that minicomputer manufacturers have a real interest in electronic mail, but rather have devised messaging systems in an attempt to prevent other firms from selling a system that would run on their hardware. Thus, this type of electronic mail system has evolved as part of a defensive strategy by original equipment manufacturers (OEMs). An excellent example of a product by an OEM is Wang Laboratories Inc.’s Mailway” (Wang Systems Newsletter, 1979)
"...the PARC email software, Laurel, ran on the user’s local computer, was operated with a mouse, and pulled messages from the PARC server to a personal hard drive for storage and filing." (‘SIGCIS Blog’, 2012)
“For years CompuServe users could type “GO EMAIL’ to read their messages….” (Compuserve Information Service User’s Guide, 1983)
This is called interactive video and is the future of the computer networks.
Both The Source and Compuserve (the two largest computer networks) are beginning to tap the wellspring of interactive video. Both began their services by offering electronic mail (called EMAIL on Compuserve and SMAIL on The Source), which meant you were no longer at the mercy of the Postal Service if your addressee was also hooked into the computer revolution.
Quick and easy-to-learn areas allow you to type in a message to anyone else on the network. And, your message is delivered in a few moments, or a couple of hours at most.
SIGs, or Special Interest Groups, is an area that has been pioneered by Compuserve, although The Source is now offering a "Participate" program that is similar. In a SIG, a person leaves a message about that group's interest, or he replied ...
Fig. 8. Taken from the August, 1983 Edition of Popular Mechanics Magazine, pg. 107.
LAST NIGHT WE EXCHANGED LETTERS WITH MOM, THEN HAD A PARTY FOR ELEVEN PEOPLE IN NINE DIFFERENT STATES AND ONLY HAD TO WASH ONE GLASS ...
That's CompuServe, The Personal Communications Network For Every Computer Owner
And it doesn't matter what kind of computer you own. You'll use CompuServe's Electronic Mail system (we call it Email") to compose, edit and send letters to friends or business associates. The system delivers any number of messages to other users anywhere in North America.
CompuServe's multi-channel CB simulator brings distant friends together and gets new friendships started. You can even use a scrambler if you have a secret you don't want to share. Special interest groups meet regularly to trade information on hardware, software and hobbies from photography to cooking and you can sell, swap and post personal notices on the bulletin board.
There's all this and much more on the CompuServe Information Service. All you need is a computer, a modem, and CompuServe. CompuServe connects with almost any type or brand of personal computer or terminal and many communicating word processors. To receive an illustrated guide to CompuServe and learn how you can subscribe, contact or call:
CompuServe
Information Service Division, P.O. Box 20212 5000 Arlington Centre Blvd., Columbus, OH 43220
800-848-8990
In Ohio call 614-457-8650
An H&R Block Company
BYTE January 1983
"Email has no single inventor. There are dozens, maybe hundreds, of people who contributed to significant incremental ‘firsts’ in the development of email as we know it today. Theirs was a collective accomplishment, and theirs is a quiet pride (or at least was until recent press coverage provoked them). Email pioneer Ray Tomlinson has said of email’s invention that, ‘Any single development is stepping on the heels of the previous one and is so closely followed by the next that most advances are obscured. I think that few individuals will be remembered.’” (Crocker, 2012)
"Naturally this was discussed on the ex-BBN list. In my view, this "new guy" [Shiva Ayyadurai] has described something not quite like what the rest of us understand when we say ‘email.’" (‘SIGCIS Blog’, 2012)
Return to A Growing Corpus of Analytical Materials
Users browsing this forum: No registered users and 83 guests